What is Continuous Threat Exposure Management (CTEM)?

Continuous Threat Exposure Management (CTEM) is not a tool or a technology, it's a program. The rationale behind adopting this concept and rolling it out in your organization is straightforward: Continuously plan, monitor, and reduce your level of risk using validation technologies that prompt prioritized remediation actions based on the business context, so executives understand and engage.
Gartner predicts that organizations that adopt this model will be far less likely to be breached.
The 5 stages of Continuous Threat Exposure Management
The five stages of the Continuous Threat Exposure Management (CTEM) program offer a comprehensive approach to managing security risks.
- The first stage is planning, where organizations assess potential threats and vulnerabilities specific to their environment. This step involves understanding the business context and aligning security strategies accordingly.
- Once the planning stage is complete, the next stage is monitoring. Organizations must continuously track and analyze changes within their systems, networks, and applications to identify any emerging threats or weaknesses. By staying vigilant, businesses can detect potential breaches or attacks early on and take immediate action.
- In the third stage of the CTEM program, organizations focus on validation. This involves using various technologies to validate the effectiveness of their security controls and measures. By conducting regular assessments and audits, businesses can ensure that their defenses are up to date and capable of warding off potential threats.
- The fourth stage is remediation. In this phase, organizations prioritize and address any vulnerabilities or weaknesses that have been identified through the monitoring and validation stages. Prompt remediation actions are taken to mitigate the risk and reduce exposure to potential threats.
- The final stage of the Continuous Threat Exposure Management (CTEM) program is response. This stage is all about developing and implementing an effective incident response plan. Organizations should have clear protocols in place to swiftly respond to any security incidents, such as breaches or attacks. This includes mobilizing resources, containing the incident, and minimizing the impact on systems and data.
By following these five stages of the CTEM program, organizations can better manage their security risks and reduce their exposure to threats. It's important for businesses to be proactive in their approach, continually assessing, monitoring, validating, remediating.
Detailed Steps in Exposure Management
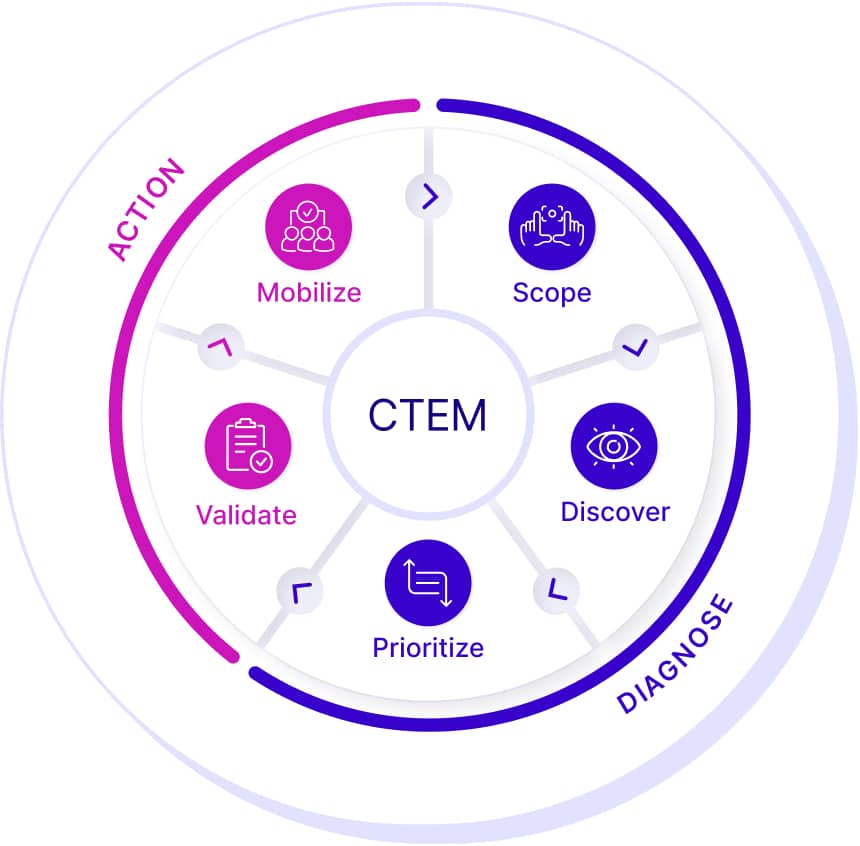
- Scoping – The first step in an exposure management program is, naturally, scoping the exposure. This is done by mapping the external attack surface and the risks associated with SaaS and software supply-chain. It requires a collaboration between the business and the security functions to define (or refine, in later iterations) what is mission-critical, high value, or sensitive, and the business objectives to support it.
- Discovery – consists of mapping the infrastructure, network, applications, and sensitive data assets, to find misconfigurations, vulnerabilities, and other tech/logic/process flaws and classify their respective risk.
- Prioritization – CTEM advocates evaluating the likelihood of exploitability – with or without regard to compensating controls – as the basis to grade their relative importance. Where the exploitability likelihood is low, the security gap is scored as a low priority and could be postponed if sufficient remediation resources are unavailable.
- Validation – Launch simulated or emulated attacks on the previously identified exposures to evaluate the efficacy of existing defenses, and validate that the immediate response and remediation are adequate, making sure to leverage initial foothold gains to test the attacker’s ability to exploit lateral movement routes to the critical assets. This stage requires using a large variety of techniques to assess the efficacy of both security controls and procedures.
- Mobilization – Taking corrective measures and actions deriving from business implications of the validation’s outcomes. It is usually done manually and within the local context. As CTEM depends much on collaboration, the remediation operationalization is expected to be near-frictionless and generate comprehensive information formatted to optimize rescoping for the subsequent cycle.
The ultimate goal of CTEM
Ultimately, CTEM is about security posture optimization. Its continuous nature allows quick remediation and application of previous ‘lessons’ to each exercise. Success depends much on agility, accelerated by both automation and rapid mobilization. This way, it can meet the risk requirements defined in agreement with the organizational or business priorities defined from the beginning in collaboration with executives.
Continuous improvement is a core principle of CTEM, as it is an ongoing process that requires continuous evaluation, adaptation, and improvement based on lessons learned and evolving threats and security measures.
Cyber threats have become a major concern for businesses and organizations as they increasingly rely on technology to operate. Exposure to cyber threats can result in data breaches, financial losses, and reputational damage. Therefore, it is important to proactively assess and manage cyber threats through a continuous threat exposure management program, which provides valuable insights, intelligence, and context to enhance the effectiveness of the Security Operations Center (SOC). This ensures that businesses are up-to-date with the latest security best practices and technologies, and can effectively address the ever-evolving and sophisticated nature of cyber threats.
With a continuous exposure management solution, organizations can adopt a forward-looking approach towards cybersecurity and have faster response capabilities in the event of an incident.

Three Reasons Cymulate is your Continuous Threat Exposure Management Partner of Choice:
1. Multifunctional Validation Platform
Rolling the CTEM program out cannot depend solely on technology, but a platform that consolidates the different functions necessary for security posture assessment and optimization is a key component that simplifies the process and helps operationalize the program.
For instance, Cymulate brings together external attack surface management (EASM), automated red teaming, vulnerability prioritization, and breach and attack simulation capabilities.
Threat detection is a critical aspect of cybersecurity. It involves identifying potential attacks and vulnerabilities that can compromise a system's security. Automated threat detection systems are an effective way to detect and respond to threats in real-time. These systems use advanced algorithms and machine learning techniques to analyze network traffic, detect anomalous behavior, and alert security teams about potential attack paths.
Implementing threat detection systems can help businesses reduce the impact of security incidents and prevent major breaches from occurring. However, it is important to note that these systems may not be able to address complex or nuanced vulnerabilities on their own.
2. Test and Evaluate Processes
Assessing security technologies is insufficient. We started by stating that CTEM isn’t a tool. Its success depends on the collaboration between teams and workflows between them. Part of the evaluation of the security strategy focuses on processes. Responsibilities, handoffs, information flows, awareness, response, priorities, and so on.
Therefore, testing the SOAR playbooks, SOC, and incident response validation (internal or managed) via tabletop exercises and simulated attacks are necessary to reflect how resilient an organization is and set the baseline for the next scoping and discovery cycles.
Penetration testing
Penetration testing is an essential part of assessing the level of threat exposure to a company's IT resources. It involves testing for vulnerabilities in the system and identifying potential dangers that could be exploited by cybercriminals. Other security audits like vulnerability assessments and vulnerability scanning are also conducted to ensure the safety of IT resources.
With penetration testing, businesses can detect flaws in their security systems and take measures to address them before they become a problem. This proactive approach helps prevent potential threats and ensures the safety of sensitive data.
3. Translate Findings into Business Implications
The above combination of validation technologies into one platform facilitates the collection of extensive information. Security teams, however, have no time to really get into the details of each event or finding. Therefore, they need some guidance for the mobilization phase to translate that information into scores reflecting the potential business impact or risk level.
Gartner’s CTEM program underlines that there is no game without executive leadership requiring straightforward reports, performance improvement over time, drift control, and good scores overall.
Cyber threats can have a significant impact on business operations, making it important for organizations to be proactive in addressing them. The Continuous Threat Exposure Management (CTEM) approach evaluates the risk associated with each business asset and ranks them based on their criticality to operations.
By aligning security protocols with business goals, CTEM enables organizations to enhance operations while also improving their security posture. To achieve this, businesses can leverage advanced tools like threat intelligence platforms and external attack surface management solutions to gain comprehensive visibility into their security posture and prioritize the most critical risks.
This approach, known as vulnerability management, allows organizations to continuously monitor and address potential vulnerabilities before they can be exploited by cyber threats.
By implementing CTEM, organizations can stay ahead of evolving threats and minimize the impact of cyber attacks on their operations.
Key Takeaways
Moving from a reactive approach to a proactive approach against cybersecurity threats with programs like Continuous Threat Exposure Management can help organizations better prioritize their efforts and build greater resilience over time against against these types of attacks.
With the rise of cyber-attacks and data breaches, companies should take a proactive approach towards cybersecurity and risk management by gaining a deeper understanding of their cyber estate on an ongoing basis. This will enable organizations to take prompt action based on a thorough, contextual analysis, thereby facilitating a more proactive approach to addressing cyber risks through advanced strategies like continuous threat exposure management in their security operations led by security leaders.
Better and faster decision-making is at the heart of a successful Continuous Threat Exposure Management program and its ultimate KPI. If security posture is tested in advance, preemptive measures are taken, risks remain low, and adversaries are likely to move on to the next target.