Traditional Vulnerability Management is Not Enough
Ever since Gartner® introduced its Continuous Threat Exposure Management (CTEM) program, there has been a shift in how the industry talks about “proactive” cybersecurity. While organizations used to concentrate on patching vulnerabilities, many are taking a broader approach to focus on exposures.
But why the change?
Traditional vulnerability management aims to strengthen your security posture by internally focusing on identifying and remediating Common Vulnerabilities and Exposures (CVEs)—the industry-reported weaknesses that an attacker can potentially exploit. In comparison, exposure management adopts the attacker’s view of your organization to focus on the most potentially damaging security gaps in your unique risk landscape.
By taking the attacker’s view, you can validate where your gaps are. Rather than relying only on vulnerability scanners or annual penetration tests, you need tools that automate offensive security testing to assess controls, threats, and attack paths continuously.
Exposure management software enables you to keep your organization safe and stay one step ahead of an attack by focusing your resources on where you need them the most. The Cymulate 2024 State of Exposure Management & Security Validation report proves the importance of adopting an exposure management strategy that considers:
- Source of exposure – vulnerability, misconfiguration, control gap, etc.
- Business impact – critical assets, data, and infrastructure at risk
- External threat activity – known or active attacks that target the exposure
- Attack feasibility – effectiveness of mitigating controls to prevent a breach if attacked
Focus on the Biggest Weaknesses, Not the Most Severe CVEs
The State of Exposure Management & Security Validation report aggregates anonymized data from attack surface assessments, simulated attack scenarios and campaigns, and automated red teaming performed with the Cymulate Exposure Management and Security Validation Platform across a global user base of over 500 customers.
As part of these offensive security assessments in 2023, Cymulate identified the top 10 most assessed (most popular) and top 10 most successful threats that target CVEs.
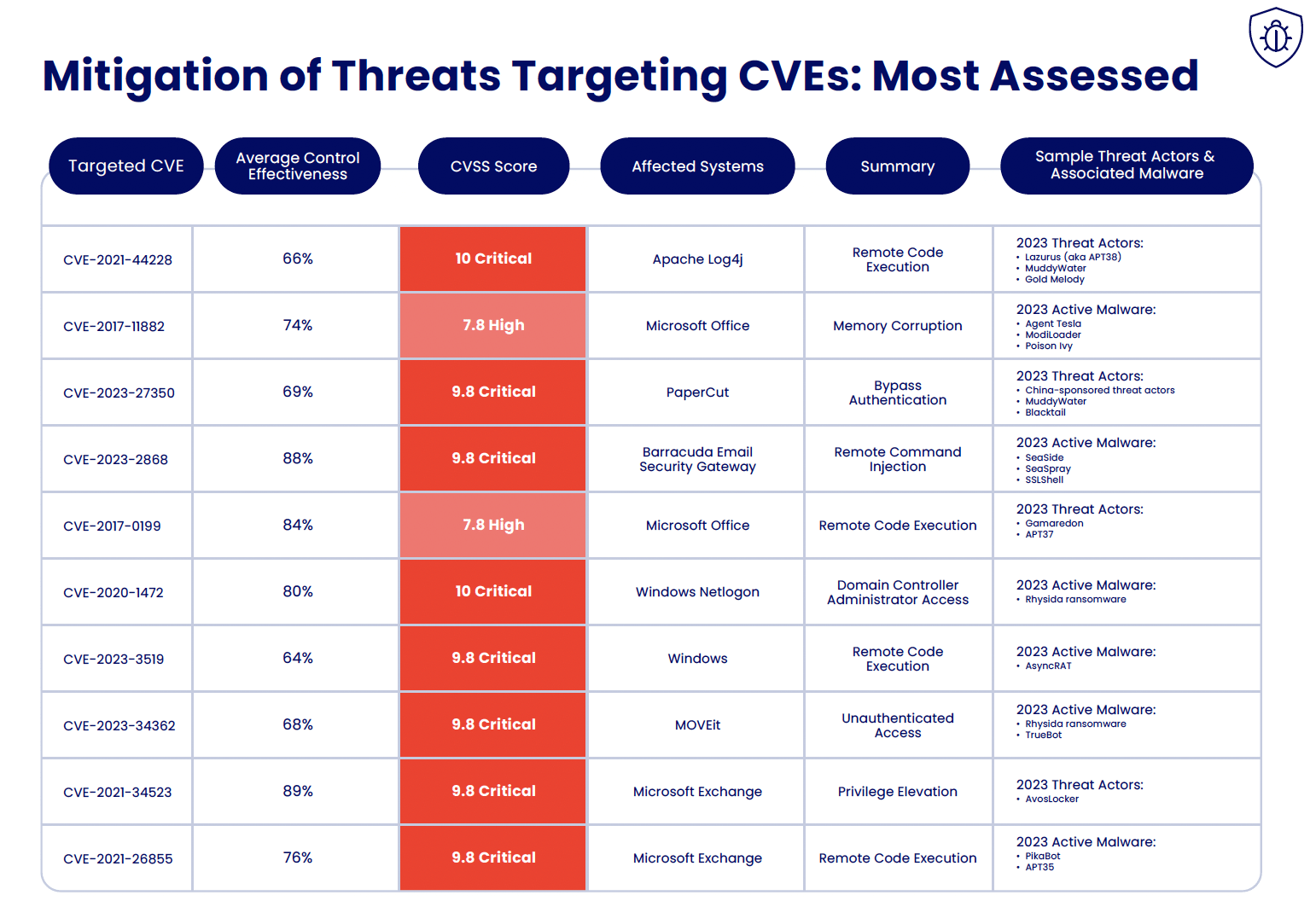
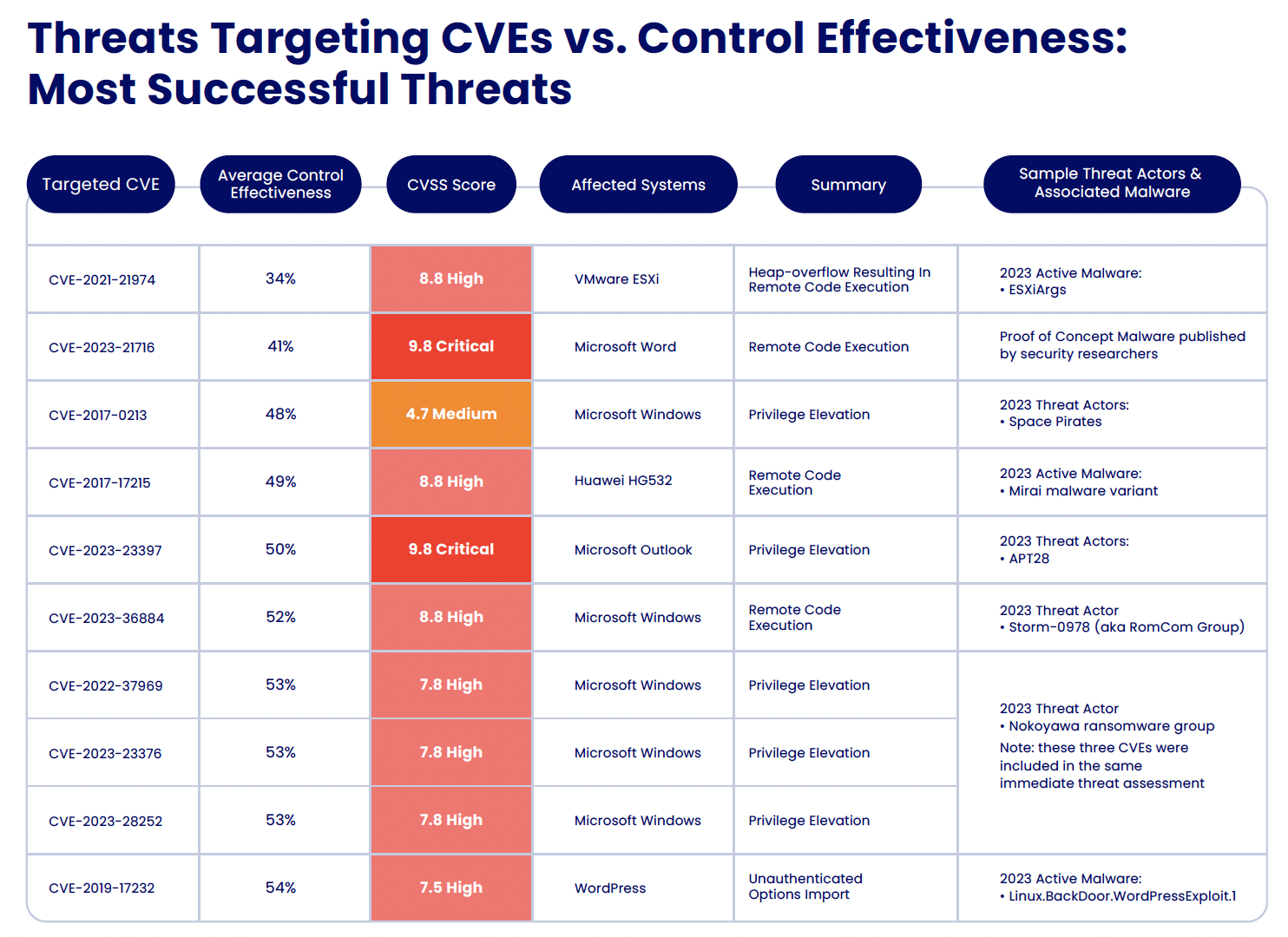
*Average Control Effectiveness – The average control effectiveness rate reported is based on the security controls’ ability to recognize known Indicators of Compromise (IoCs). The Immediate Threats module of Cymulate BAS does not run active code like other Cymulate BAS modules. The other modules in Cymulate BAS do assess the effectiveness of behavioral detection and monitoring solutions in stopping executions in progress. In the case of threats with CVEs, the results do not indicate the presence of the vulnerability.
Interestingly, none of the CVEs most frequently assessed make the list of the most successfully exploited. This disconnect highlights a nuance in exposure management: It’s not only the identification of critical or high vulnerabilities that matters but whether they are actually exploitable within an organization’s unique environment. The report illustrates scenarios where vulnerabilities with high severity scores were effectively neutralized by compensating controls, preventing successful exploitation.
Exposure management provides a holistic view of an organization’s security posture. This strategy allows for a more strategic allocation of security resources, prioritizing actions based on the actual risk posed to the organization. For instance, a high-severity vulnerability in a system that is critical to business operations and contains sensitive data would warrant immediate action. Conversely, a similar vulnerability in a less critical system, adequately protected by other security measures, might be deprioritized. Additionally, exposure management doesn’t only focus on vulnerabilities; it assesses all types of exposures, including misconfigurations and gaps in controls, to evaluate which ones are the riskiest to your organization.
The Cymulate approach emphasizes continuous scanning and assessment from an attacker’s perspective. This method identifies exposures by simulating attack paths and scenarios to provide a realistic view of potential security breaches. Through continuously monitoring the attack surface, organizations can detect and address new exposures as they emerge rather than relying on periodic assessments that may leave gaps in coverage.
Add Context to Your Exposures with Cymulate
Exposure management represents a shift toward a more dynamic and proactive cybersecurity strategy. It acknowledges that not all vulnerabilities can or should be patched immediately but requires a strategic approach based on risk assessment and business impact. By focusing on the most significant weaknesses rather than the most severe CVEs, organizations can allocate their resources more effectively, ensuring the security of their digital assets and, by extension, their business operations.
The insights from the Cymulate 2024 State of Exposure Management & Security Validation report emphasize the importance of adopting an exposure management approach to stay ahead of potential threats.
Download the full report here >>








