Initial Access Brokers
What are Initial Access Brokers (IABs)? The Hidden Players Behind Ransomware Attacks
Initial Access Brokers (IABs) are specialized cybercriminals who break into corporate networks and then sell that unauthorized entry to other attackers. In effect, they act as “high-value middlemen” providing “access-as-a-service,” monetizing the breach while avoiding the risk of executing the final attack.
Once inside an organization, an IAB typically establishes multiple backdoors or stolen accounts and then advertises those access credentials on dark forums or private channels.
This brokered model enables Ransomware-as-a-Service (RaaS) and fraud groups to bypass the time-consuming intrusion stage. In fact, experts note that in the RaaS ecosystem, access brokers “specialize in identifying and exploiting vulnerabilities” and then sell this network access to ransomware operators, allowing attackers to skip straight to deployment.
In short, IABs are the “opportunistic locksmiths” of the cybercrime world, prying open the digital doors for others to break in.
How Initial Access Brokers Operate
IABs are a distinct category of cybercriminals whose primary role is to gain unauthorized access to networks and then sell that access to other threat actors. Unlike hackers who complete the entire attack lifecycle—from initial compromise to data exfiltration or ransomware deployment—IABs focus exclusively on the first stage: establishing a foothold in a network.
Rather than executing the attacks themselves, they monetize access by offering it for sale, often to ransomware-as-a-service (RaaS) affiliates or data extortion groups. This outsourcing model has become a core component of the modern cybercrime economy, enabling specialization and scalability.
One industry report noted that IABs often lack the technical skills—or simply the intent—to deploy ransomware, instead opting to "provide access as a service" and leave the dirty work to others.
Once an organization is breached, Initial Access Brokers (IABs) shift their focus to monetizing the compromise by selling access to other threat actors.
Access is typically categorized by industry vertical—such as finance, healthcare, or manufacturing—and then posted for sale on underground forums, encrypted chat channels like Telegram or invite-only marketplaces.
How IABs Monetize Network Access
IABs operate like illicit financial brokers, packaging access credentials and network backdoors for sale on dark web marketplaces. A 2023 threat intelligence analysis found that credentials for over 100 organizations across 18 industries were listed for sale on Russian-language hacking forums within just the first half of the year.
Their offerings typically include:
- VPN and Remote Desktop Protocol (RDP) credentials
- Active Directory domain access
- Admin/root accounts
- Webshell or backdoor implants
Prices vary widely based on the target's size, industry and geography, ranging from a few hundred to hundreds of thousands of dollars.
IABs frequently advertise on initial access markets—underground marketplaces or encrypted forums dedicated to selling hacked access.
What Do IABs Offer?
In many cases, IABs they provide comprehensive access packages that include credential dumps collected through infostealer malware, detailed vulnerability scanning and identification of exploitable flaws within a target’s environment.
Some IABs even go as far as delivering full network maps and access to privileged internal systems such as domain controllers or cloud management portals.
These enhanced offerings allow ransomware affiliates and other cybercriminals to bypass the time-consuming phases of reconnaissance and initial compromise, enabling them to move directly to exploitation, lateral movement, and ultimately monetization.
Role in the Ransomware Ecosystem
In the Ransomware-as-a-Service (RaaS) model, IABs are the initial entry providers. They sell access to affiliates, who then handle payload deployment, data exfiltration and extortion.
This compartmentalization:
- Reduces the operational risk for IABs
- Allows for greater specialization
- Enhances the efficiency of cybercriminal supply chains
Common Techniques Used by IABs
Initial Access Brokers (IABs) deploy a wide range of intrusion techniques to compromise their targets. These methods typically include spear-phishing, exploiting unpatched vulnerabilities, brute-force attacks on RDP/SMB, and credential theft. According to security researchers, IABs “rely on automated systems and tools that scour the internet to discover vulnerabilities,” such as exposed or unpatched VPNs and RDP servers.
In practice, many brokers execute broad phishing or spam campaigns and often rely on commodity malware—such as infostealers—to harvest usernames and passwords.
Cybereason highlights that IABs have increasingly exploited the rise in remote work by deploying trojans and ransomware loaders through unsecured RDP and VPN services, particularly those lacking multi-factor authentication (MFA). One study even found that unsecured RDP access was responsible for more than half of all ransomware incidents.
Brokers may also engage in brute-force attacks, password spraying, or, in some cases, simply purchase credentials from insiders.
Advanced Intrusion Methods
Some IABs employ more sophisticated tactics, exploiting zero-day vulnerabilities or critical, publicly known flaws. One well-known case involves the threat group Exotic Lily, which exploited the MSHTML vulnerability (CVE-2021-40444) in a large-scale phishing campaign. They distributed thousands of weaponized Office documents daily across dozens of organizations (more on this later).
After breaching a system, an IAB typically installs backdoors and establishes multiple access points—such as web shells or hidden user accounts—to ensure persistence. This strategy allows them to maintain access even if one method is detected and removed.
Emerging Threats: BYOVD and Antivirus Evasion
Recent ransomware groups, including affiliates of Kaseya and Akira, have adopted a new tactic known as BYOVD (Bring Your Own Vulnerable Driver). This involves abusing legitimate but vulnerable signed drivers to disable antivirus processes and evade detection.
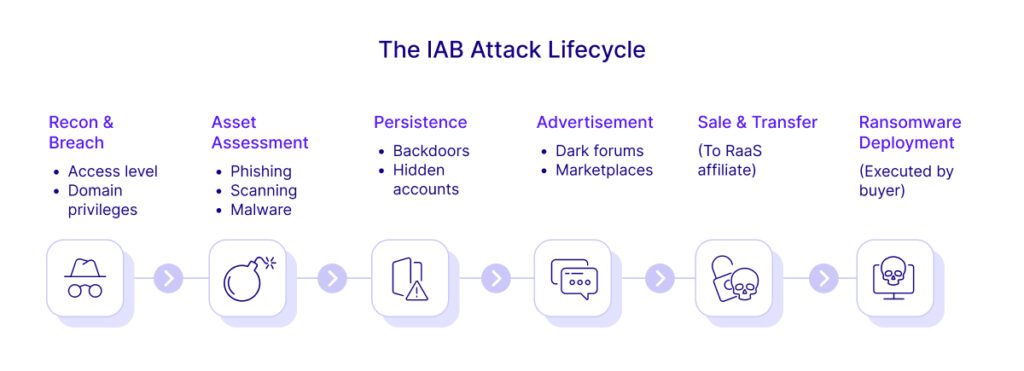
Typical IAB Attack Lifecycle
A simplified attack chain involving an Initial Access Broker typically proceeds as follows:
- Reconnaissance & Intrusion: The IAB scans for targets (phishing email lists, exposed RDP/VPN, vulnerable servers) and uses tools or malware to breach at least one system.
- Establish Persistence: Upon entry, the broker deploys backdoors (web shells, remote access tools) and creates alternative access accounts so the foothold survives credential resets or patches. Tools like Cobalt Strike, Metasploit or custom loaders (e.g. Bumblebee) are often staged to maintain stealthy control.
- Categorize & Advertise: The broker assesses the environment (level of privileges, network segment, potential data value) and then advertises the access to buyers. Ad listings might describe the company name or industry, access level (VPN, domain admin, etc.) and sale price.
- Monetization: A buyer (often a ransomware affiliate) purchases the access, pays in cryptocurrency, and immediately leverages it. The affiliate typically loads post-exploitation tools (Cobalt Strike beacons, remote management scripts) to perform lateral movement, data exfiltration and ultimately deploy ransomware across the network.
In a documented attack chain, Proofpoint researchers describe how an IAB might work with a ransomware actor: after an IAB sells access, the buyer used the broker’s backdoor to deploy a Cobalt Strike payload, quickly achieved full Active Directory compromise and then launched a widespread ransomware encryption within a matter of days.
Notably, IABs themselves do not encrypt files or negotiate ransom; their job ends when the access is sold. The affiliate proceeds to run the exploit, while the broker often disappears and looks for the next target.
Impact on Organizations
The rise of IABs dramatically alters an organization’s risk profile. By outsourcing the break-in phase, attackers dramatically shorten the time between compromise and ransom.
Reduced Dwell Time and Accelerated Attacks
One of the most alarming effects of the IAB model is the drastic reduction in “dwell time”—the period between initial compromise and the execution of an attack, such as ransomware deployment.
Incident reports reveal that attackers now spend only days, sometimes even hours, inside a network before triggering encryption, compared to the 40-day average observed in 2019. This leaves security teams with a shrinking window for detection, investigation, and containment.
Decoupled Attack Chain and Detection Gaps
The IAB-driven attack model separates different phases of a cyberattack between multiple actors. This segmentation complicates detection and response efforts.
For example, an organization might log a phishing email or credential theft weeks before the actual ransomware strike. By then, the original IAB has vanished and defenders are left with fragmented data that’s difficult to correlate. This disconnect can lead to misattribution, missed red flags or delayed incident response.
Increased Risk of Multiple, Simultaneous Attacks
With access sold to the highest bidder—or even multiple bidders—organizations face the possibility of suffering several types of attacks simultaneously or in quick succession.
Bitdefender and other analysts have warned that high-value industries such as finance and healthcare are especially vulnerable. In these sectors, a single compromised login can lead to multiple forms of cybercrime: ransomware deployment, data exfiltration, business email compromise, cryptojacking and more.
For example, one affiliate might encrypt systems for ransom, while another quietly exfiltrates personally identifiable information (PII) or intellectual property. The cumulative impact can be severe—financially and reputationally. Ransom payments, operational downtime, legal liabilities, and long-term brand damage all compound the cost of a breach.
Critical Infrastructure at Risk
The threat isn’t limited to private enterprises. Reports have surfaced of IABs selling access to critical infrastructure systems on dark web forums.
This raises the stakes dramatically, introducing the risk of disruptions to national utilities, transportation networks, or healthcare systems, with potential consequences far beyond monetary loss.
Prevention and Mitigation Strategies against Intital Access Brokers
Effectively defending against IABs begins with foundational cybersecurity practices that prioritize prevention, detection and response.
While IABs leverage a range of techniques to breach systems, organizations can greatly reduce their exposure by implementing layered defenses and improving visibility.
1. Enforce Multi-Factor Authentication (MFA)
MFA is a critical safeguard against credential theft. By requiring an additional factor beyond a password, MFA renders stolen credentials far less valuable.
It should be enforced across all remote access points, including VPNs, RDP gateways, email portals and cloud applications. Without MFA, IABs can easily exploit compromised credentials harvested via phishing or malware.
2. Patch Critical Vulnerabilities Promptly
Timely patching eliminates many of the vulnerabilities IABs rely on for access. Known flaws in Windows services, VPN appliances, and enterprise software are frequent targets.
Organizations should prioritize patching high-risk areas like RDP, SMB, OWA, Citrix and VMware environments. Removing these attack vectors denies IABs the easy wins typically discovered through automated internet scans.
3. Strengthen Credential Hygiene
Poor credential management is a common weakness exploited by IABs. Organizations should regularly rotate passwords, disable or remove unused accounts, and enforce complex password policies.
Credential-related anomalies—such as multiple failed login attempts or logins from unusual locations—should be actively monitored. Cymulate’s guidance on credential compromise outlines additional best practices to strengthen defenses.
4. Implement Network Segmentation and Least Privilege Access
Limiting internal lateral movement is crucial once an attacker gains an initial foothold. Segmenting the network and applying least-privilege access principles reduces the potential blast radius.
If a low-level account is compromised, proper segmentation ensures the attacker cannot easily pivot to high-value systems like domain controllers or financial servers.
5. Monitor User Behavior and Endpoint Activity
User Behavior Analytics (UBA) and endpoint monitoring can reveal subtle indicators of compromise. Actions such as the unexpected creation of new accounts, off-hours logins or unusual lateral movement should trigger automated alerts.
Most IAB campaigns rely on repeatable tactics—like credential stuffing or remote command execution—which deviate from normal user behavior and can be caught with anomaly detection.
6. Manage External Attack Surfaces Continuously
Because IABs often gain access through externally exposed services, continuous attack surface management is essential.
Organizations should conduct regular scans and manual penetration testing to identify vulnerable services, misconfigurations, or outdated components. For example, detecting an exposed or vulnerable driver like those used in BYOVD attacks can prevent an exploit before it occurs. Public-facing assets must be minimized, hardened or tightly monitored.
7. Prioritize Early Detection and Threat Hunting
Rapid detection is vital, as IAB-based compromises can quickly escalate to ransomware deployment. Security teams must prioritize log collection, real-time alerting, and centralized visibility into indicators of compromise such as suspicious process executions, credential dumps, or web shell activity.
Regular threat hunting exercises—especially those simulating known IAB tactics like the deployment of commodity loaders or tools like Cobalt Strike—enhance preparedness and response.
8. Proactive Defense and Exposure Validation
Defending against Initial Access Brokers (IABs) requires proactive, intelligence-driven strategies rather than reactive measures. Organizations must continuously assess their exposure and test their defenses against real-world tactics.
9. Use Threat Intelligence to Guide Priorities
Staying ahead starts with understanding the threat landscape. Monitoring dark web forums, credential leak sites, and IAB-related threat reports helps security teams identify emerging attack trends—such as popular RDP exploits or phishing lures—allowing for timely adjustments in defense priorities.
10. Continuously Assess and Reduce Attack Surface
Organizations must regularly scan their external-facing assets—like VPNs, websites, and RDP endpoints—to uncover misconfigurations or outdated components before attackers do. Exposure management platforms help automate this process. Regular validation ensures vulnerabilities are patched and access points are secure.
11. Emulate IAB Tactics to Test Defenses
Conducting “purple team” exercises—where defenders simulate IAB-style breaches—helps validate security controls. For instance, simulating a login with stolen credentials can reveal whether MFA and log alerts are working. Simulations using BYOVD techniques test the effectiveness of endpoint protection. This hands-on approach reveals blind spots in real-time defense.
12. Run Breach and Attack Simulations (BAS)
BAS platforms offer automated, realistic attack scenarios. Teams can simulate the full IAB kill chain—from phishing and credential dumping to lateral movement and ransomware deployment.
Mapping each scenario to frameworks like MITRE ATT&CK ensures comprehensive coverage. These exercises expose detection and response gaps (e.g., undetected Cobalt Strike activity) and improve organizational resilience over time.
Cymulate as a Proactive Defense Partner
Cymulate’s security validation platform is designed to help organizations defend against exactly these kinds of threats. For example:
- Credential-based attack simulations: Cymulate can simulate attacks that use compromised credentials (phishing, password spray, Pass-the-Hash) to test whether MFA and login monitoring are effective. It helps ensure stolen “cyber access logins” will not silently grant an attacker in.
- Access-vector validation (e.g. BYOVD): Cymulate’s customizable simulations include advanced techniques. Customers can run tests that mimic BYOVD exploits or other rootkit-level attacks to confirm their antivirus and EDR controls react properly.
- MITRE ATT&CK mapping: Each Cymulate scenario is mapped to ATT&CK techniques. This means an IAB-style breach (Tactic T1078: Valid Accounts, T1588: Steal Accounts) is tracked against specific ATT&CK IDs, making it easy to see which controls (detections and preventions) cover each technique.
- Exposure management: Cymulate’s Exposure Validation Platform continuously scans internet-facing assets for vulnerabilities and missing patches – essentially catching the same exposures that IABs might exploit. This continuous validation complements manual efforts and points out risky exposures in real time.
- Purple teaming: The platform facilitates red-team/blue-team exercises. Security teams can custom-build IAB-like attack chains and share results, ensuring both offensive techniques and defensive detections improve in tandem.
You can simulate a phishing delivery of a loader and verify whether the SOC detects the subsequent Cobalt Strike beacon. Or test that a fresh VM is hardened against known driver exploits (BYOVD). These proactive simulations validate that MFA is enforced, that lateral movement is monitored, and that behavioral analytics or SIEM rules catch anomalies – closing the gaps IABs need to operate.
What IABs Mean for Your Cybersecurity
IABs have become the unseen gatekeepers that fuel modern cybercrime. By specializing in infiltration and reselling access, they make it easier than ever for ransomware and fraud gangs to strike.
Organizations must adopt a defensive posture tailored to this reality: harden entry points, monitor for early signs of breach, and continuously test controls against IAB tactics.


