MITRE D3FEND
What is MITRE D3FEND Matrix? The Defensive Counterpart to ATT&CK Explained
MITRE D3FEND is a knowledge base of defensive cybersecurity techniques developed by the MITRE Corporation as a complementary framework to the popular MITRE ATT&CK matrix.
In essence, D3FEND (pronounced “defend”) provides a structured catalog of countermeasure techniques – the tools and methods defenders can use to mitigate or thwart adversary tactics and techniques.
Where MITRE ATT&CK maps how attackers operate (the offensive side), MITRE D3FEND maps how defenders can respond (the defensive side).
MITRE introduced D3FEND in mid-2021 (with funding support from the NSA) as a public, open framework to help organizations strengthen their security postures. D3FEND stands for “Detection, Denial, and Disruption Framework Empowering Network Defense,” reflecting its focus on enhancing an organization’s ability to detect threats, deny attackers success and disrupt malicious activities.
Modern Cybersecurity Defense: The Role of MITRE D3FEND
Modern cybersecurity defense requires understanding attacker operations and implementing a clear defensive strategy.
This is where MITRE D3FEND becomes invaluable. D3FEND helps organizations structure and improve their defensive strategies by mapping countermeasures to known attacker behaviors.
This approach builds upon the MITRE ATT&CK framework, shifting the focus to the defender's side. By examining an ATT&CK technique (such as OS Credential Dumping), security teams can consult D3FEND for defensive techniques or controls to counter that behavior. This creates a common language for defensive measures like ATT&CK’s language for attacker tactics.
D3FEND provides a comprehensive list of defensive techniques, enabling security architects and blue teams to cover all aspects of defense.
It highlights potential gaps in an organization’s defenses by aligning defensive techniques with the corresponding offensive techniques from ATT&CK. This ensures that defensive strategies are as organized and robust as attacker methodologies.
D3FEND is vendor-neutral and technology-agnostic, meaning it focuses on what needs to be done, rather than how it’s achieved by any specific product. Organizations can use D3FEND to evaluate security tools without bias.
When selecting a product, a security architect can assess which D3FEND techniques the product addresses. MITRE designed D3FEND to cut through marketing jargon and define the technical functions (capabilities) that defensive tools offer, simplifying comparisons between solutions and ensuring that all critical defensive functions are covered in the security architecture.
Structure of the MITRE D3FEND Matrix and Core Categories
The MITRE D3FEND framework is organized as a matrix of defensive techniques, similar to how ATT&CK maps offensive techniques.
However, D3FEND focuses on defensive tactics or stages. Each defensive tactic represents a high-level goal that defenders aim to achieve during an attack, with specific techniques outlining how to achieve those goals. D3FEND also provides related tools, standards and Digital Artifacts linking offensive and defensive concepts.
Core Categories (Defensive Tactics) in D3FEND
D3FEND consists of one preparatory stage called "Model," followed by five main defensive tactic categories. These categories help guide defense actions during various stages of an attack.
1. Model: Know Your Environment
This initial stage involves understanding all assets, configurations and behaviors in your environment.
Techniques here include discovering and mapping assets, baselining configurations and identifying normal patterns. Modeling the environment forms the foundation for the remaining defense actions.
2. Harden: Strengthen Systems and Reduce Attack Surface
The Harden category focuses on reinforcing security posture and eliminating vulnerabilities before an attack occurs. Techniques include Application Hardening, Credential Hardening and Platform Hardening, which aim to lock down systems and make them resilient against attacks.
3. Detect: Identify Malicious Activity Quickly
The Detect category focuses on spotting intrusions or malicious behavior in real-time. This includes techniques like File Analysis, User Behavior Analysis and Network Traffic Analysis, which help identify threats and provide timely alerts for faster responses.
4. Isolate: Contain the Threat and Limit Lateral Movement
The Isolate category involves containing or quarantining malicious activity to prevent attackers from spreading. Techniques include Network Isolation and Execution Isolation, which limit attackers' ability to move laterally and cause further damage.
5. Deceive: Misdirect and Frustrate the Adversary
The Deceive category uses deception techniques like honeypots, decoy accounts and fabricated data to mislead attackers and gather intelligence on their methods. This tactic disrupts attackers' operations and increases the likelihood they reveal themselves.
6. Evict: Remove the Adversary and Recover
The Evict category focuses on eradicating threats once identified. Techniques such as Credential Eviction and Process Eviction remove compromised accounts and processes, ensuring attackers are expelled and systems are restored securely.
A Holistic Defensive Lifecycle
These tactics together form a defensive lifecycle that aligns with the cyber kill chain: model and harden your environment, detect intrusions, isolate and deceive to limit damage and evict the threat to recover. Not all tactics are used in every scenario, but they ensure defenders have techniques for each phase of an attack.
Visualizing the D3FEND Matrix
In the D3FEND matrix, each category (Harden, Detect, Isolate, Deceive, Evict) has specific techniques listed underneath it, such as Application Hardening, Decoy Account and Honeytoken.
Each technique is identified by a D3FEND code and includes descriptions and links to related ATT&CK techniques.
The Digital Artifacts ontology defines objects like files, credentials, and network traffic, showing how ATT&CK techniques are connected to defensive actions. This visual structure makes D3FEND a valuable cyber defense matrix, providing a comprehensive guide for securing systems.
MITRE D3FEND vs. MITRE ATT&CK
MITRE D3FEND and MITRE ATT&CK are complementary frameworks, but they focus on different aspects of cybersecurity. Below are the key distinctions between the attacker-focused MITRE ATT&CK and the defender-focused MITRE D3FEND.
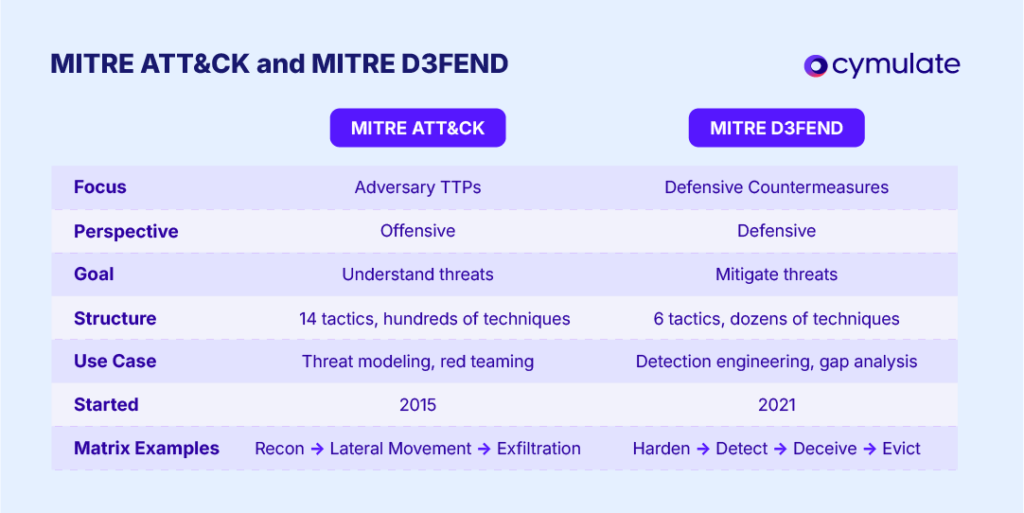
Focus and perspective
MITRE ATT&CK focuses on adversary behavior, documenting tactics, techniques and procedures (TTPs) used by attackers at various stages of an intrusion.
D3FEND, however, catalogs defensive actions, describing the techniques defenders can use to counter those attacks. ATT&CK provides the offensive lens (what attackers do), while D3FEND provides the defensive lens (how defenders can respond).
Objective
The goal of ATT&CK is to understand and classify how attacks are carried out, enabling threat intelligence, red teaming and improving detection capabilities.
D3FEND, on the other hand, helps organizations mitigate attacks, answering the question, “How do we stop or lessen the impact of technique X?”— a question that ATT&CK alone does not address.
Content and structure
ATT&CK is organized into multiple matrices, covering general IT environments (Enterprise ATT&CK), Mobile and ICS. It defines 14 high-level tactics (e.g., Reconnaissance, Lateral Movement, Exfiltration) under which hundreds of techniques are documented.
D3FEND, in contrast, has a single matrix focused on enterprise defense, defining fewer defensive tactics (such as Harden, Detect, Isolate, Deceive, Evict), each with dozens of defensive techniques. D3FEND also includes the Digital Artifacts knowledge base, linking offensive and defensive concepts, which ATT&CK lacks.
Usage in practice
ATT&CK is widely used for threat modeling, adversary emulation, purple teaming and assessing detection coverage. Security teams use ATT&CK to identify which techniques their controls can detect or to simulate attacks during red team exercises.
D3FEND is primarily used to design and evaluate defenses. Security architects use D3FEND to identify the defensive techniques to implement for specific threats, such as ensuring solutions are in place for credential Hardening in response to techniques like credential dumping from ATT&CK. D3FEND is also used for detection engineering and gap analysis to ensure defenses are comprehensive.
Maturity and adoption
MITRE ATT&CK, released in 2015, has become a de facto industry standard for cyber threat knowledge, widely adopted across cybersecurity products and programs. D3FEND, however, is newer, with its beta released in mid-2021 and is still gaining traction.
It is an evolving framework, with MITRE actively seeking community feedback. Many organizations are just beginning to explore how to leverage D3FEND, often alongside ATT&CK, to build a balanced, threat-informed defense strategy.
Threat-Informed Defense: Aligning D3FEND with the Cyber Kill Chain
One of the main advantages of using frameworks like D3FEND (alongside ATT&CK) is enabling a threat-informed defense strategy. This means making security decisions based on real threat behaviors and intelligence—essentially, understanding the enemy and preparing accordingly.
MITRE D3FEND supports this approach by linking known attacker techniques (threats) to specific defensive measures. By aligning defensive actions with adversary tactics, organizations can be prepared for threats at each stage of an attack.
A useful way to conceptualize this is by using the cyber kill chain, which breaks down an attack into stages like Reconnaissance, Weaponization, Delivery, Exploitation, Installation, Command & Control and Actions on Objectives. Security teams can map D3FEND tactics to these phases to ensure appropriate defenses at each step.
Early-Stage (Reconnaissance/Delivery) – Harden and Model
Before an attacker breaks in, defenders should focus on modeling their environment and hardening systems to eliminate weaknesses.
Techniques such as surface reduction (removing unnecessary services) and secure configuration enforcement directly thwart Reconnaissance and Exploitation efforts, making it harder for attackers to find targets. These hardening measures align with the early kill chain steps by denying adversaries footholds.
Mid-Stage (Exploitation/Lateral Movement) – Detect and Deceive
When an attacker exploits vulnerabilities or attempts lateral movement, D3FEND’s Detect techniques come into play. For example, process monitoring or file analysis can detect malicious payloads in the Execution phase.
In the Lateral Movement phase, network traffic analysis or authentication logging can uncover suspicious access attempts. Simultaneously, Deception techniques like using a fake database (decoy) can mislead the attacker, pulling them away from real assets. This proactive approach not only watches for threats but also sets traps to delay or disrupt the adversary.
Late-Stage (Actions on Objectives) – Isolate and Evict
If an attacker reaches the final phase (e.g., data collection or persistence), defenders must contain and eradicate the threat. Isolation techniques, like cutting off C2 communication, align with the containment step in incident response.
Eviction tactics, such as removing malware or rebuilding systems, ensure that attackers are expelled before completing their objectives (e.g., data exfiltration). By mapping these tactics to kill chain stages, defenders ensure they are prepared for each phase of an attack lifecycle.
Continuous Testing and Adaptive Defense
Threat-informed defense also involves testing and adjusting defenses based on emerging threat trends. Since D3FEND is built on real offensive techniques, it enables organizations to align their defenses with the most relevant threats.
For example, if threat intelligence indicates a rise in PowerShell-based exploitation, defenders can look to D3FEND for countermeasures like Script Execution Monitoring under Detect or Application Whitelisting under Harden. This allows D3FEND to operationalize an adaptive defense that evolves with the threat landscape.
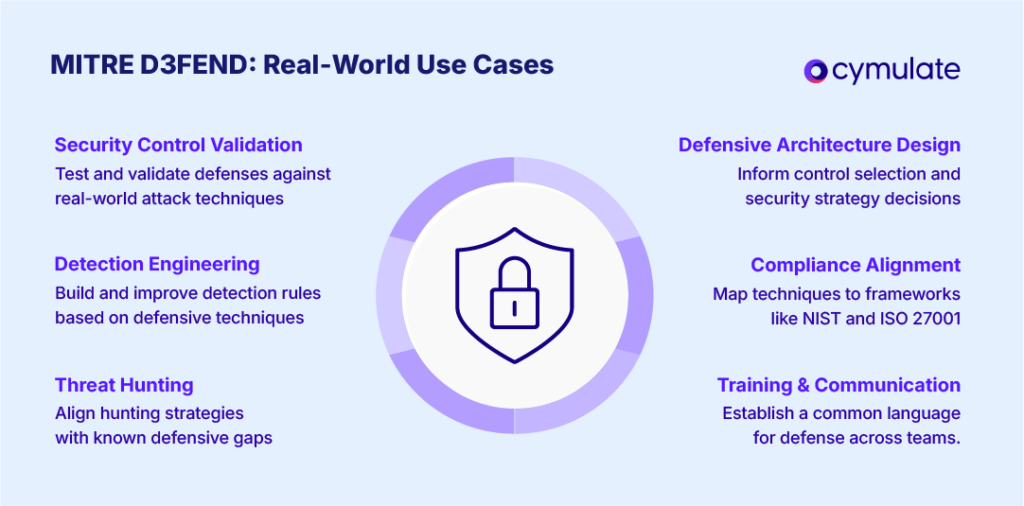
Use Cases and Benefits of MITRE D3FEND in the Real World
Implementing MITRE D3FEND offers several benefits for cybersecurity teams across various use cases:
- Guiding Defensive Architecture & Control Selection: D3FEND helps security architects choose the right defensive technologies by mapping techniques to necessary security controls, ensuring gaps are avoided and resources are optimally allocated.
- Detection Engineering and SOC Effectiveness: SOC teams can use D3FEND to develop comprehensive detection coverage by translating defensive techniques into monitoring use cases. This leads to improved detection capabilities and faster response times during attacks.
- Security Control Validation (Breach and Attack Simulation): Organizations can use D3FEND to validate their security controls through purple team exercises or breach-and-attack simulations, ensuring defensive mechanisms are effective against real attacks.
- Threat Hunting and Analytics: Threat hunters can align their efforts with D3FEND’s defensive techniques and artifacts to better identify and address gaps in security. D3FEND guides where to look for clues when attack techniques are attempted.
- Common Language and Training: D3FEND standardizes the language of defensive practices, aiding training and communication across teams and helps provide a high-level measure of defense posture.
- Integration with Other Frameworks and Compliance: D3FEND aligns with frameworks like NIST and ISO 27001, helping organizations demonstrate compliance and integrate defense measures into risk management tools.
In practice, D3FEND helps organizations rationalize security investments and improve their defensive posture.
Cymulate’s Value Proposition: Operationalizing ATT&CK for Exposure Management
Cymulate is a continuous threat exposure management (CTEM) platform that helps organizations implement and validate the MITRE ATT&CK framework through continuous assessments and threat simulations. It provides actionable insights for improving security defenses by simulating real-world attacks and testing defense effectiveness.
Adversary emulation and TTP Simulation
Cymulate emulates adversary behaviors based on MITRE ATT&CK tactics and techniques, simulating real attack sequences to test how defenses detect or block these threats. By aligning simulations with ATT&CK, organizations can assess their defenses’ ability to prevent specific attacks, such as phishing or malware execution.
By emulating adversary behaviors and testing them against their defenses, organizations can find their gaps and focus on optimizing their controls with Cymulate’s remediation guidance.
Integration with MITRE ATT&CK
Cymulate maps security validation with the MITRE ATT&CK framework, giving security teams clear insights into which tactics were executed and whether defenses stopped them. Cymulate has meticulously designed scenarios that imitate the specific tactics and techniques outlined by MITRE. Whether it's credential harvesting, privilege escalation, or data exfiltration, Cymulate simulations provide an authentic feel of how real-world adversaries operate.
"The Cymulate MITRE ATT&CK Heatmap helps us easily visualize our gaps and coverage of the MITRE framework. We quickly understand if there are specific MITRE techniques or sub-techniques that we haven’t been able to detect, so we know exactly where we need to allocate our resources for better protection"
- Markus Flatscher, Senior Security Manager, RBI
Continuous Improvement and Metrics
Cymulate tracks progress over time by measuring how many ATT&CK tactics and techniques are detected by defenses, highlighting strengths and weaknesses backed by concrete evidence of security effectiveness. This continuous testing and feedback loop allows organizations to stay updated and refine their defenses as new threats emerge.
Cymulate brings the MITRE ATT&CK framework to life by simulating real-world threats, validating defenses and providing actionable insights for continuous improvement. It helps organizations to adopt a threat-informed defense strategy, ensuring their security posture is resilient, adaptive and always evolving.