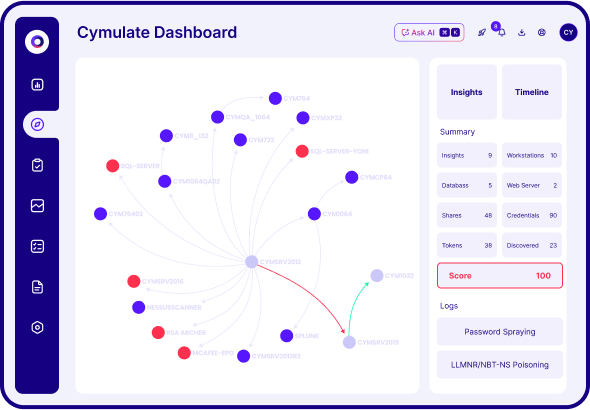
Is Automated Penetration Testing Software All You Need?
Go beyond an automated penetration testing platform with Exposure Management from Cymulate.
Do more than automated pen testing solutions.
While an automated pen test identifies threat exposures for vulnerabilities, it doesn’t provide control integrations to understand prevention and detection.
Point-in-time vulnerability discovery
Solve with continuous, threat-led validation testing from Cymulate that covers your entire security posture.
Control effectiveness not tested
Validate prevention and detection through easy, out-of-the-box control integrations with Cymulate Exposure Validation.
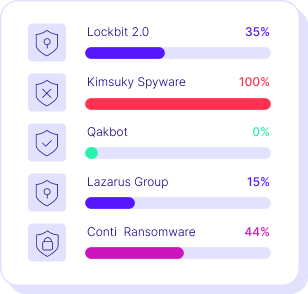
Manual, infrequent testing fails
Go beyond a penetration testing solution with Cymulate; automated mitigation pushes threat updates directly to security controls.
Better than a penetration testing platform
Cymulate Exposure Validation goes beyond a penetration testing platform, automating and scaling red teaming with threat-informed security assessments, allowing you to fast-track your red teaming exercises to identify the most critical security gaps and deliver actionable results.
Scale with automation
Accelerate with AI
Collaborate with purple teaming
Test with confidence
The reviews are in. Cymulate remains a leader in Breach and Attack Simulation
"Cymulate is not just another testing tool; it’s a strategic enabler for continuous security assurance. If you want to move beyond compliance and measure resilience, Cymulate is one of the best investments you can make."

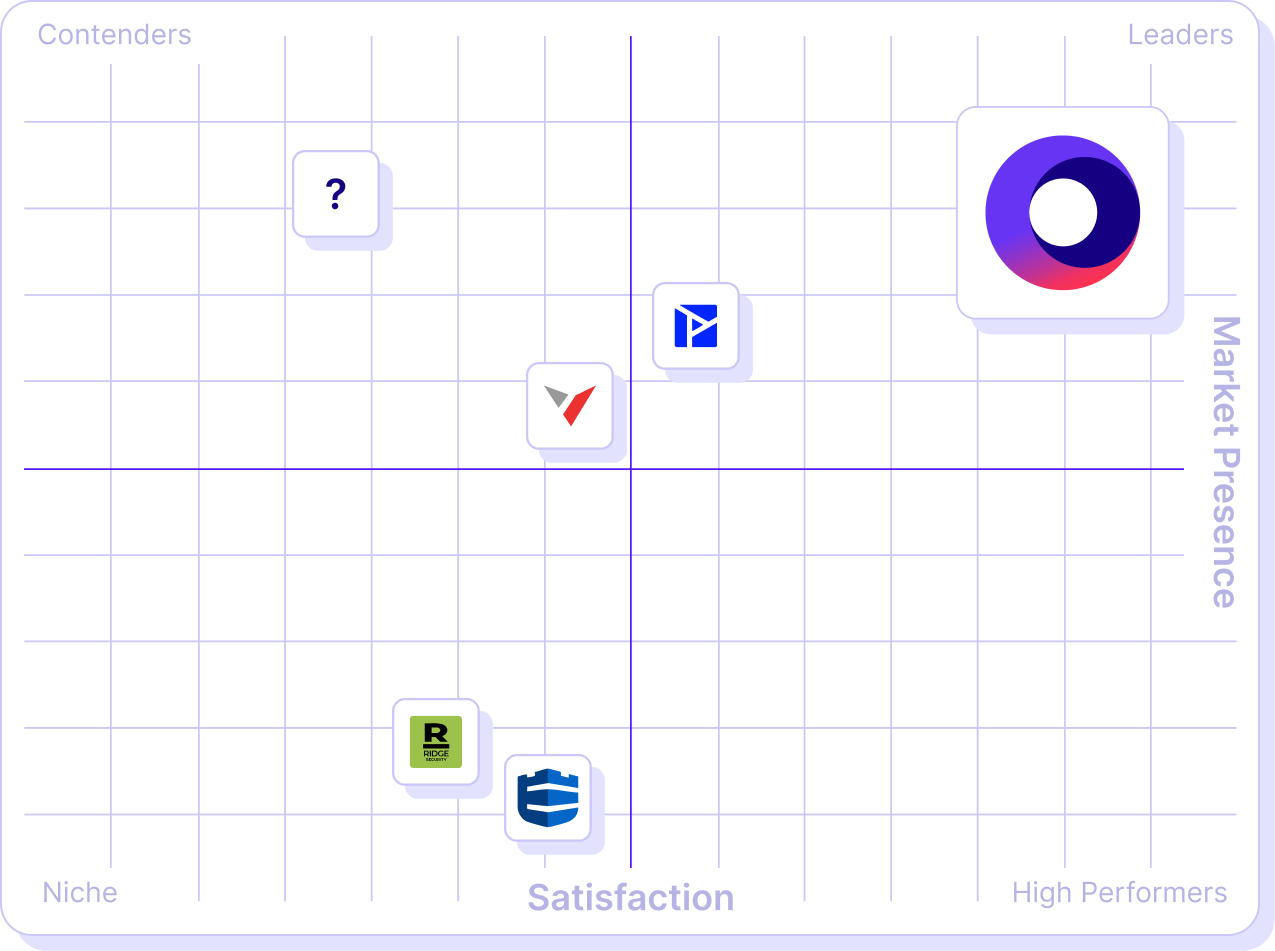
Test like an attacker.
Schedule a call with one of our experts.
Exposure validation beyond pen testing, at scale
Go beyond pen testing with continuous automated red teaming (CART). Get industry-leading breach and attack simulation (BAS), attack path discovery and custom attacks. Leverage AI-driven automation and the latest threat intelligence to automate production-safe, live-date adversary TTPs at scale.
What our customers say about us
Organizations go beyond automated penetration testing with Cymulate for exposure validation, proactively confirming defenses are robust and reliable before an attack.
Frequently asked questions
Manual penetration testing provides infrequent, time-consuming and resource-intensive testing that produces long lists of findings that are quickly outdated against the daily evolution of threats.
Automated penetration testing identifies threat exposures for vulnerabilities but does so without control integrations to understand prevention, detection and immediate action for improvement.
A vulnerability assessment (VA) scans for known weaknesses and misconfigurations, while penetration testing (PT) simulates real-world attacks to actively exploit those weaknesses. VA shows what could be vulnerable, whereas PT shows how an attacker would actually exploit them.
Look for a solution that supports automated, continuous testing, realistic attack simulations, detailed remediation guidance and integration with your security stack. Scalability, accuracy and minimal false positives are also critical.
Cymulate goes beyond a penetration testing platform. Cymulate Exposure Validation provides automated continuous testing, with offensive testing including a growing library of over 100,000 attack actions aligned to the full kill chain, MITRE ATT@CK and daily threat intel. It also offers easy, OOTB control integrations to validate prevention and detection as well as automated mitigation to push threat updates directly to security controls.
Organizations see a more than 50% improvement in their detection rates using Cymulate Exposure Validation.
Cymulate does more than just list CVEs. Our Exposure Validation Platform runs attacker-like simulations across your environment to discover exposures and prove whether they are actually exploitable. It finds and validates issues across numerous categories including:
- Known software vulnerabilities / CVEs
- Misconfigurations
- Network/perimeter weaknesses
- Endpoint and EDR gaps
- Email security weaknesses
- Identity and access weaknesses
- Web application and API exposures
- Cloud security exposures
- Attack path/exposure chains
Continuous threat validation shows which vulnerabilities are actually exploitable in your environment and how controls behave under an attack, then prioritizes remediation based on proven risk rather than CVE severity alone.
Yes. Automated pen tests are designed to safely simulate attacks without disrupting production systems. Unlike manual testing, they use controlled methods and configurable scopes to minimize operational risk.
Automated penetration tests should be run continuously or at least after every major update, configuration change or new deployment. Frequent testing ensures real-time visibility into evolving attack surfaces.
GET A PERSONALIZED DEMO
Go beyond automated penetration tests
Find out how Cymulate drives exposure validation beyond automated pen testing.