Vulnerability Management Lifecycle
With the National Institute of Standards and Technology (NIST) adding thousands of new vulnerabilities to its national database each month, a reactive approach to security is not sustainable. A structured vulnerability management lifecycle (VML) provides a repeatable framework for identifying, prioritizing and remediating risks before they can be exploited.
This article will explore the key steps of the cycle and explain how a proactive approach to vulnerability management mitigates risks such as data breaches while strengthening regulatory compliance.
Key highlights:
- A vulnerability management lifecycle framework replaces reactive patching with a repeatable, proactive security process.
- Standardized vulnerability management process steps allow security teams to implement a high-impact, risk-based strategy.
- A complete vulnerability lifecycle tracks every exposure stage to ensure no discovery goes ignored.
- The Cymulate Continuous Security Validation (CSV) suite automates simulations to verify that the vulnerability management cycle effectively remediates threats.
What is the vulnerability management lifecycle?
The vulnerability management lifecycle is a continuous, multi-stage process designed to identify, evaluate and remediate security weaknesses across an organization's digital assets. Unlike a one-time vulnerability scan, the lifecycle is a repeatable framework that ensures security teams manage risks in real time, covering the complete progression of a vulnerability — from initial discovery to the validation of its fix.
What are the steps in the vulnerability management lifecycle?
The vulnerability management lifecycle steps are an iterative framework designed to provide a structured approach to maintaining a resilient defense against cyber threats.
Before starting the VML process, you need to define the program’s scope and objectives, establish security policies, specify service-level agreements (SLAs) for remediation timelines and identify critical assets to ensure the lifecycle aligns with organizational risk tolerance. Then you can begin scanning for threats.
Follow these six vulnerability management process steps:
Step 1: Assessment
This phase involves identifying assets and risks within the organization, such as hardware, software and network components. Tools like vulnerability scanners, inventory management systems and penetration tests are used to detect known vulnerabilities.
Step 2: Prioritization
In this phase, identified vulnerabilities are evaluated based on their technical severity, exploitability and potential business impact. According to the Verizon 2025 DBIR report, vulnerability exploitation as an initial access vector has surged by 34% year-over-year.
Teams often use the common vulnerability scoring system (CVSS) and threat intelligence to prioritize vulnerabilities that are high-risk and exploitable first, ensuring that remediation efforts align with the organization's actual exposure risk.
Step 3: Remediation/mitigation
Once vulnerabilities are prioritized, efforts to validate remediation involve applying patches, making configuration changes or implementing other security controls to mitigate the risks associated with the identified vulnerabilities. Remediation must be done in a timely manner to address the high-priority vulnerabilities.
Step 4: Validation
After remediation efforts, verification helps ensure that vulnerabilities have been effectively addressed. By using automated tools to rescan or test systems to confirm that vulnerabilities are no longer present, organizations can ensure they are compliant with regulatory standards.
Step 5: Reporting and Monitoring
The next-to-last phase includes documenting findings, remediation efforts and continuous monitoring of systems for any new vulnerabilities. Regular reporting helps maintain visibility and informs stakeholders about any changes in the cybersecurity posture.
Step 6: Improvement
This final phase of the VML allows for teams to make note of any areas of improvement in the vulnerability management process, adjust policies, tools and procedures based on previous assessments. This critical step will help keep teams sharp and agile in the event of an attack.
Benefits of vulnerability lifecycle management
As systems continue to become more complex and interconnected, vulnerabilities can emerge in a variety of forms, from software bugs to misconfigured settings. To safeguard sensitive data, maintain operational integrity and protect an organization’s reputation, an effective VML is essential.
Here are seven key benefits of implementing a VML:
- Proactive risk mitigation: The primary goal of the VML is to proactively identify and address vulnerabilities before they can be exploited by attackers. By regularly scanning systems and applications, organizations can uncover potential weaknesses, allowing them to implement fixes or mitigations quickly. Having a proactive approach reduces the risk of data breaches, financial loss and reputational damage.
- Prioritization of resources: Since not all vulnerabilities are created equal in terms of risk, the VML helps organizations assess and prioritize vulnerabilities based on factors like severity, exploitability and potential impact on the business. This prioritization helps ensure that the most critical high-risk vulnerabilities are addressed first.
- Strengthened compliance: Remaining compliant and staying up to date with constantly changing regulations such as Payment Card Industry Data Security Standard (PCI DSS), Health Insurance Portability and Accountability Act (HIPAA) and General Data Protection Regulation (GDPR) means avoiding costly fines and penalties as well as protecting an organization's reputation. The VML helps organizations comply with these regulations while providing documentation and reporting capabilities that demonstrate compliance to auditors.
- Continuous improvement: With new potential threats constantly emerging, the VML helps to promote a culture of continuous improvement by encouraging organizations to revisit their processes, tools and strategies. Regular process reviews help identify gaps and potential areas for improvement, which help an organization remain resilient and ahead of evolving threats.
- Incident response preparedness: Organizations can significantly improve their incident response preparedness by maintaining an active vulnerability management program. Knowing which vulnerabilities exist and how they have been addressed allows teams to respond more effectively in the event of an attack, which in turn allows for quicker recovery times.
- Building a security culture: Instituting a vulnerability management cycle encourages a security-first culture within an organization. Employees begin to understand the weight of becoming more vigilant about security best practices through training and awareness programs that help strengthen the overall security posture.
- Long-term cost savings: Though establishing any kind of security program upfront has costs, in the long term, when run effectively, the cost savings can be substantial. By preventing a potential breach and reducing the likelihood of a costly incident, an organization is saving money on recovery efforts and resources, legal fees or regulatory fines and potential reputational damage.
Aligning global security frameworks with the vulnerability management lifecycle
Vulnerability lifecycle management serves a critical dual purpose: hardening security while satisfying the rigorous requirements of global regulatory frameworks. Standards such as NIST, PCI DSS and HIPAA establish the baseline for how data must be protected, requiring organizations to demonstrate consistent oversight and proactive mitigation of their exposure risks.
Here’s a closer look at the correlation between VM technical security measures and the core objectives of international regulatory standards:
| Security framework | Core regulatory mandates | Vulnerability management alignment |
| PCI DSS | Continuous protection against vulnerabilities and malicious software | Remediation and validation verify that critical patches are applied within mandated windows to secure cardholder data. |
| HIPAA | Periodic risk analysis and implementation of technical safeguards | Assessment and prioritization provide the technical documentation required for formal risk evaluations and information protection. |
| NIST CSF | Asset identification, risk assessment and continuous monitoring | Preparation and remediation fulfill the protocols for identifying critical assets and establishing information protection policies. |
| GDPR | Regular testing, assessment and evaluation of technical security effectiveness | Monitoring and improvement demonstrate a formal process for identifying gaps and maintaining resilience against evolving threats. |
Challenges in the vulnerability lifecycle
Growing pains are normal for any organization, but managing complex organizations and the rise in vulnerabilities, especially amid cloud security challenges, is critical when establishing a sustainable strategy. The range of threats increases with the size of the organization. For example, larger organizations can struggle with the sheer volume of vulnerabilities found in scans and then must remediate before being exploited.
With increased volumes comes the challenge of prioritizing real risks, vulnerabilities and resources accordingly. Tool effectiveness and the potential for overlap could lead to confusion and inefficiencies. This may also create a skills gap if tools are not being used effectively.
In each step of the vulnerability management lifecycle, challenges may present themselves. However, maintaining a security-minded culture helps overcome these obstacles by leveraging a strategic approach, clear communication and ongoing training.
The advantage of automated vulnerability management
Automated vulnerability management leverages tools and technologies to streamline and enhance the VML from discovery to monitoring. There are several key benefits of automation:
- Efficiency and speed: Automating repetitive tasks, such as scanning and reporting, saves time and resources, allowing security teams to focus on more critical vulnerabilities. Automated scans can quickly identify vulnerabilities, enabling faster responses to emerging threats.
- Consistency: Implementing automated processes helps ensure uniformity in vulnerability assessments and remediation techniques, reducing the risk of human error and increasing accuracy.
- Real-time monitoring: Scanning and monitoring help organizations stay updated and ahead of new vulnerabilities and threats before they occur.
- Prioritization: Scoring and prioritizing vulnerabilities automatically, based on risk factors, helps teams focus on the most critical issues first.
Streamline the vulnerability management process with Cymulate
It would be ideal to think every security team could stay steps ahead of an adversary, but in today’s hyper-connected environment, manual processes cannot keep pace. Organizations are adopting what Gartner identifies as a top strategic trend for 2026: Preemptive cybersecurity. This framework shifts the focus from reactive defense to proactive prediction.
The Cymulate Continuous Security Validation suite includes:
- Breach and attack simulation (BAS): Automated multi-vector simulations designed to test the effectiveness of security controls across the entire infrastructure
- Continuous automated red teaming (CART): Autonomous, end-to-end campaigns that mimic sophisticated adversaries to find and validate exploitable attack paths
- Attack surface management (ASM): Continuous discovery and mapping of external and internal assets to identify blind spots and potential entry points
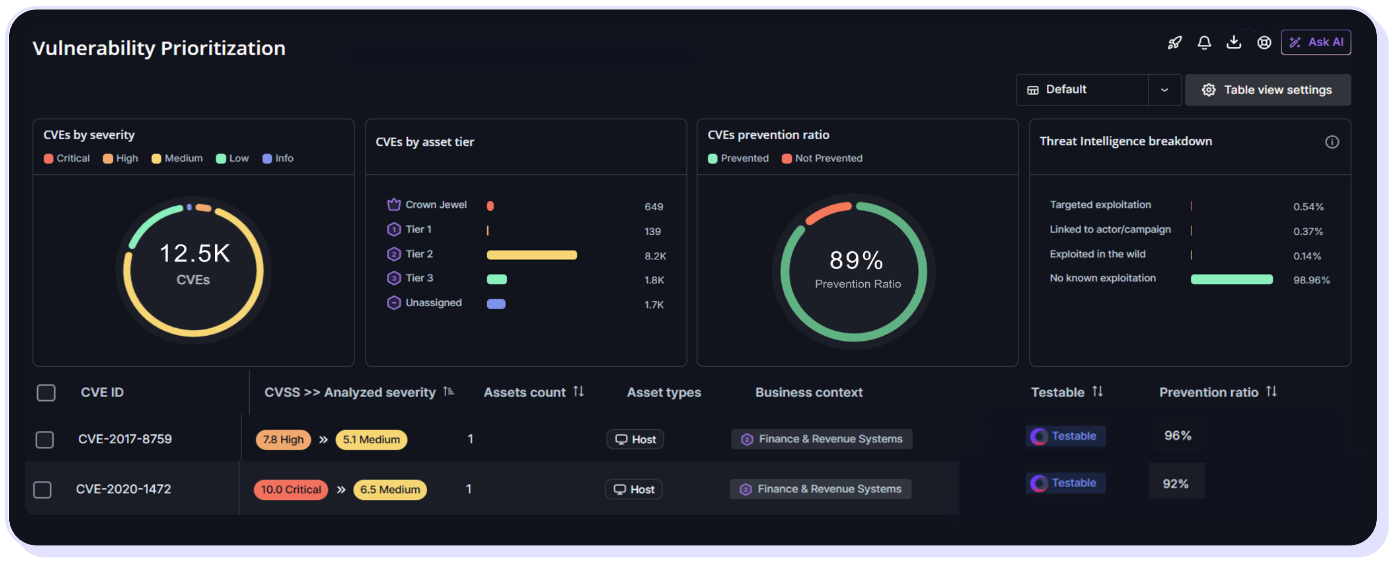
- Vulnerability prioritization: Correlation of simulation findings with vulnerability data to rank risks based on actual exploitability rather than theoretical common vulnerability scoring systems.
With the flexibility to scale to any size organization at any pace, the Cymulate Security Validation platform can help your organization make manual penetration testing a thing of the past.
Book a demo and discover how Cymulate can transform your vulnerability management lifecycle from a reactive manual process into a continuous, automated defense strategy.

