Attack Path Management Platform
Halt lateral movement and remediate misconfigurations with attack path management.
Why you need to manage attack paths
An attacker can reach critical business assets through lateral movement and privilege escalation. Automating offensive testing can prove the threats.
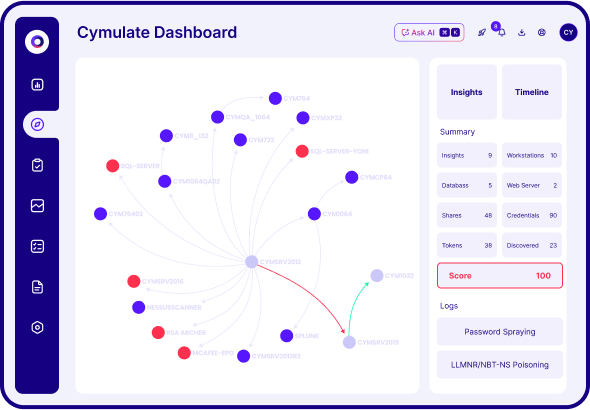
Map attack paths
Generate attack path maps automatically, from initial agent to every asset reached.
Test privilege escalation
Validate how effective security policies are limiting and/or preventing privilege escalation.
Target crown jewels
Assess how attackers can exploit exposures to reach critical data.
How proactive attack path management keeps you resilient
Cymulate automates offensive testing to identify threat exposures related to privilege escalation and lateral movement exposures. Through Attack Path Discovery, Cymulate maps potential adversary advancement paths, validates network segmentation and access control policies and delivers actionable mitigation guidance to improve threat resilience.
The reviews are in. Cymulate remains a leader in Breach and Attack Simulation
"Validating the effectiveness of our security tools is easy and effective with Cymulate BAS."

Test like an attacker.
Schedule a call with one of our experts.
Attack path validation and simulation across your entire environment
The Cymulate Exposure Validation Platform, with Attack Path Discovery, uses simulation tools to validate security controls and harden defenses with real-world testing. Identify control weaknesses and get policy tuning guidance, automated control updates and custom mitigation rules that can be directly applied to your security controls.
Trusted by enterprise security teams
Organizations across all industries choose Cymulate for exposure validation, proactively confirming that defenses are robust and reliable-before an attack occurs.
Frequently asked questions
An attack path is a series of connected vulnerabilities or misconfigurations that an attacker can exploit to move from an initial point of access through a network, systems or identity graph to reach a critical or high-value asset. The path represents not just where attackers might get in, but how they move once inside. It also describes which chain of exposures leads them to sensitive or critical resources.
Here’s a concrete (but realistic) example:
- Entry point: An attacker obtains access through an exposed web application with an unpatched vulnerability.
- Credential compromise: Using that web app, the attacker can extract credentials or gain access on a server.
- Privilege escalation: The compromise server has a service account with excessive permissions or misconfigured role membership. The attacker is able to escalate privileges.
- Later movement: From that server, the attacker uses permissions to access file shares or other internal servers.
- Target access: Eventually the attacker reaches a domain controller, sensitive databases or systems containing intellectual property.
An attack path is the specific route or chain of vulnerabilities/misconfigurations an attacker could follow after entry (or via some entry) to move inside an environment and reach a critical asset. It’s the “how” once inside, tracing through connected weaknesses.
An attack surface covers all possible entry points an attacker could exploit or get into, or affect, a system. This includes everything exposed, vulnerable or misconfigured. It’s the “what” of exposure.
An attack vector is the specific technique or method used to gain initial access or exploit a vulnerability. It’s the doorway into a system. Examples include phishing, exploiting unpatched software, brute-force, cross-site scripting and more.
An attack path is the sequence of vectors, configuration issues, identities and system relationships that an attacker uses (or could use) after initial access (and including the initial vector) to move toward a goal. It’s broader, describing the journey rather than one move.
Attack path management (APM) is the continuous practice that builds on discovery, analysis and remediation of attack paths. The core idea:
- Continuously discovering and mapping all possible or likely attack paths in your environment (on-premises, cloud, identity, etc.)
- Validating which ones are exploitable in real-world conditions
- Prioritizing them by risk (considering criticality of target, blast radius, ease of exploitability)
- Systematically eliminating, reducing or mitigating the high-risk paths in order to minimize exposure
It’s not simply a one-time assessment, but an ongoing capability to adapt as the organization evolves (new systems, new identities, new exposures) so that the paths an attacker might use are always monitored, understood and controlled.
Attack path management works by continuously mapping relationships between assets, identities and permissions to uncover exploitable routes to critical systems. It validates which paths are practical for attackers, prioritizes them by risk and business impact and identifies choke points where remediation has the biggest effect.
Finally, it guides remediation such as reducing privileges, patching vulnerabilities or segmenting networks. It also monitors for new paths as your environment changes.
Attack path management helps organizations focus remediation on the risks that are most critical rather than patching for the sake of patching. The process reduces the blast radius of potential breaches, strengthens identity and privilege hygiene and makes security operations more efficient. By proactively controlling attack paths, organizations gain stronger resilience, faster detection and better compliance readiness.
The three core steps are:
- Discovery and mapping of all attack paths
- Analysis and prioritization to identify the riskiest routes
- Remediation with continuous monitoring to eliminate or mitigate paths while adapting to environmental changes.
This cycle ensures organizations stay ahead of evolving exposures.
Yes. Active Directory is often central to attack path management because many paths rely on misconfigurations, excessive privileges or delegation with AD. By monitoring and hardening AD, organizations can eliminate high-risk choke points that attackers commonly exploit to gain domain dominance.
An attack surface management (ASM) platform discovers, monitors and helps reduce all external and internal exposures that attackers could exploit. It provides a complete view of assets, vulnerabilities and misconfigurations, ensuring that organizations understand where their environment is most at risk.
Key features include continuous asset discovery, vulnerability and misconfiguration detection and real-time monitoring of new exposures. ASM platforms also provide risk scoring, remediation guidance, integration with security workflows and dashboards for visibility. These capabilities help organizations shrink their attack surface and keep exposure under control.
GET A PERSONALIZED DEMO
Get your attack path management strategy on the track, see Cymulate in action now.
“Through validation, Cymulate helps us understand which vulnerabilities can be exploited in our organization. This helps us focus our limited resources so we can be proactive and remediate before a threat becomes an actual problem.”
– CISO, Law Enforcement