Ransomware Detection Techniques: A Smarter Approach to Staying Ahead of Attacks

Ransomware attacks continue to rise in both volume and sophistication, crippling organizations, exfiltrating sensitive data and costing billions annually in recovery and downtime.
Early detection isn’t just important - it’s essential.
Attackers deploy advanced tactics to remain undetected for as long as possible, from polymorphic code and evasion techniques to time-delayed execution and lateral movement. Relying solely on traditional antivirus and endpoint protection to detect ransomware is no longer enough.
Security teams need smarter, faster and more proactive ransomware detection techniques to stay ahead.
What Makes Ransomware So Hard to Detect?
Modern ransomware strains are engineered to avoid conventional security tools. Here's why detecting ransomware is increasingly complex:
- Polymorphic Malware: Code changes on each execution, evading signature-based detection.
- Living-off-the-land Tactics: Attackers abuse legitimate tools like PowerShell or PsExec to avoid triggering alerts.
- Delayed Activation: Ransomware often lies dormant before executing, making early detection difficult.
- Lateral Movement: Attackers silently move across endpoints to escalate privileges and maximize damage.
- Double/Triple Extortion: Beyond encryption, attackers threaten to leak data or re-target unless ransoms are paid.
These stealthy characteristics make detecting ransomware during the early stages a critical but challenging task.
Common Signs of a Ransomware Attack
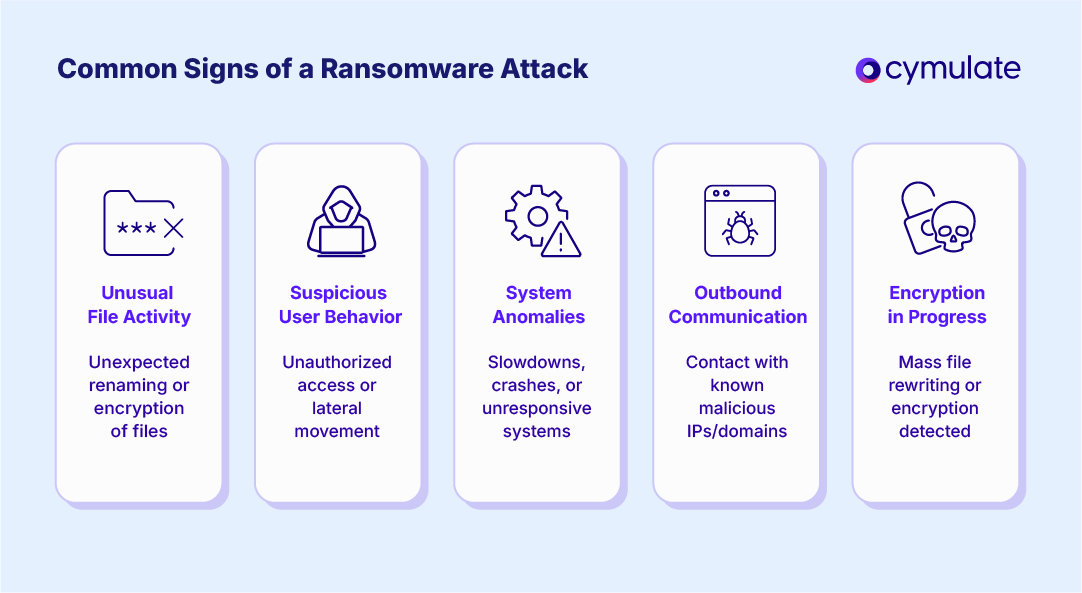
While ransomware can be stealthy, there are often detectable symptoms if you know what to look for. Key signs of ransomware include:
- Unusual File Activity: Unexpected file renaming, modifications, or unauthorized encryption behavior.
- Suspicious User Behavior: Privilege escalation or lateral movement by compromised accounts.
- System Anomalies: Sudden performance degradation, frequent crashes, or system unresponsiveness.
- Outbound Communication: Connections to known malicious domains or IPs.
- Encryption in Progress: The presence of processes aggressively reading and rewriting files in bulk.
Timely identification of these indicators is vital for swift incident response and mitigation. If not properly identified, you can quickly see how effective ransomware can be. Here’s how:
- Ransomware employs strong, unbreakable encryption algorithms, making it infeasible for victims to decrypt affected files without access to the attacker's private decryption key.
- It can encrypt a wide variety of file types, including documents, images, videos, and audio files, thereby maximizing the impact across personal and enterprise systems.
- Ransomware renames or scrambles file names during encryption, hindering the victim's ability to determine which files have been targeted.
- After encryption is complete, it presents a ransom note containing payment instructions. Payments are typically demanded in cryptocurrency, such as Bitcoin or Monero, to anonymize the attacker and bypass conventional financial oversight.
- Many ransomware variants are equipped with a "dead man's switch" or time-based triggers: if the ransom is not paid within a specified timeframe, the malware either deletes the encrypted data permanently or leaks stolen data publicly, damaging the brand, exposing sensitive information, or harming individual reputations.
- To ensure persistence and minimize detection, ransomware uses advanced evasion techniques, including code obfuscation, runtime packing, process hollowing and the disabling of endpoint protection tools, allowing it to bypass traditional antivirus and endpoint detection systems.
Ransomware Typology: Different Attack Types
As ransomware techniques have evolved, so too has the typology of attacks. Contemporary ransomware operations now span multiple categories, often overlapping or combining tactics for greater effectiveness. Below is a breakdown of the primary classes of ransomware observed in the wild:
1. Encrypting Ransomware
Also known as crypto-ransomware, this is the most prevalent type of ransomware in use today. It leverages strong cryptographic algorithms (often AES for symmetric encryption in conjunction with RSA for asymmetric key exchange) to encrypt critical files and render them inaccessible.
Victims are typically presented with a ransom note demanding payment (commonly in cryptocurrency) in exchange for the decryption key. The sophistication of key management and encryption implementation has increased over time, making manual recovery or brute-force decryption impractical in most cases.
2. Doxware / Leakware
A variant of traditional encrypting ransomware, doxware extends the attack surface by exfiltrating sensitive data prior to - or in lieu of - encryption. The threat actor then issues a secondary extortion demand, threatening to publicly release or sell the stolen data if the ransom is not paid.
This double extortion model has become increasingly common, with some campaigns incorporating direct outreach to customers, employees, or business partners of the victim organization to increase pressure.
3. Wiping Ransomware
Unlike encrypting ransomware, wiping variants do not offer data recovery as a viable outcome. These strains overwrite or corrupt the victim’s data irreversibly. In some cases, attackers may still demand a ransom under false pretenses, though no decryption or restoration mechanism exists.
This tactic blurs the line between ransomware and data destruction malware (e.g., wipers like NotPetya) and is often politically or ideologically motivated, rather than purely financially driven.
4. Ransomware-as-a-Service (RaaS)
RaaS platforms commoditize ransomware by offering ready-to-deploy ransomware kits, command-and-control infrastructure, and payment handling services to affiliates in exchange for a cut of the ransom profits.
These platforms operate similarly to legitimate SaaS models and drastically lower the barrier to entry for less technically skilled threat actors. RaaS has accelerated the proliferation of ransomware attacks, enabling organized cybercrime groups to scale operations through affiliate networks.
5. Locker Ransomware
Locker ransomware targets system functionality rather than file contents. These variants restrict user access to the infected operating system, often locking the screen and disabling input devices. Unlike encrypting ransomware, files themselves are typically left untouched.
However, access to applications and data is obstructed, and the attacker demands a ransom to restore system functionality. While less damaging than file encryption, locker ransomware can still cause significant operational disruption.
6. MBR Ransomware
A subcategory of locker ransomware, MBR (Master Boot Record) ransomware compromises the bootloader by overwriting the MBR with malicious code. Upon system startup, instead of the OS loading, the victim is presented with a ransom demand screen. Because this type of ransomware operates at the boot level, it effectively disables the entire system from loading, presenting unique recovery challenges that often require advanced forensic or boot-level remediation techniques.
7. Scareware
Scareware typically masquerades as legitimate security software or system alerts, falsely claiming that the victim's system is infected or compromised. These messages are engineered to induce panic, prompting the user to pay for fake remediation services or "cleaning tools."
While scareware lacks the destructive payloads of true ransomware, it remains an effective social engineering tactic, especially among non-technical users.
Conventional Ransomware Detection Techniques
Most organizations still rely on traditional tools and methods to detect ransomware:
- Signature-Based Antivirus and EDR: Detects known malware using predefined patterns but fails against zero-day or polymorphic variants.
- Heuristics and Behavioral Analysis: Identifies abnormal activity, though prone to false positives and limited by predefined baselines.
- Email Gateway Filtering: Scans attachments and URLs for known threats, often missing obfuscated payloads.
- SIEM and Log Analysis: Correlates logs and events to detect anomalies, but effectiveness depends on coverage and rule tuning.
These methods are valuable but reactive. They detect what's already happening, often after the initial compromise.
The Cymulate Approach to Proactive Detection
Cymulate transforms ransomware detection from reactive to proactive through its exposure validation and threat resilience platform. Unlike traditional tools, Cymulate continuously validates detection capabilities across the entire ransomware kill chain before real attackers strike.
Key Capabilities of the Cymulate Platform
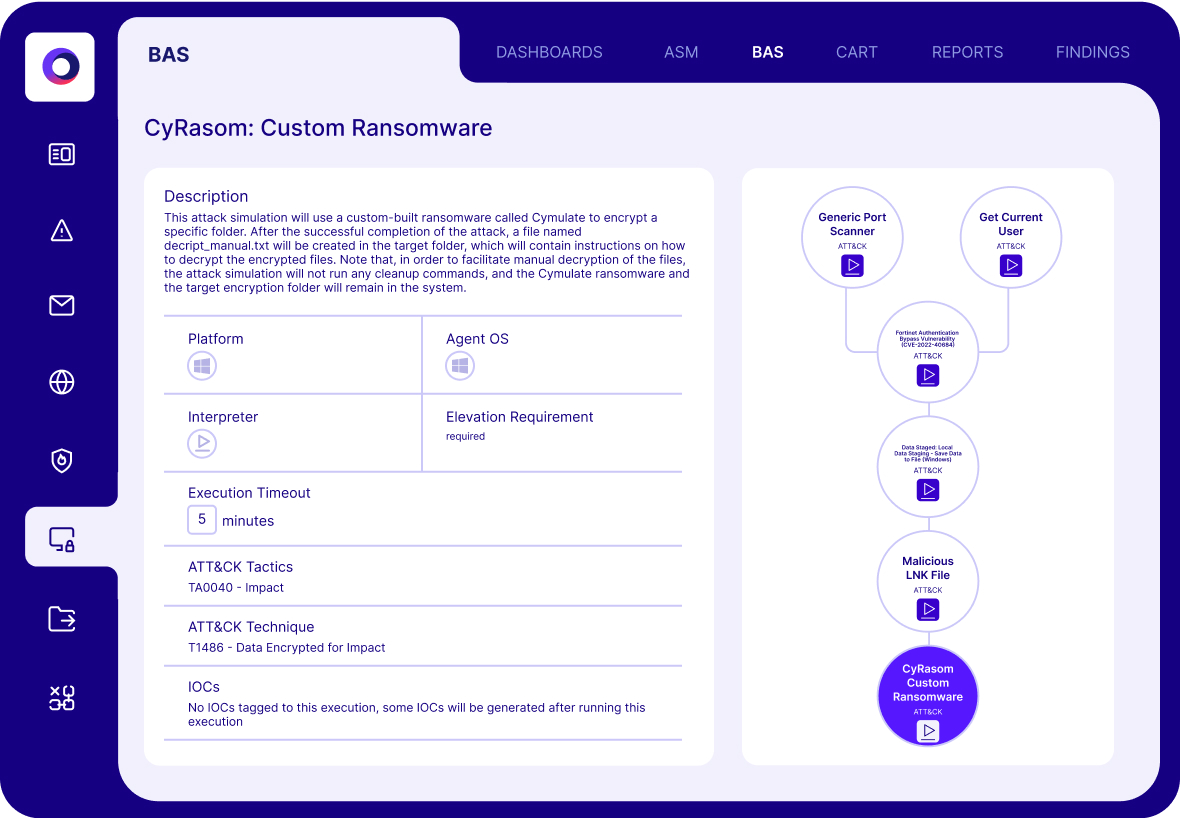
- Breach and Attack Simulation (BAS): Simulates real-world ransomware payloads, infection paths, and evasion tactics in production-safe environments.
- Email Gateway Testing: Validates how well email filters catch malicious attachments and links, before users click.
- Endpoint Security Vector: Launches multi-stage ransomware scenarios that assess how your EDR, antivirus, and XDR tools detect and respond.
- Full Kill Chain Emulation: Tests resilience from initial infection to lateral movement and encryption to exfiltration.
- Auto-Generated Sigma Rules: Instantly provides detection rules for SOCs to close observed gaps and reduce dwell time.
Real-World Application: Continuous Detection Without Disruption
The Cymulate platform is designed for continuous detection without interrupting daily operations or putting production systems at risk.
How It Works:
- Fast Deployment: Agents are optional, and cloud-native setup means you can start validating within hours.
- Click-to-Launch Testing: Pre-built scenarios make it easy to test against ransomware strains and tactics.
- Actionable Reporting: Detailed insights into what was executed, blocked, deleted or missed - mapped to MITRE ATT&CK.
- SIEM/EDR Integration: Findings can be correlated with tools like Splunk, Microsoft Defender, SentinelOne and more to accelerate detection and response workflows.
This capability moves teams beyond alerts to actual detection validation, closing gaps in real-time.
Benefits of Validated Ransomware Detection
Validation turns assumptions into facts, ensuring your ransomware defenses actually work when it matters. The detection-first approach from Cymulate provides tangible benefits:
- Reduce Dwell Time: Identify ransomware activity earlier in the kill chain, minimizing damage.
- Improve Incident Response: Equip SOC teams with precise, actionable data for faster triage and containment.
- Maximize Security Investments: Understand where your current stack works - and where it needs tuning.
- Prioritize Patch Management: Focus remediation efforts on exploitable paths and vulnerable assets.
By aligning detection with real-world attack behavior, Cymulate empowers security teams to act smarter, not just faster.
From Detection to Resilience: The Smarter Strategy
Detection alone is not enough. The new standard is validated detection - automated, continuous, and threat-informed. Ransomware is evolving every day, and so should your defenses.
Cymulate offers a smarter, scalable, and comprehensive strategy to detect, test and build resilience across all ransomware vectors. With exposure validation and threat resilience, organizations can stay ahead of ransomware attacks, not just respond after the damage is done.
Explore how Cymulate helps your team become ransomware resilient.



