Endpoint Protection Platform
An Endpoint Protection Platform (EPP) is a security solution that protects devices such as laptops, mobile phones, and servers from cyber threats. It detects, prevents, and responds to attacks before they cause harm. Businesses use EPP to safeguard sensitive data and maintain smooth operations.
EPP is essential because cyber threats are constantly evolving. Attackers target endpoints to steal data, install ransomware, or disrupt systems. Without strong protection, organizations risk financial loss, reputational damage, and operational downtime.
The Main Functions and Objectives of an Endpoint Protection Platform
An EPP is designed to secure devices from cyber threats. It actively prevents attacks, detects suspicious activity, and responds to security incidents.
Key functions of an EPP include:
- Advanced threat prevention – blocks malware, ransomware, and phishing attacks before they cause harm.
- Real-time monitoring – continuously scans devices for unusual behavior.
- AI and machine learning – identifies emerging threats without relying solely on known malware signatures.
- Endpoint detection and response (EDR) – investigates and neutralizes advanced attacks.
- Data protection – prevents unauthorized access and data leaks.
- Cloud integration – ensures security across remote and hybrid work environments.
EPP’s main objective is to provide proactive security. Instead of reacting after an attack, it stops threats before they spread. It also helps organizations meet compliance requirements and protect customer data.
What to Look for in an Endpoint Protection Platform
Choosing the right EPP from endpoint protection platform examples is critical for securing devices against cyber threats. Here are key features to consider:
1. Threat detection capabilities
A strong EPP should use machine learning, behavioral analytics, and real-time scanning to detect threats before they cause harm. It must identify known malware, zero-day attacks, and suspicious activities without slowing down devices.
2. Ease of deployment & management
Look for a cloud-based solution for easier updates and scalability. On-premise options work for organizations needing full control. The platform should integrate smoothly with existing IT infrastructure and support remote management.
3. Integration with other security tools
Your EPP should work with SIEM, SOAR, and EDR solutions. Seamless integration ensures better visibility, faster threat response, and a more cohesive security strategy.
4. Automation & AI
Automation reduces manual workload and improves response times. AI-powered tools help prioritize real threats, cutting down on alert fatigue. The EPP should automate threat investigation and remediation.
5. Compliance & Regulatory standards
A good EPP helps businesses meet General Data Protection Regulation (GDPR), The Health Insurance Portability and Accountability Act (HIPAA), PCI-DSS, and other regulations. It should offer auditing, reporting, and data protection features to ensure compliance.
By focusing on these features, organizations can enhance security, streamline operations, and stay ahead of cyber threats.
Endpoint Protection Platform vs. Endpoint Detection and Response
Both EPP and EDR protect endpoints, but they serve different purposes. Understanding their differences helps organizations build a stronger security strategy.
Key differences are the following:
- Endpoint protection platform focuses on preventing attacks. It blocks malware, ransomware, and phishing attempts before they cause damage. EPP solutions use antivirus, machine learning, and behavioral analysis to detect threats early.
- Endpoint detection and response goes further. It provides detection, investigation, and response capabilities. Instead of just blocking threats, EDR monitors activity, identifies suspicious behavior, and helps security teams analyze and respond to advanced attacks.
Why you need both
A strong security strategy requires both EPP for prevention and EDR for deeper threat detection and response.
- EPP reduces risk—stops most threats at the entry point.
- EDR adds visibility—helps detect and investigate advanced attacks.
Together, they close security gaps: EPP prevents, while EDR detects and mitigates anything that slips through.
By combining EPP and EDR, organizations improve threat protection, reduce downtime, and strengthen their cybersecurity posture. Prevention alone isn’t enough, and detection without prevention leads to unnecessary risk. A layered approach ensures maximum security.
EPP vs. Traditional Antivirus
Endpoint protection platforms and traditional antivirus both aim to protect devices from cyber threats. However, EPP offers a more advanced, proactive approach compared to traditional antivirus software.
| Antivirus vs EPP: Key Difference | Traditional Antivirus | Endpoint Protection Platform |
| Threat detection | Traditional antivirus relies on signature-based detection. It blocks known threats but struggles with new, unknown malware. | EPP uses machine learning, behavioral analysis and AI to detect both known and unknown threats in real- |
| Protection scope | Antivirus mainly focuses on individual devices, scanning files and programs for malware. | EPP secures entire networks, covering multiple endpoints, including laptops, mobile devices |
| Prevention vs. Response | Antivirus only blocks threats when they are detected. | EPP goes further by preventing, detecting |
| Cloud integration and management | Antivirus requires manual updates and local installations. | EPP often operates from the cloud, providing centralized management and automatic updates across all endpoints. |
| Zero-day threat protection | Antivirus is ineffective against new, unknown threats until a signature update is available. | EPP proactively identifies and stops zero-day attacks using AI and behavioural analysis, even before security patches exist. |
| Insider threat detection | Antivirus focuses on external threats like malware and viruses. | EPP detects suspicious behavior from insiders, such as unauthorized access, unusual file transfers, or credential misuse. |
Traditional antivirus alone is not enough against today’s evolving cyber threats. Organizations need EPP’s advanced detection, automation, and cloud-based management to stay secure. It reduces risk, simplifies security management, and provides better protection against modern attacks.
How Cymulate Can Help
An EPP is essential, and Cymulate, as an endpoint security solution, helps organizations validate, test, and optimize their EPP to ensure maximum security.
Validating the effectiveness of EPP solutions: Cymulate Endpoint Security Validation allows businesses to test whether their EPP blocks threats effectively. It simulates real-world attacks to check if security controls are detecting and preventing threats as they should.
This ensures your EPP is delivering the protection it promises.
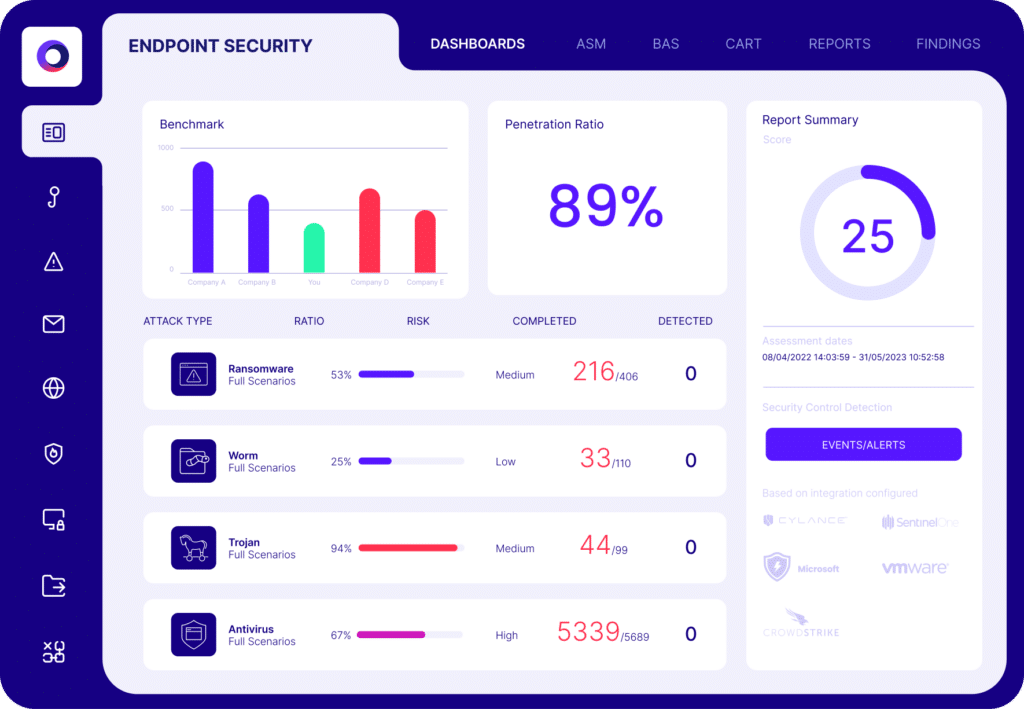
- Simulating real-world threats: Cybercriminals constantly evolve their tactics. With Cymulate Breach and Attack Simulation (BAS), organizations can test their EPP against ransomware, advanced malware, and phishing attacks in a controlled environment. This helps measure how well the platform responds to actual threats before an attack happens.
- Closing security gaps: Even next-generation endpoint protection platforms are not foolproof. When vulnerabilities appear, Cymulate provides actionable insights and clear remediation steps. Instead of guessing where security weaknesses are, organizations get detailed reports on how to strengthen their defenses. This proactive approach helps businesses stay ahead of attackers.
- Supporting both EPP and EDR assessments: A strong security strategy includes both prevention (EPP) and detection/response (EDR). Cymulate enables organizations to test both to ensure they are working together effectively.
By validating preventive controls (EPP) and detective controls (EDR), businesses can build a more resilient security posture.
Security isn’t about hoping your tools work—it’s about proving they do. Cymulate gives organizations the confidence that their EPP is effective, identifies weaknesses, and helps continuously improve endpoint protection.
By testing, validating, and optimizing security measures, businesses can stay one step ahead of cyber threats.

