Cymulate recently announced the launch of “Exposure Analytics”, the latest addition to the Cymulate Exposure Management and Security Validation platform.
Exposure Analytics collects data from across enterprise IT, clouds, and the security stack to support exposure management programs to measure and baseline cyber resilience, focus on the biggest risks, and accelerate mitigations. As such, it provides the missing technological links needed to operationalize the Gartner-recommended continuous threat exposure management (CTEM) approach.
I was lucky to be part of the genesis of Cymulate Exposure Analytics and to contribute to its development into a working product. That process weaved together the shifting trends in our customers’ requests and queries, the insights from our researchers about the interplay between threats and digital infrastructure evolution, and the input from reputed cybersecurity analysts and think tanks.
The Pre-Exposure Analytics Era
As a security validation platform, Cymulate initially focused on validating security controls by automating attack simulations and identifying where they bypassed defenses.
That is a technological issue developed by tech-minded people for tech-minded people. Back then, cybersecurity was still the ultimate natural reserve for tech nerds.
In that tech realm, discussing improvements to the technology led to expanding into a wider range of simulation types, expanding from the initial BAS (Breach and Attack Simulations) capabilities into ASM (Attack Surface Management) and CART (Continuous Automated Red Teaming).
Customer feedback was also mainly about technical tweaks, and conversations flowed easily in tech jargon.
Requests for integrating Cymulate validation capabilities with vulnerability management, SIEM, SOAR, and other scanning, detection and response, and orchestration tools were a common occurrence. Our team is used to rapidly answer such requests and grow our technological partners ecosystem, so the data flow from a growing number of sources enriched the findings.
Misunderstanding the Pain Point
But as the importance of cybersecurity made more and more inroads into the business concerns realm, the nature of customer requests began to shift.
With finite resources facing an ever-rising tide of threats number and complexity meant, the goal of succeeding in preventing every single breach was becoming increasingly elusive.
Customers began asking how to ensure that their security posture management efforts were focused on areas with the highest protective impact on operability and on selecting the data to protect in priority based on the data business value.
As cybersecurity experts, we thought that providing a quantified risk score based on verified resilience to attack simulations and providing the data required to rationalize and optimize cybersecurity tool stacks would be the perfect answer to business concerns.
So, we did more of the same!
We added more capabilities, internal ASM, attack path mapping, lateral movement, cloud security, network segmentation validation, and so on.
Yet, our efforts to answer the increasing number of customer requests for business-oriented answers focused on improving the risk scoring quantification granularity and depth, providing options for report customization, integrating with a ticketing solution to increase operability, and other practical features and capabilities. On the plus side, these enhancements made Cymulate the only platform centralizing all those capacities in a single platform.
On the plus side, these enhancements made Cymulate the only security validation provider centralizing all those capacities in a single platform.
Still, from a business context perspective, we were missing the elusive main point.
Identifying the Missing Link
It took numerous consultations with customers, analysts, and advisors to bridge the gaps between the technologically minded cyberpeople and the priorities expressed by the business experts, but in time, a new paradigm began to coalesce.
The motivation behind all the integrations with technical partners was gathering tech data and correlating it with more tech data.
But we were still missing the business value element.
In other words, if the risk score of an unlocked room is high, the business risk is very different if the unlocked room contains trade secrets or brooms and buckets.
Once that light bulb finally turned on, we began working on what is now crystallized into the Exposure Analytics newly launched product.
Putting it All Together
The first step was realizing that our existing products created disconnected pieces of the cybersecurity puzzle that needed to be connected to form a coherent image.
The second step was to absorb the idea that no two organizations are the same and each has its own operational and business priorities. Creating a cybersecurity image intelligible to non-tech people would also have to take these idiosyncrasies into account.
The third step was a collaborative effort between R&D, design partners, and advisors to conceptualize how to ingest diverse data feeds, correlate the findings, and enable individualized asset business value customization to generate insights.
The requirements for those insights were that they would guide the remediation efforts to prioritize those with the highest business impact.
Initially, our risk calculations were done at the asset level, assigning a risk score based on the severity of security findings and the extent of assets they impact. While this was pretty nifty, it was not enough.
As feedback from our partners kept lamenting the lack of business impact factors within the risk calculations, we returned to the drawing board. They were right. Our risk calculations led to conclusions disconnected from business priorities and operational dependencies.
So, we tried again.
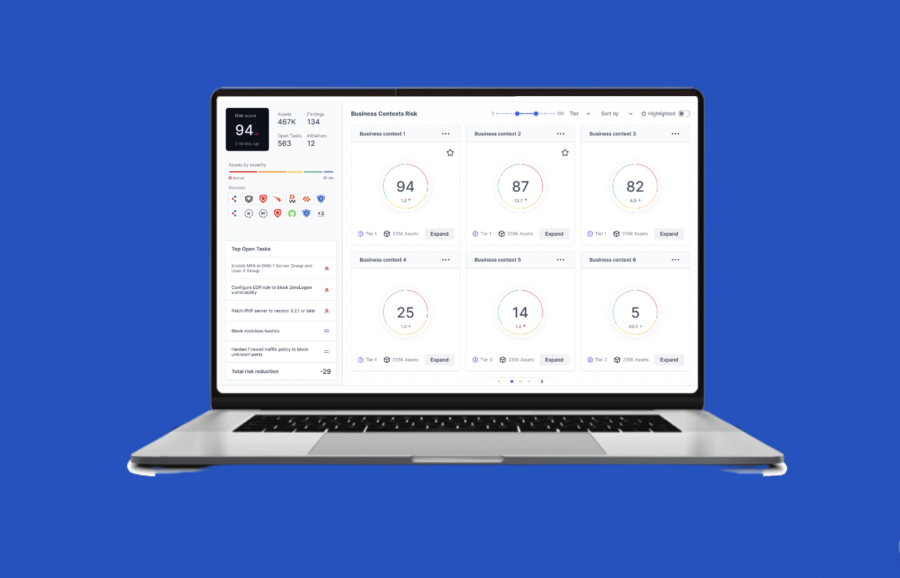
This time, we introduced the concept of “business context”. In the absence of unified data sets to incorporate business context into the risk score calculation, we added a way for organizations to input their own perception of risk based on individual assets’ value.
This inclusion revolutionized the results, aligning priorities rooted in technical concepts with business valuation and providing a unified view that aligns risk assessment with business strategy.
As the product manager for Exposure Analytics development, I wish I could get the credit for it, but, in truth, it would never have been possible to create such a timely, innovative, and altogether phenomenal product without the constant collaboration between Cymulate teams and departments, and the inputs and feedback from customers, partners, analysts, and advisors.
To learn more about Exposure Analytics
- Download the Datasheet
- Read the press release
- Watch the webinar