Lateral Thinking: What is Lateral Movement and How Can You Prevent It?
It is not uncommon for organizations to hear the term “Lateral Movement” after an audit or to be told they have a problem with it after a penetration test. But in most cases, there is no insight into what this means for them; and how they can begin to tackle it. In this post we are going to attempt to make Lateral Movement relatable, and highlight how Cymulate can make it achievable, to understand what Lateral Movement looks like in your environment.
Lateral Movement refers to the techniques threat actors use to systematically identify, move between, and compromise assets of value within an organization’s network. We can simplify the idea of the process by relating the activities to physical security; in this case, a thief attempting to burgle a property.
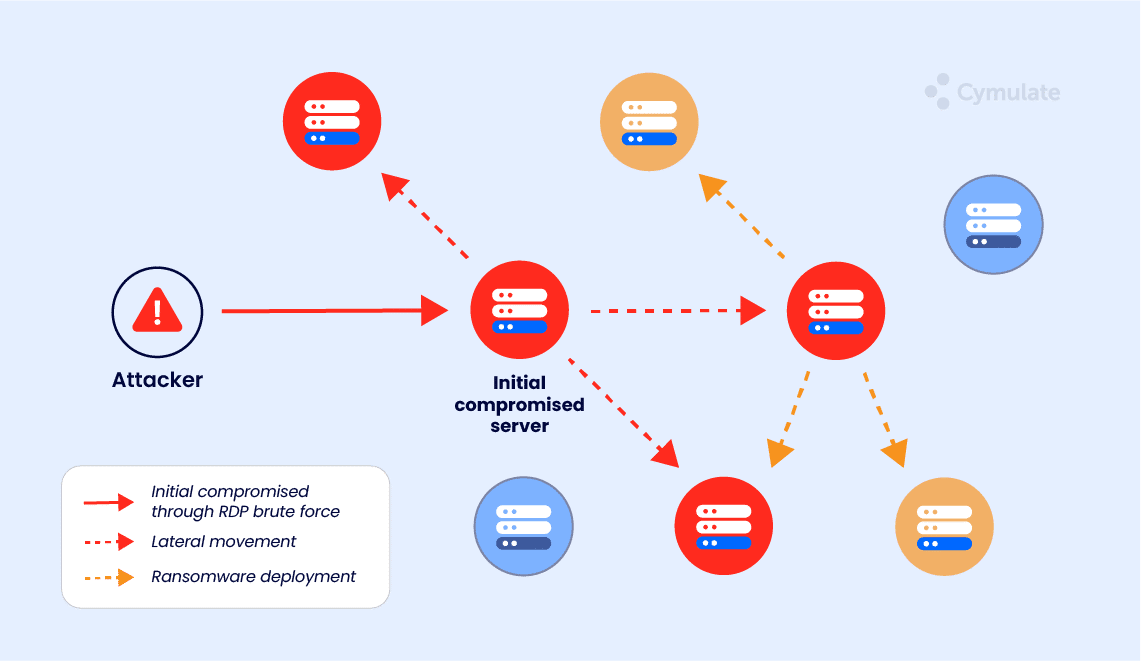
Can an entry point be identified to gain access, an open door, or a window? Is there a key left under the mat?
Once entry is gained, are there any alarms or locks protecting rooms of interest; and how far can we spread throughout the building until we find something of value, or get blocked from entering any more rooms?
Now, as I said it is common for many organizations to hear this term after an annual audit or penetration test; but what does Lateral Movement look like for the company? It is a tricky question to answer and something that does not get clearly articulated due to its complexity. So, let us start by understanding the challenges and then move on to understanding how the Cymulate platform can help.
Challenge 1 – Account and Role Change Automation
In most organizations, there is a fine line between delivering operational support and being able to monitor all user access and activities. An organization’s network and security landscape are continuously changing and subject to configuration drift and “fixes” to keep the lights on so the business can deliver. New employees, role changes, and resignations/terminations result in a barrage of account activity and manual labor which often leads organizations to look to automation to streamline the process of HR operations.
This means that an attacker gaining the ability to either digitally or (in some cases) physically manipulate this automation would give them an unprecedented ability to also manipulate all the outcomes of these operations. Automation to keep the lights on could – inadvertently – kill the lights as payroll, reporting, and other vital operations are suddenly disrupted by false changes to HR data; leading to the ability to move laterally by getting access to roles and responsibilities that shouldn’t be assigned to that account/person.
Challenge 2 – The Ever-Changing IT landscape
Most organizations are on a constant journey to improve network security and transition services to cloud environments; to reduce costs and deliver more for less. Some IT teams find themselves having to maintain and support legacy systems and applications both on-prem and in cloud migrations. Whilst others are subject to mergers and acquisitions and having to support multiple technologies and systems that they have no previous knowledge of – but are now expected to combine into the IT systems or take over and support from the acquired company. To meet deadlines and goals things can be overlooked, default configurations left in place, ports and protocols left open, systems left behind on updates and patching, whilst accounts with privilege are overlooked.
Lateral Movement attacks are often persistent and carried out over a prolonged period to evade detection and blend into the background noise of day-to-day behaviour. If our IT & Security teams are overwhelmed or under resourced how can we expect them to differentiate between legitimate user and account activity quickly and correctly versus something malicious? This is drastically compounded when systems are migrated to cloud platforms without proper preparation and transformation; or systems are merged/taken over during particularly hurried mergers and acquisitions.
Challenge 3 – Operational context
If a device were to be compromised, what would happen? How could that device be compromised in the first case? What is the blast radius and what items (data, additional systems, etc.) of value could be reached? These can be wrapped up in the single question, “Are the security controls I have in place configured and working effectively for my organization right now?”
Lateral Movement attacks leverage the fact that many systems do not report abnormal activity effectively and may not even be able to recognize abnormal activity at all. Remember that many systems can only see their own operations, and as we move toward more interconnected platforms (as opposed to single systems); it becomes much easier for an attacker to leverage this lack of communication to move laterally.
How Can Cymulate help?
Cymulate Continuous Security Validation allows organizations to test their security controls against thousands of simulated attacks and techniques on-demand or on a schedule of their choosing safely, including Lateral Movement simulations.
Unlike traditional testing, it is not bound by scope or timeframe and provides continuous assurance and visibility into the effectiveness of your security controls, even against the latest threats. It’s class-leading UI and rich reporting means that organizations of any size or vertical can quickly and effectively gain instant insight, and identify gaps in their security controls, while receiving actionable insights for full kill-chain mitigation.
The Bigger Picture – More Than Just Lateral Movement
Cymulate’s Endpoint Security Validation challenges your endpoint security controls and identifies whether they are properly configured and tuned to protect you against signature and behavioral attacks.
This module empowers an organization to deploy and run simulations of ransomware, trojans, worms, and viruses in a controlled and safe manner. The endpoint attack simulation ascertains if the security controls are configured properly and are protecting your organization’s critical assets against the latest attack methods used by threat actors – in addition to previous methods that may be used again in the future. This comprehensive testing covers all aspects of endpoint security; including but not limited to behavioral detection, virus detection, and known vulnerabilities.
So, after testing and identifying what can execute and run successfully on the endpoint; we can start to answer, “Would it be possible to execute Lateral Movement from an endpoint; and if so, would it be detected quickly and effectively?”
Some tools are finished at this point, they have served their purpose. But, this is only part of the picture when it comes to Lateral Movement. The next stage is to understand what assets and configurations lay within the organization’s network that could be discovered by, compromised by, and used by something or someone attempting to move laterally (tickets, tokens, credentials, networking and routing, etc.).
Cymulate’s Lateral Movement module allows an organization to safely and continuously test their environment to ascertain what resources are in place that would allow an attacker to move laterally; and what defenses are effective at prohibiting a threat actor from using them.
Cymulate will not be using vulnerabilities or exploits which could cause disruption or destruction of systems or data during testing because we want to enable organizations to test for Lateral Movement safely. This is key to allowing organizations to test their environment without the threat of downtime or disrupting operations. This is where integration with a vulnerability scanner allows Cymulate to identify where weaknesses exist that could have been leveraged; without having to invoke them and risk causing operation downtime and outages.
When it comes to reviewing results you now have three key items to help you understand what Lateral Movement looks like for your organization. Let’s refer to the “thief” scenario (where a thief attempting to break into a building needs specific things to be successful):
The Keys – Tickets, Tokens, Credentials.
Over-Privileged accounts, whether that is a specific user account or a service account. Credentials saved in plain text, browsers, or applications. Whether security controls are going to permit and detect techniques that supply threat actors the keys, including kerberoasting, responder poisoning, password spraying, etc.
Routing, Ports, and Protocols
Are there open ports and protocols in place that can permit Lateral Movement, and can they be used to propagate and navigate throughout the environment – and if so, how far? Is it possible to bridge networks? Is my firewall properly configured? Is my network segmentation working effectively? Can someone move from our DMZ network to our production network? If someone compromised a device via phishing in our finance department; how far could they move within our environment based on our current configurations? How long would it take to detect that behavior?
Other Doors and Windows – Patching and Legacy/BYOD Devices
Are we up-to-date with our patching? Have we omitted patching a device because of its role and if so, what is the level of risk that it creates? How can I quantify and prioritize patching related to Lateral Movement? What exploits and vulnerabilities would allow someone to successfully move in the network?
What risks are posed by allowing Bring Your Own Vulnerable Device platforms into my networks? Have I accounted for their security as well, and have I segmented out the networks they will use? Are legacy systems – which may not even be able to be restricted or patched in the same way as current systems – allowing attack surfaces to be leveraged?
With these three items identified we can now start to build a picture of what Lateral Movement looks like for our organization. Are there quick wins such as dealing with over-privileged accounts and improving firewall configurations? Can we prioritize patching within a certain network segment/location that is more critical for our business? Is our SOC service capable of detecting and reacting to Lateral Movement? What can we do to improve our existing controls before we start to look at tools such as Privileged Access Management?
Lateral Movement is an extremely broad term. The key to understanding is visibility. And what better way of doing that than using a platform that allows you to continuously test and demonstrate what Lateral Movement looks like in your organization.
Discover how Cymulate can enhance your security posture—book your demo today