Cyber Kill Chain
The Cyber Kill Chain shows the step-by-step execution of a cyberattack, from initiation to data exfiltration. This framework is invaluable for analyzing and mitigating threats, including ransomware, data breaches, and advanced persistent threats (APTs).
Originally developed by Lockheed Martin, the Cyber Kill Chain helps identify, engage, and neutralize targets effectively. Over time, it has evolved to address emerging threats such as social engineering, insider risks, and sophisticated ransomware attacks. By thwarting an attacker at any stage, defenders can prevent significant damage and gather valuable insights to strengthen their defenses.
What is the Cyber Kill Chain?
The Cyber Kill Chain framework provides a structured approach for blue teams to analyze incidents and communicate effectively among security professionals. It outlines the phases an attacker follows during a cyberattack, offering a systematic way to identify and mitigate advanced threats.
It can be used to distinguish between minor incidents and critical crises. Its adaptability to evolving threats, such as those stemming from cloud computing and IoT technologies, underscores its relevance in modern cybersecurity. That flexibility underlines the model's resilience and applicability. Although attack methods have continued to evolve and diversify, the Cyber Kill Chain remains relevant for analyzing the different stages of a cyberattack and developing robust defense mechanisms against evolving threats.
The Origins: Lockheed Martin's Cyber Kill Chain
Developed in 2011 by Lockheed Martin, the Cyber Kill Chain is part of an intelligence-based defense strategy designed to help security teams understand and disrupt the phases of cyber intrusions. Borrowing terminology from military strategy, the "kill chain" describes the sequence of events leading to the engagement and neutralization of a target.By breaking down an attack into stages, defenders can plan targeted tactics to detect, disrupt, and defend against threats
The framework has been continuously modified to cope with the increasing complexity and variety of current threats. Over time, the model has been adjusted to account for the advanced tactics, techniques, and procedures (TTPs) employed in contemporary cyberattacks, which often surpass the scenarios initially envisioned.
A significant evolution is the addition of more stages or redefinition of stages to reflect current threat landscapes. For example, the payload of the latest adaptation includes phases addressing the attacker's persistence in a network, lateral movement (to other machines), and privilege escalation to reach a vital resource target.
These enhancements also generalize the framework to the post-exploitation phase, including data exfiltration or malicious sabotage of critical infrastructure, thereby providing a solution to the whole lifecycle of current cyberattacks.
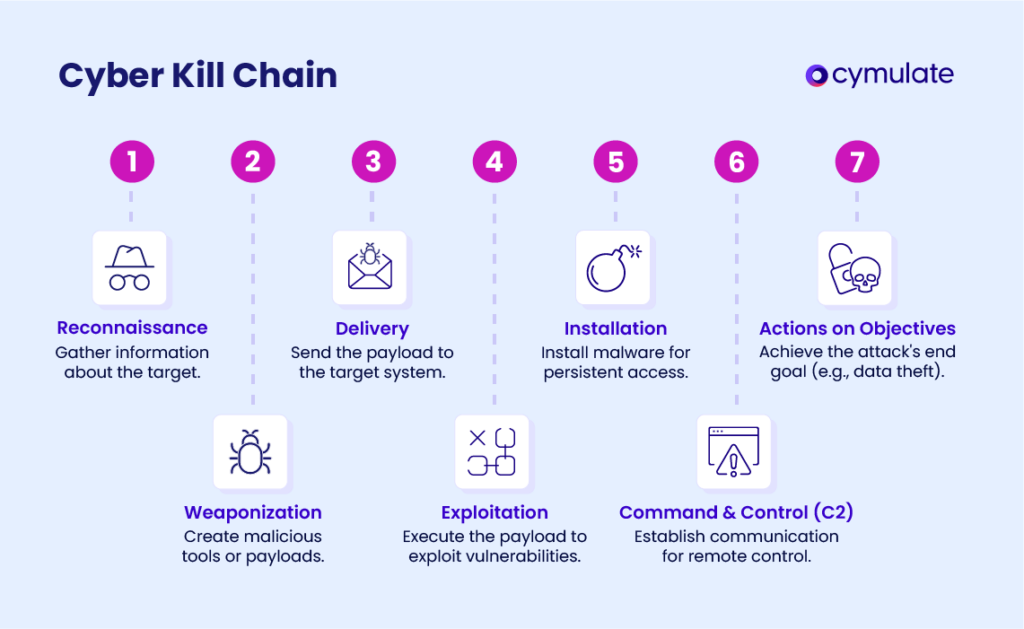
The 7 Steps of the Cyber Kill Chain
- Reconnaissance: Attackers prepare for the target by trying to find out about the systems, the users and what manner of vulnerabilities they may have. For instance, they may scan the Internet for public Internet IP ranges with open ports or browse social media to look for clues on employee roles within the organization. Defensive action includes adversary emulation testing to determine the effectiveness of security tools in identifying and mitigating adversarial scanning activities, and anomaly monitoring and detection of suspicious access patterns.
- Weaponization: Attackers develop malicious tools or payloads to target known vulnerabilities. For example, they could create an email phishing attack that contains a Word document that executes a macro exploit. Establishing sandbox environments to test and quarantine weaponized files can stop an attack before attackers can completely compromise the system.
- Delivery: Attackers deliver the payload via a vector to the target using means such as electronic mail, USB, and compromised websites. Relevant examples include sending an email with a website link that contains malware. Consequently, the organization may want to validate its web security tools against the threat by performing extensive penetration tests.
- Exploitation: Attackers use the payload to exploit a vulnerability that leads to gaining initial access. They could also use it to exploit an unpatched server vulnerability for remote code execution. This risk can be reduced by closely validating an organization's patch management process and ensuring that vulnerability scanners find issues that could be exploited.
- Installation: Attackers install malware or backdoors to maintain their position inside the system. For instance, they may drop a keylogger or a remote access Trojan onto the target machine. Proactive measures, such as using endpoint detection tools while carrying out simulated attacks, support early detection and blocking of such malicious installations.
- Command and Control (C2): The attacker creates connections with victim machines to execute commands or export information. For instance, malware can call back to an attacker's server to receive command directives. Defenders can simulate this traffic to test network defenses' ability to detect and block unauthorized communications.
- Actions on Objectives: This is where attackers fulfill their final goals, such as stealing data, destroying it, or conducting espionage. The attackers might export customer data or encrypt all the systems in anticipation of a ransom demand. Good monitoring systems, tuned to detect anomalies in data transmission or file access, help with early responses that limit the impact.
Cyber Kill Chain vs. MITRE ATT&CK
The Cyber Kill Chain and MITRE ATT&CK frameworks share one common goal: to analyze adversary behavior and tactics for the enhancement of cyber defense. Both provide real-world insights to help an organization enhance its capability for threat detection, prevention, and response. However, they have some significant differences in terms of their focus and application.
- The Cyber Kill Chain shows very clearly the life cycle of an attack in terms of consecutive stages: reconnaissance, delivery, and exploitation.
- On the other hand, the MITRE ATT&CK framework is far more developed and connects the dots among concrete tactics and techniques employed by adversaries in real-life attacks, especially APTs.
An organization can choose any of these two frameworks depending on their needs or it may decide to use them together for better results. Where the Cyber Kill Chain is best applied in explaining the end-to-end flow of an attack and in strategically organizing security programs, MITRE ATT&CK serves well for operational activities such as threat hunting, adversary emulation, and refinement of detection capabilities. More importantly, together, they let organizations knit both strategic plans and tactical execution to stand fully prepared against the evolving threat landscape.
The Role of Adversary Emulation
Adversary emulation is the key factor at all levels of validating security controls in the Cyber Kill Chain. It replicates the TTPs utilized in real life by the attackers, which allows an organization to test its defenses in a controlled, secure manner. It is helpful in finding weaknesses in detection, prevention, and response capabilities at every phase, starting from the beginning with reconnaissance up to the execution of objectives. Penetration testing provides insight to inform proactive steps that security teams must take to bolster the defense posture and set the configurations of their security tools to address emerging threats better.
The Cymulate Full Kill Chain Scenario
The Cymulate Full Kill Chain Scenarios module provides a comprehensive solution for measuring and improving your organization's defense against real-world APTs by testing the effectiveness of your various security controls across the entire cyber kill chain - from attack delivery to exploitation to post-exploitation. Instead of challenging each attack vector separately, you can run a Full Kill Chain Scenarios assessment to simulate a fullscale APT attack to test the effectiveness of your current detection tools, identify vulnerabilities, and help you take action to remediate any gaps.
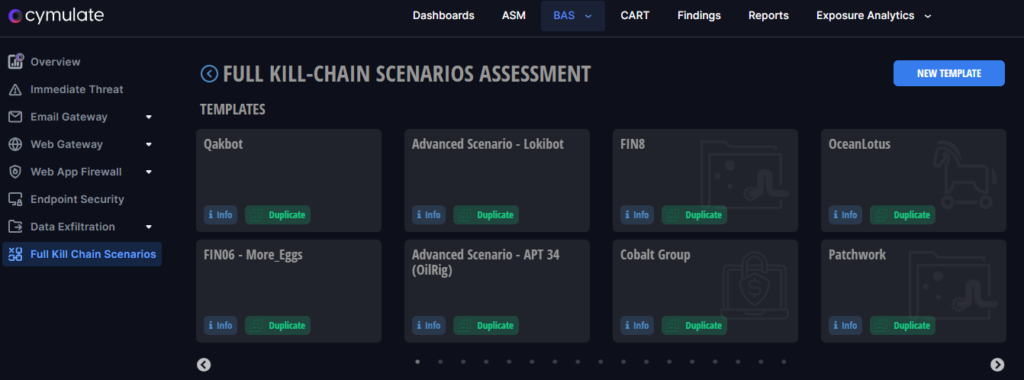
How the Full Kill Chain Scenario Assessment Works
Cymulate Full Kill Chain Scenarios are designed to simulate an end-to-end cyber-attack, replicating the sophisticated strategies employed by Advanced Persistent Threat (APT) groups. This comprehensive simulation allows organizations to test their defenses against a variety of attack vectors and techniques that adversaries might use.
Beginning with the delivery of the initial payload, the simulation encompasses various stages, culminating in the execution of the attack.
- Phase 1: Initial foothold - In this initial phase, the assessment emulates a real Advanced Persistent Threat (APT). It begins with an attempt at infiltration and gaining initial foothold, by deploying a deceptive payload via a malicious attachment or link, or by simulating a direct malware download.
- Phase 2: Execution - Following the successful delivery of the payload in Phase 1, this phase intensifies the assessment. Here, the focus is on challenging the organization's endpoint security. Utilizing production-safe code execution coupled with advanced defense evasion techniques, the system is tested against various threats such as ransomware, trojans, worms, and other sophisticated attack scenarios. This phase evaluates the resilience of the endpoint security and identifies potential security gaps.
- Phase 3: Remediation and Guidance - Upon completion of the assessment, the system generates a comprehensive analysis of the findings. This phase is crucial as it provides prescriptive remediation guidance. It highlights the security gaps discovered during the assessment and offers strategic recommendations for mitigation. This guidance is tailored to enhance the organization's security posture and prepare it for real-world cyber threats.
By replicating sophisticated attack strategies, Cymulate enables organizations to identify vulnerabilities, improve detection capabilities, and enhance overall security posture.
Enhancing Cybersecurity with the Kill Chain Framework
The Cyber Kill Chain is an important framework for understanding and mitigating cyberattacks. By leveraging adversary emulation, integrating platforms like Cymulate, and combining complementary frameworks such as MITRE ATT&CK, organizations can build robust, adaptive defenses against the constantly evolving cyber threat landscape.