Cymulate alternatives
& comparisons
Unified exposure validation that filters out the noise so you can focus on the exploitable.
No Slack account needed
Cymulate security validation provides advanced security testing for every blue and red team.
Increase in team efficiency
by focusing on the exploitable
Reduction in manual
SecOps tasks
Reduction in vulnerabilities between pen tests
AttackIQ
AttackIQ delivers automated security validation through attack simulation, but fails to match Cymulate innovation, threat coverage and ease of use. Cymulate delivers the industry leading threat scenario library and AI-powered capabilities to streamline workflows and accelerate your organization’s security posture.
Use Case | Capabilities | AttackIQ | |
Defensive Posture Optimization | Security controls integrations | ||
Threat-informed defenses | |||
Scale Offensive Testing | Attack scenario creation workbench | ||
Automation, extensible testing | |||
Attack paths | |||
Exposure Awareness | Automated & continuous testing | ||
Always current attack scenario knowledge |
Mandiant Security Validation
Mandiant Security Validation is one of the original BAS platforms; however, the product has become outdated with very little innovation in the past 5 years. Cymulate continually innovates to meet market demands, powers the platform with AI and automation and has expanded into the exposure management market as a grid leader.
Use Case | Capabilities | Mandiant | |
Defensive Posture Optimization | Security controls integrations | ||
Threat-informed defenses | |||
Scale Offensive Testing | Attack scenario creation workbench | ||
Automation, extensible testing | |||
Attack paths | |||
Exposure Awareness | Automated & continuous testing | ||
Always current attack scenario knowledge |
NetSPI
NetSPI is an excellent choice if you are looking for a penetration testing as a service (PTaaS) vendor. But if you want to independently assess and strengthen your organization’s defenses, NetSPI’s approach to automated exposure validation will limit you. Cymulate is recognized by both Gartner and G2 as a leader in exposure validation, with a track record of continuous innovation.
Use Case | Capabilities | NetSPI | |
Defensive Posture Optimization | Security controls integrations | ||
Threat-informed defenses | |||
Scale Offensive Testing | Attack scenario creation workbench | ||
Automation, extensible testing | |||
Attack paths | |||
Exposure Awareness | Automated & continuous testing | ||
Always current attack scenario knowledge |
Pentera
Threat exposure validation requires optimizing defense, scaling offensive testing and increasing exposure awareness. While Pentera is useful for identifying security gaps with attack path validation, it lacks the depth that Cymulate provides to fully assess and strengthen defenses.
Use Case | Capabilities | Pentera | |
Defensive Posture Optimization | Security controls integrations | ||
Threat-informed defenses | |||
Scale Offensive Testing | Attack scenario creation workbench | ||
Automation, extensible testing | |||
Attack paths | |||
Exposure Awareness | Automated & continuous testing | ||
Always current attack scenario knowledge |
Picus Security
Picus might be suitable if you’re looking for a breach and attack simulation (BAS) vendor with an on-prem option, but if you’re looking for the most complete exposure validation platform that covers the full-kill chain, as well as cloud control validation, Cymulate is the better choice.
Use Case | Capabilities | Picus Security | |
Defensive Posture Optimization | Security controls integrations | ||
Threat-informed defenses | |||
Scale Offensive Testing | Attack scenario creation workbench | ||
Automation, extensible testing | |||
Attack paths | |||
Exposure Awareness | Automated & continuous testing | ||
Always current attack scenario knowledge |
Scythe
Scythe might be suitable for the most advanced red teams to build custom attack campaigns, but security teams who care about fixing the issues and actually eliminating the exposure trust Cymulate for the most complete exposure validation platform that drives actionable remediation and automated mitigation.
Use Case | Capabilities | Scythe | |
Defensive Posture Optimization | Security controls integrations | ||
Threat-informed defenses | |||
Scale Offensive Testing | Attack scenario creation workbench | ||
Automation, extensible testing | |||
Attack paths | |||
Exposure Awareness | Automated & continuous testing | ||
Always current attack scenario knowledge |
Unified Validation
Complete Exposure Validation
Best-in-class exposure security validation in a single platform allows you to optimize security controls, test for new threats and evaluate response capabilities. Put validation at the heart of exposure management, so you can focus on what’s truly exploitable in your environment.
Simple Automation
Advanced testing for any blue or red teamer to run and customize offensive testing with templates, best practices and AI assistant.

Full Kill-Chain Visibility
Wide range of full kill-chain attacks simulating threat exposure to ransomware, malware, APT groups, CVEs, MITRE TTPs and more.
Actionable & Automated Remediation
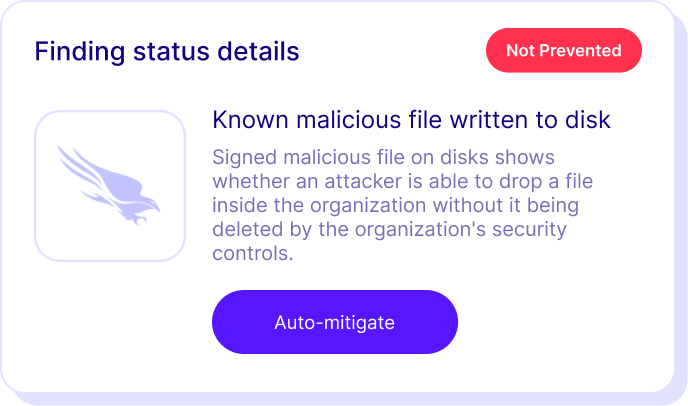
Open platform that integrates with leading security controls to push IoC updates and build custom detection rules.
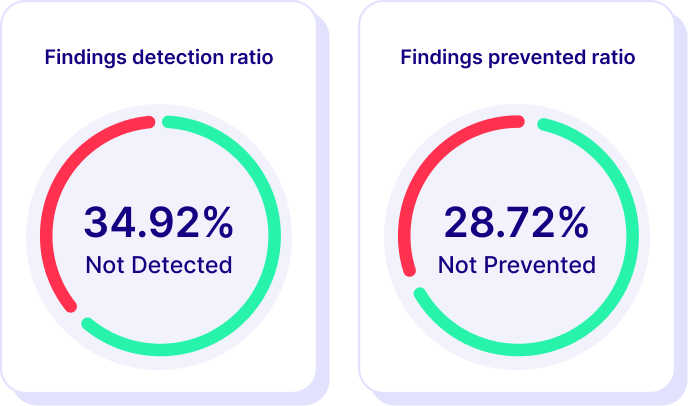
Trusted Results
Remove skepticism with evidence of exploitability and confidence to integrate automated testing in exposure management.
GET A PERSONALIZED DEMO
Ready to see Cymulate in action?
“With Cymulate, we can present quantifiable data to the board and show a direct correlation between investments and the reduction in risk.“
- Avinash Dharmadhikari, CISO, Persistent



