Top 10 Vulnerability Management Metrics for Effective Reporting

To stay ahead of attackers and demonstrate progress to stakeholders, organizations must measure how effectively they manage and reduce cyber risk. Tracking the right vulnerability metrics transforms security operations from reactive to strategic, helping teams prioritize efforts, track remediation and quantify security posture over time.
When organizations adopt a risk-based approach to vulnerability management, the right metrics become more than technical indicators. They serve as operational key performance indicators (KPIs), guide resource allocation and support executive decision-making.
Let's explore the most critical vulnerability management metrics every security leader and practitioner should monitor. We’ll also show how Cymulate enhances visibility across each dimension.
What are vulnerability management reporting metrics?
Vulnerability management metrics are measurable indicators that show how effectively an organization identifies, prioritizes and remediates security weaknesses across its environment. These metrics convert raw scan data into actionable insights that help teams understand where they stand and where the most significant security risks remain.
Unlike simple vulnerability counts, these measurements reveal how efficiently teams detect, patch and validate issues over time. By consistently tracking these metrics, enterprises gain visibility into both operational performance and long-term security maturity, empowering them to:
- Compare progress quarter over quarter
- Identify recurring gaps
- Make informed, risk-based decisions
Leveraging a centralized vulnerability management metrics dashboard provides a single source of truth for measuring how well a security program actually protects the business.
10 best KPI metrics for vulnerability management tracking
The right metrics don’t just describe how many vulnerabilities exist. Instead, they reveal how efficiently your organization detects, prioritizes and resolves them. Tracking these KPIs provides both technical and business visibility, helping teams understand where risk is concentrated, how fast issues are being fixed and whether their remediation efforts are improving over time.
Below are 10 essential vulnerability management metrics every security team should monitor to measure and understand their resilience.
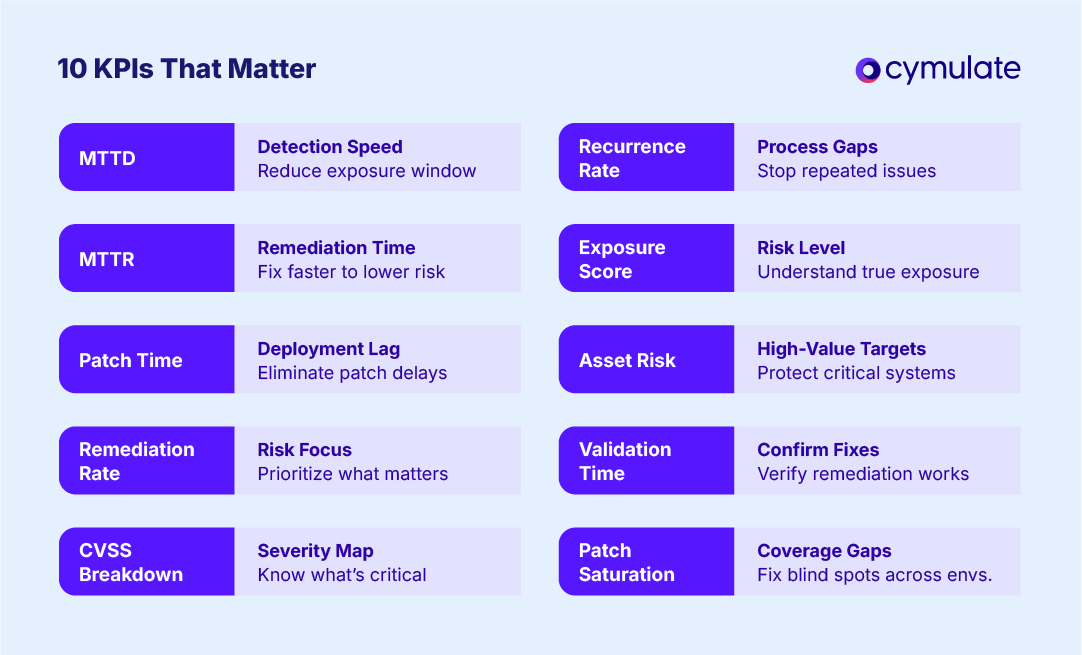
1. Mean time to detect (MTTD)
Mean time to detect measures the average time between when a vulnerability appears and when your security tools or analysts first identify it. It reflects detection efficiency across scanning, alerting and monitoring processes.
Why it matters: A high MTTD implies a long exposure window, giving attackers more time to exploit weaknesses. Reducing mean time to detect is foundational to minimizing risk and improving response capabilities.
Strategic impact: Fast detection shortens the attack lifecycle. It’s also essential for compliance with internal SLAs and external regulations.
Real-time exposure assessments from Cymulate help reduce MTTD by continuously validating security controls and identifying new weaknesses.
2. Mean time to remediate (MTTR)
What it measures: The average time taken to fix or mitigate a detected vulnerability.
Why it matters: MTTR reflects the agility of your response and the efficiency of remediation processes. Lower MTTR reduces dwell time and the likelihood of successful exploitation.
Strategic impact: Tracking MTTR informs process optimization and cross-team collaboration. It also enables SLA enforcement across IT and security operations.
3. Patch time
Patch time measures the time from when a vendor releases a patch to when it’s deployed across affected systems. It reveals how streamlined and responsive your patch management pipeline is.
Why it matters: Delays in patching—even for known exploits—leave environments exposed.
This metric highlights bottlenecks in patch management pipelines.
Strategic impact: Used for benchmarking patch effectiveness, this metric supports prioritization based on exploitability and business risk. Combined with exposure analytics, teams can validate whether patching efforts actually reduce exposure.
4. Remediation rate
Remediation rate measures the proportion of critical or high-severity vulnerabilities resolved within a set period. It helps quantify how well remediation aligns with defined SLAs or security objectives.
Why it matters: Focuses on risk-based prioritization. Not all vulnerabilities are equal; tracking the remediation of the highest-impact ones ensures resources are applied effectively.
Strategic impact: A low remediation rate signals systemic gaps in vulnerability management, potentially requiring more resources or better prioritization tools.
5. CVSS breakdown
CVSS breakdown categorizes vulnerabilities according to the Common Vulnerability Scoring System (CVSS), a standardized framework for rating the severity of security flaws. It reveals how vulnerabilities are distributed across critical, high, medium and low tiers.
Why it matters: Provides an at-a-glance view of risk severity distribution. Helps triage vulnerabilities by impact and exploitability.
Strategic impact: Supports communication with non-technical stakeholders by quantifying the threat landscape in standardized terms. Utilize context-aware scoring aligned with asset importance and exposure levels.
6. Recurrence rate
Recurrence rate measures how often a previously fixed vulnerability resurfaces in the environment. It indicates how consistent and durable remediation efforts truly are.
Why it matters: Indicates process failures, configuration drift or inadequate patching controls. Recurrence undermines trust in remediation efforts.
Strategic impact: Recurring issues demand process automation, stricter configuration management or improved validation. A best practice is to continuously test the environment to detect reintroduced exposures before they escalate.
7. Exposure score
Exposure score combines vulnerability severity, exploitability and asset criticality into a single risk-based measurement. It represents your organization’s overall exposure level at a given point in time.
Why it matters: This score provides a holistic view of your actual cyber risk—not just theoretical
vulnerabilities. It's essential for prioritization and risk communication.
Strategic impact: Enables comparisons across business units, environments or time periods.
Cymulate Exposure Analytics provides real-time scoring tied to attack simulations and asset context.
8. Asset risk
Asset risk measures the proportion of total organizational risk attributable to individual systems or business units. It highlights where remediation will have the most significant impact on reducing exposure.
Why it matters: Not all assets are equal. This metric supports asset-based risk management, ensuring high-value targets receive the most protection.
Strategic impact: Getting this right helps CISOs and engineers align security investments with business priorities. It’s best to enable asset-centric exposure views to highlight which systems require urgent attention.
9. Validation time
Validation time measures the gap between initial remediation and confirmed verification through testing or rescanning. It ensures that reported fixes are validated and effective.
Why it matters: Assumptions of successful remediation without verification can lead to false confidence and residual risk.
Strategic impact: Reduces the risk of incomplete fixes. Enable immediate validation through breach-and-attack simulation, ensuring mitigation efforts are effective.
10. Patch saturation
Patch saturation measures the percentage of assets successfully updated across all environments on-premises, cloud and hybrid. It provides insight into the consistency and reach of your patch deployments.
Why it matters: Inconsistent patching across environments introduces risk asymmetry and potential backdoors.
Strategic impact: This metric supports comprehensive coverage and highlights potential blind spots. Uncover these disparities by testing real-world attack paths across all environments.
Challenges of gathering key vulnerability management metrics
Even with the right tools, collecting accurate and actionable vulnerability metrics remains a challenge for most organizations. Inconsistent data, tool sprawl and limited visibility often make it difficult to measure true risk reduction.
Here are the biggest obstacles security teams face, along with strategies to overcome them.
Data fragmentation
Security data rarely resides in a single place. Vulnerability scanners, CMDBs, SIEMs and ticketing tools each hold partial pieces of the puzzle. Without a centralized view, teams spend hours reconciling results or manually merging spreadsheets, often introducing errors.
This fragmentation slows decision-making, masks cross-system dependencies and undermines confidence in the accuracy of reported metrics—especially when leadership needs timely updates on risk posture.
How to avoid data fragmentation:
Adopt integrated platforms or data pipelines that automatically consolidate vulnerability, asset and threat information. Establish standardized reporting APIs and cadence to ensure all systems update simultaneously.
Inconsistent scoring and prioritization
Not all vulnerability scanners interpret risk the same way. Two tools analyzing the same issue might assign different severity levels, creating confusion and inconsistent prioritization. Over time, these discrepancies cause teams to misjudge which vulnerabilities are truly urgent.
When critical flaws are overlooked or downgraded due to inconsistent scoring, the organization’s exposure window increases—sometimes significantly.
How to standardize scoring:
Normalize results using a unified framework, such as CVSS v3.1, and enrich it with exploitability and asset criticality data. Layering contextual factors ensures metrics reflect real-world business impact, not just technical severity.
Manual and reactive reporting
Many organizations still rely on spreadsheets or exported reports to track vulnerability management metrics. These manual processes can’t keep up with today’s dynamic environments, where new vulnerabilities surface daily. As a result, metrics quickly become outdated, delaying remediation efforts and limiting visibility into current exposure.
This reactive approach also prevents security leaders from demonstrating program progress to executives or auditors with confidence.
How to automate reporting:
Implement dynamic dashboards that continuously pull data from scanning tools, analytics engines and ticketing systems. Automated updates and visual summaries keep reports accurate and ensure stakeholders see real-time trends.
Limited asset visibility
Modern IT ecosystems evolve rapidly, with assets spinning up and down across hybrid and multi-cloud environments. Untracked virtual machines, shadow IT or unmanaged endpoints often fall outside the scope of scanning tools. These blind spots skew vulnerability data and hide exploitable weaknesses from analysts.
Without complete visibility, even the most sophisticated metrics provide an incomplete picture of enterprise risk.
How to improve visibility:
Use continuous asset-discovery solutions to automatically identify and classify all systems across environments. Maintain an up-to-date inventory and tag assets by function or criticality to improve reporting accuracy.
Lack of validation and follow-through
Fixing vulnerabilities doesn’t guarantee they’re resolved. Many teams close tickets once patches are applied, without verifying whether remediation actually worked. In complex environments, patches may fail silently, configurations may drift or new updates may reintroduce the same issue.
Without validation, organizations risk overstating their security posture and leaving known flaws open to exploitation.
How to ensure effective validation:
Conduct continuous testing and retesting using breach and attack simulation or automated validation tools. Confirm that remediations hold over time and track recurrence rates to identify systemic weaknesses.
Why managing vulnerability metrics is critical for enterprises
A comprehensive solution for managing vulnerability metrics turns complex technical data into clear, measurable insights that guide better decisions. By tracking key indicators over time, organizations can measure progress, benchmark performance and demonstrate accountability at every level.
Core benefits include:
- Improved visibility: Metrics highlight where exposure is highest and how remediation efforts are trending.
- Resource alignment: Teams can prioritize based on actual business impact rather than raw vulnerability counts.
- Executive confidence: Quantified risk data helps communicate security posture to non-technical stakeholders.
Program maturity: Consistent measurement turns vulnerability management into a structured, repeatable process. - Proactive defense: Metrics enable early detection of gaps before they escalate into incidents.
Collectively, these benefits help organizations evolve from reactive patching to proactive, risk-informed security management. Yet according to the 2024 Cymulate State of Exposure Management and Security Validation report, organizations still average only 64%–89% control effectiveness across tests of known security vulnerabilities. This persistent gap shows why metrics must go beyond simply counting potential threats — it’s critical to confirm that defenses perform as expected.
How to use vulnerability management program metrics for strategic security reporting
The true power of vulnerability management metrics lies in how they inform decisions. By transforming scan data into meaningful business insights, security leaders can demonstrate measurable progress, communicate value to executives and guide continuous improvement across teams.
Each of these KPIs for vulnerability management plays a strategic role:
- Vulnerability management SLA tracking: Metrics such as MTTR, MTTD and the percentage of vulnerabilities remediated help enforce internal security agreements and regulatory obligations.
- Resource prioritization: Risk-based metrics like asset contribution and exposure scores ensure remediation efforts align with business risk.
- Risk-based decision making: Technical findings translated into executive reports so business leaders can make more informed decisions and ensure long-term effectiveness.
- Audit readiness: Consistent vulnerability management reporting supports compliance with standards such as ISO 27001, NIST and PCI-DSS.
- Continuous improvement: Trends in recurrence rate, patch saturation and time to validate remediation help fine-tune operational processes.
Ultimately, these metrics elevate security programs from operational maintenance to measurable, strategic risk score reduction, building resilience and improving security posture.
Best practices for managing metrics for information security vulnerabilities
To get full value from vulnerability assessment metrics, security teams should combine automation, risk-based prioritization and continuous validation within a structured management framework. Yet, according to our State of Exposure Management report, only 37% of organizations have fully mature risk-based prioritization.
The following five best practices can help your enterprise close the gap and ensure metrics drive measurable improvement:
- Automate data collection: Integrate scanning and analytics tools so metrics update in real time.
- Align vulnerabilities with business risk: Prioritize vulnerabilities by asset value and exploitability, not just by count.
- Establish SLAs for remediation: Define acceptable detection and remediation timelines and hold teams accountable.
- Visualize vulnerability management progress: Use dashboards to show trends in exposure, remediation and SLA adherence.
- Validate your remediation results: Continuously test to confirm that fixes actually reduce risk exposure.
Learn more: explore Cymulate’s risk-based approach.
Cymulate manages and enhances vulnerability assessment metrics
Traditional vulnerability management tools focus on enumeration. Cymulate advances this by offering continuous exposure validation, asset-level analytics and remediation tracking that aligns with real-world attack scenarios.
Using Cymulate Exposure Analytics, organizations can:
- Monitor MTTD, MTTR and validation timelines with real-time data.
- Measure exposure at the asset and environment level.
- Prioritize remediation based on exploitability and attack path simulations.
- Continuously validate that applied fixes reduce actual risk—not just theoretical vulnerabilities.
Unlike traditional scanners, Cymulate helps security teams shift left and right: identifying exposures earlier and ensuring their resolution actually defends against attackers.
Here’s what Shaun Curtis, Head of Cybersecurity, GUD Holdings, had to say:
“Basic vulnerability scans tell you where you're vulnerable, but Cymulate tells you if you will be compromised. Vulnerability scanning just gives a report. Cymulate gives us intelligence.”
For organizations moving from vulnerability management to complete exposure management, these capabilities are essential.
Ready to get started? Book a demo today and see how Cymulate can help you turn vulnerability management metrics into actionable BI that drives results.
Frequently asked questions
There isn’t a single KPI that defines success, but Mean Time to Remediate (MTTR) is often viewed as the most telling. It measures how quickly vulnerabilities are fixed after discovery, reflecting both team efficiency and organizational responsiveness. When combined with MTTD and exposure metrics, it provides deeper performance insight.
Vulnerability metrics should be reviewed continuously, not just during quarterly reporting cycles. Automated dashboards and exposure analytics make it possible to track real-time changes, ensuring data reflects current risk levels. Continuous measurement also helps teams identify trends, reduce dwell time and respond faster to emerging vulnerabilities and threats.
Consistent tracking of vulnerability metrics helps identify process bottlenecks, prioritize high-risk assets and validate that remediations are effective. Over time, these insights enhance collaboration between security and IT teams, reduce response times and drive measurable improvements in resilience, compliance and overall cybersecurity maturity across the organization.



