Red Team in Cybersecurity
In cybersecurity, organizations often assemble red, blue and purple teams to assess their security posture and resilience to cyber threats. The different colors symbolize the different responsibilities of each team:
- Red – offense
- Blue – defense
- Purple – a combination of offense and defense
The reasoning for the red and the blue team definitions originates from military exercises where training teams simulate enemy actions. In these exercises, the "red team" represents the attackers, while the "blue team" represents the defenders.
Key highlights:
- Red team in cybersecurity helps organizations proactively identify and remediate vulnerabilities, testing controls across a variety of adversarial techniques.
- Common red teaming methods include reconnaissance, social engineering, exploitation, lateral movement and exfiltration, each designed to assess different aspects of an organization’s security defenses.
- Despite their benefits, traditional red teams face challenges like limited resources, a continuously expanding threat landscape and difficulties in consistent validation, which can make it hard to fully assess and strengthen defenses.
- Automated red teaming with a tool like Cymulate offers a scalable, continuous testing approach, providing near-real-time insights into vulnerabilities and helping prioritize remediation by risk, making it a valuable enhancement to traditional red team efforts.
What is a red team in cybersecurity?
A red team in cybersecurity is a group of offensive security testers, such as penetration testers, vulnerability assessors and ethical hackers, who simulate cyber attacks. They aim to think like attackers and use tactics, techniques and procedures (TTPs) seen in the real world to breach an organization's defenses.
Red teaming tests are designed to challenge and verify an organization’s threat resilience and find weaknesses in its security posture before malicious threat actors (real-world hackers) can exploit them.
What does a red team do?
A cyber red team tests and evaluates an organization’s security defenses from an attacker’s perspective on an ongoing basis. Red team operations are more comprehensive and adversarial than routine security assessments, which often involve checking for compliance or performing standardized vulnerability scans. Their primary activities are:
- Identifying exploitable vulnerabilities: The primary goal of a red team is to uncover weaknesses in an organization’s security posture. By simulating real-world attacks, they identify vulnerabilities that malicious actors could exploit.
- Testing security measures: Testing security controls such as firewalls, intrusion detection systems, access controls and other security mechanisms to ensure they function as intended.
- Simulating real-world attacks: Adopt the tactics, techniques and procedures (TTPs) used by actual cyber criminals to help organizations understand if and how they would hold against real threats
- Improving incident response: Red teams provide valuable insights into the effectiveness of the organization’s incident response procedures, helping, for example, blue teams refine their response strategies
In the context of identifying IoCs, the Pyramid of Pain framework offers an effective approach to prioritization. The pyramid categorizes IoCs based on how difficult they are for attackers to modify, with hashes, IP addresses and domains at the base and TTPs at the peak. By focusing on TTPs, red teams can create significant operational challenges for adversaries, disrupting their campaigns more effectively. This strategic focus ensures that red team activities go beyond surface-level vulnerabilities and address deeper security gaps.
Why do I need a red team for cybersecurity?
Red teaming gives you a realistic view of how attackers see your environment and where your defenses fall short. Red teaming helps you:
- Identify real attack paths: See how an attacker would actually move through your environment by chaining together real vulnerabilities and misconfigurations.
- Validate security controls: Confirm which tools, alerts and processes hold up under real‑world attacker behavior and which ones break down.
- Strengthen incident response: Train your IR team to detect, contain and recover from a live adversary simulation under realistic pressure.
- Uncover blind spots: Identify hidden gaps across assets, access and configurations that routine assessments fail to surface.
- Test people and processes: Stress‑test workflows, communication chains and decision‑making to see where human factors create risk.
- Support security strategy: Prioritize investments and remediation with insights grounded in attacker impact, not assumptions.
Types of red team engagements
Red team exercises can take several forms depending on your goals, resources and risk tolerance. Choosing the right type ensures you focus on the areas that matter most.
- Full scope red team assessment: A full scope assessment simulates a real attacker targeting your entire environment and shows how an adversary could move from initial access to your most critical assets.
- Objective-based red team: An objective-based engagement focuses on a specific target or outcome, which allows you to test high-value risks without running a full organizational assessment.
- Threat-informed red teaming: A threat-informed engagement uses real attacker intelligence and mirrors the adversary tactics most likely to target your industry.
- Assumed breach engagement: An assumed breach assessment begins with the red team already inside the network, helping you measure how quickly your team can detect and contain post-compromise activity.
- Continuous automated red teaming: A continuous or automated engagement runs on an ongoing basis and gives you real-time insight into new gaps as your environment evolves.
Red team exercises: What they typically include
Red team operations follow a series of steps that mirror how real attackers break into an environment. Each phase targets a different part of your security posture and exposes weaknesses that traditional testing might miss. Below are the key stages you can expect in most red team engagements.
1. Reconnaissance
Red team attack begins by collecting information that helps them plan their attack, including the following:
- Open source intelligence (OSINT): Gathering information from publicly available sources (websites, social media, public records) to identify potential attack vectors and entry points.
- Network scanning: Using tools like Nmap or Nessus to identify open ports, services and network vulnerabilities.
- Social engineering recon: Collecting information about employees, organizational structure and internal processes that could be exploited in social engineering attacks.
2. Social engineering
Red teams then test how easily attackers can manipulate people inside the organization, using methods such as:
- Phishing: Crafting deceptive emails or messages to trick employees into revealing credentials, clicking malicious links or downloading malware.
- Pretexting: Creating a fabricated scenario to manipulate someone into disclosing sensitive information or performing an action.
- Baiting: Leaving physical devices (like USB drives) with malware in public or easily accessible areas to see if someone will plug them into their computer.
3. Exploitation
Once enough information is collected, red teams attempt to break in using techniques like:
- Vulnerability exploitation: Identifying and exploiting known or unknown software, application or system vulnerabilities to gain unauthorized access.
- Credential theft: Using methods like password spraying, brute-forcing or exploiting weak passwords to gain access to accounts and systems.
- Zero-day exploits: Utilizing unknown or unpatched vulnerabilities to compromise systems. Zero-day attacks are highly effective and challenging to defend against since the exploit is unknown to the vendor or the organization.
4. Lateral movement
After gaining access, red teams try to move deeper into the network, often using tactics such as:
- Pass-the-hash and pass-the-ticket attacks: These methods involve using stolen credentials or tokens to move laterally within the network. In a Pass-the-hash attack, the attacker captures a user's hashed password and reuses it to authenticate as that user without needing to know the actual password. Similarly, in a Pass-the-ticket attack, the attacker steals a Kerberos ticket to access resources within the network. Both techniques allow attackers to access additional systems and escalate their privileges without cracking the original password.
- Pivoting: After gaining initial access to a network, Red teams often use pivoting techniques to move from one compromised system to another, using the compromised system as a gateway to other parts of the network. This allows attackers to expand their foothold and access more sensitive areas of the network.
- Living off the Land (LotL): Living off the Land attacks involve using the existing tools and processes within a network to carry out an attack. Red teams may use built-in tools like PowerShell, Windows Management Instrumentation (WMI) or other legitimate software to conduct malicious activities.
5. Exfiltration
To complete the operation, red teams attempt to remove sensitive data without being detected, often using methods like:
- Data exfiltration: Encrypting stolen data to prevent detection during exfiltration. This makes the data look like normal encrypted traffic, making it harder for security teams to detect the breach.
- Steganography: Hiding data within other files, such as images or documents, to conceal the exfiltration process. This can help avoid detection by security monitoring tools.
- Using legitimate channels: Exfiltrating data through legitimate channels like email, cloud storage or DNS requests further complicates detection efforts.
Red teams vs. blue teams vs. purple teams
While the red team plays the role of the offender or attacker, the blue team defends against the attack from the red team. Purple teams bridge the two, facilitating collaboration and knowledge sharing so lessons from red team attacks directly improve blue team defenses.
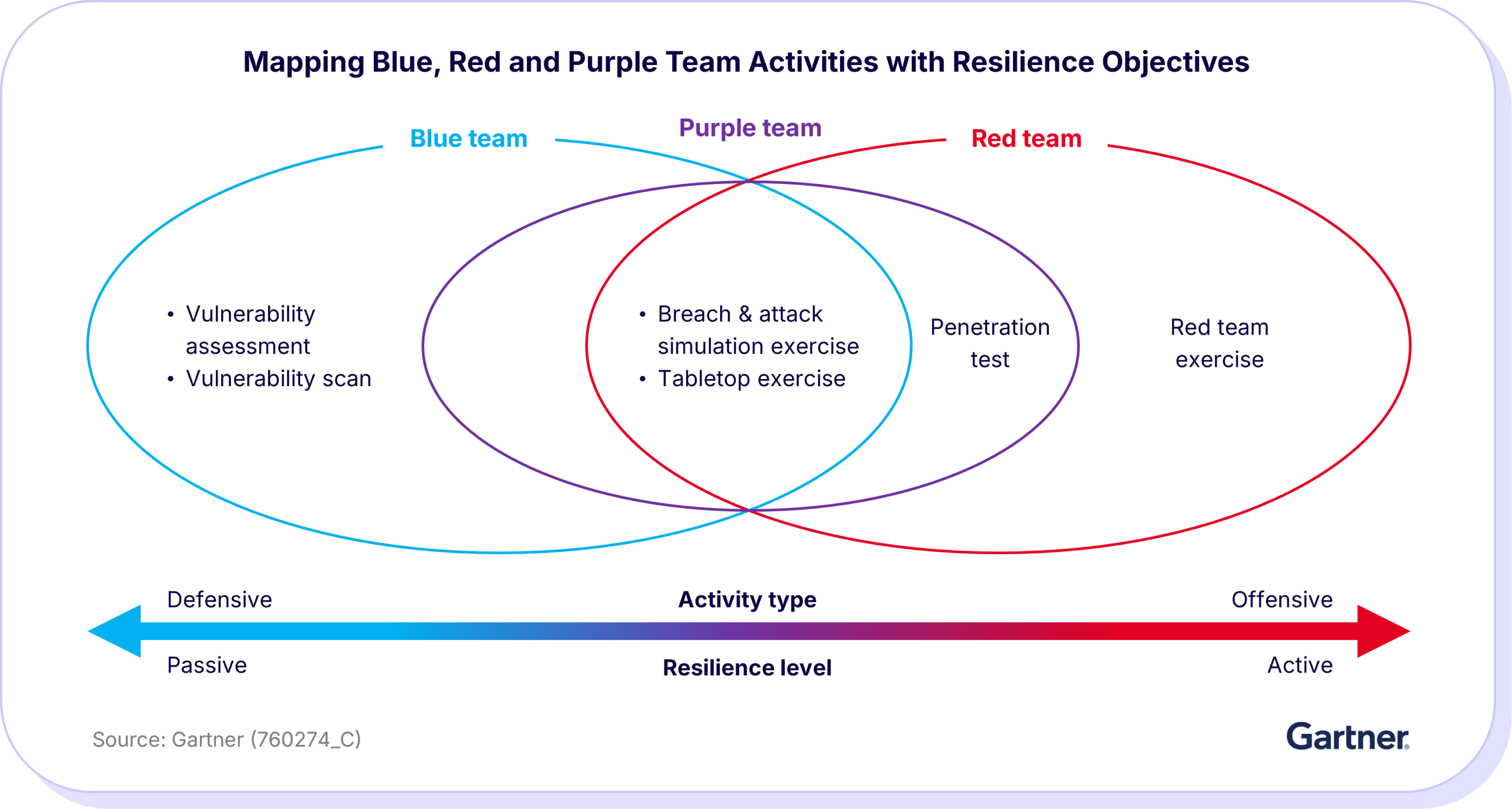
For example, a red team might simulate a cyber attack in which they attempt to breach security measures, exfiltrate sensitive data, or disrupt services. The blue team is then responsible for defending against these simulated attacks. They focus on detecting, responding to, and mitigating any attempted breaches. This involves monitoring network traffic, analyzing security logs, deploying patches, and refining defense strategies to prevent future incidents.
Challenges of traditional red teaming
While the tasks performed by a red team are essential to any cybersecurity posture assessment, they might not be enough to maintain a resilient cyber defense in the constantly evolving cyber threat landscape. Challenges facing red teams include:
- Lack of resources and limited capacity
- Continuously growing threat landscape
- Communication gaps with blue teams and other parts of the cyber defense company infrastructure
- Inability to extensively validate each security defense
Common red teaming tools
There is a wealth of pen testing and red teaming tools out there, both paid and open source, to help you test your infrastructure, including:
- MITRE Caldera is an automated adversary emulation tool designed to test defenses against the latest cyber threats. Caldera provides modular TTPs based on MITRE ATT&CK and can automate complex attack chains, making it a powerful addition for those who need to simulate realistic, multi-step attacks. However, users require technical expertise to fully leverage its potential and the tool provides limited guidance on addressing identified weaknesses.
- Red Canary Atomic Red Team is another popular option, providing a library of simple, atomic tests that emulate a range of known adversarial behaviors. Its straightforward framework allows security teams to test specific TTPs across different platforms with less setup, making it ideal for assessing individual components of a security posture. Yet, as with Caldera, it lacks comprehensive remediation guidance, requiring analysts to devise their own solutions for any detected vulnerabilities.
- The Metasploit framework remains one of the most widely used tools for penetration testing and red teaming. It offers extensive exploitation and post-exploitation capabilities. It is highly adaptable, with a vast repository of exploit modules that can be customized to suit various testing needs. However, Metasploit demands substantial technical knowledge and, like many red teaming tools, it does not prioritize vulnerabilities or offer specific remediation steps.
Red team tools often lack the latest cyber threat intelligence, which means they can only challenge controls against known threats. Alternatively, red team testers must conduct research in advance to incorporate the latest threat intelligence in their testing. New malware variants emerge daily, requiring you to ensure that your controls can identify the newest attacks’ Indicators of Compromise (IoCs), stealth techniques and behaviors.
Due to these variables, it is challenging for CISOs and IT teams to make meaningful evaluations of security control effectiveness across attack vectors for accurate security risk assessment. A lack of remediation guidance further complicates the prioritization of resources for mitigating identified weaknesses.
Without end-to-end automation, red teaming exercises are difficult to repeat consistently, hard to perform on a large scale and challenging to execute with a broad scope. For instance, after running an exercise and fine-tuning controls, you would want to repeat the same barrage of tests to ensure the adjusted controls work.
Shift to automated red teaming with Cymulate
Given red teams' challenges, many organizations looking to strengthen their security posture are turning to automated exposure management. Automation involves the continuous testing and validation of security controls to ensure they are functioning as intended and that they are effective against the latest emerging threats.
The Cymulate solution for the red team makes the process faster, easier and more reliable. It allows security teams to run continuous simulations of advanced threats, attack techniques and adversary behaviors without manual intervention. This automation provides near-real-time visibility into vulnerabilities and highlights any gaps in your defenses as your IT environment changes.
Unlike traditional red teaming, which may only happen periodically due to resource and time constraints, Cymulate ensures testing is ongoing, helping teams respond quickly to new risks and maintain strong, up-to-date security controls.
Frequently asked questions
The red team is responsible for trying to compromise an organization by using real attacker tactics, techniques and procedures. Their goal is to mimic how an adversary would operate, identify weaknesses and show how far an attacker could go inside the environment.
Red team vulnerability assessment is the process of going beyond traditional vulnerability scanning with attacker‑style testing to show what an attacker could actually do with those weaknesses. Red team vulnerability assessments:
- Find weaknesses: Scan systems, applications and networks for vulnerabilities.
- Test exploitability: Check if those weaknesses can actually be used to gain access or move through the network.
- Discover attack paths: Show how an attacker could chain multiple vulnerabilities to reach important assets.
- Check defenses: See if current security controls detect or stop these attacks.
The primary goals of a red team are to mimic real attackers, uncover security weaknesses and test how well defenses hold up under pressure. A red team also demonstrates how far an adversary could move inside your environment and provides actionable insights to improve security. Common objectives include:
- Identify weaknesses: Expose vulnerabilities across people, processes and technology.
- Test defenses: Evaluate the effectiveness of detection, prevention and response controls.
- Simulate attackers: Recreate realistic adversary behaviors and attack paths.
- Measure impact: Show what an attacker could achieve if exploitation succeeds.
- Improve resilience: Provide insights that help security teams strengthen their overall security posture.
Most red team exercises take several weeks to a few months, depending on scope, complexity and the organization’s size. Larger or more mature environments often require longer engagements.
Penetration testing checks for vulnerabilities in specific systems or applications, while red teaming simulates a real attacker trying to achieve broader objectives across people, processes and technology. Use the following table to understand the difference between red teaming and penetration testing:
| Feature | Penetration testing | Red teaming |
| Scope | Specific systems or applications | The entire organization and attack lifecycle |
| Goal | Identify exploitable vulnerabilities | Test if attackers can achieve strategic objectives |
| Approach | Controlled and scoped | Goal-driven and realistic |
| Outcome | List of vulnerabilities and remediation steps | Insights into attack paths, detection gaps and response effectiveness |
Red, blue and purple teams work best when their efforts are coordinated and continuous. Here’s how the three teams can work together.
- The red team identifies vulnerabilities, attack paths and techniques that real adversaries could exploit.
- The blue team monitors and investigates attacks while improving detection, containment and mitigation strategies.
- The purple team bridges red and blue teams by analyzing outcomes, highlighting gaps and ensuring lessons are applied across the organization.
Each exercise feeds into the next, using red team insights, blue team responses and purple team oversight to strengthen defenses over time.
Success in red teaming is measured by the quality of insights gained and the improvements made to your defenses, not by whether the red team “wins.” Key indicators of success include:
- Objective completion rate: The red team successfully reaches the predefined goals of the engagement, such as accessing a target system or demonstrating data exposure.
- Stealth level: The red team carries out actions without being detected early in the engagement, showing the accuracy and realism of the simulation.
- Attack path clarity: The red team maps clear, reproducible paths that an attacker could use, making the findings actionable.
- Quality of findings: The red team delivers findings that are meaningful, specific and directly tied to real attack scenarios rather than generic issues.
- Actionability of recommendations: The red team provides remediation steps that are practical and can be implemented by the blue team.