What Is an Attack Model in Cybersecurity?
An attack model is a structured representation of how a cyber adversary could carry out an attack against a target system or network.
It maps out the steps, tactics and techniques an attacker might use, from initial reconnaissance to achieving their end goals, providing defenders with a blueprint of potential attack paths and methods.
An attack model in cybersecurity lets organizations anticipate attacks by visualizing an attacker’s behavior and pathways, so they can strengthen defenses proactively.
- Attack model in cybersecurity: A framework mapping out how attackers exploit vulnerabilities, helping security teams understand and simulate potential breaches to improve preparedness.
- Structured cyber attack frameworks: Models like the Cyber kill chain and MITRE ATT&CK break attacks into phases or Tactics, Techniques and Procedures (TTPs), providing clear steps to detect and stop adversaries at each stage.
- Purpose-driven defense: Building an attack model clarifies an attacker’s motives, goals and objectives, aligning security controls to the most common cyber attacks likely to target the organization.
- Cymulate advantage: The Cymulate Exposure Management Platform enables Continuous Security Validation through automated attack simulations, operationalizing attack models to pinpoint security gaps and improve your security posture on an ongoing basis.
Purpose of an attack model
The primary purpose of an attack model is to understand the “why” and “how” behind potential attacks in order to bolster defenses. It forces defenders to think like attackers, clarifying the attacker’s motives, goals and objectives (often called the motives-goals-objectives formula).
In other words, an attack model captures why an attacker might target you (motive), what they want to achieve (goal) and how they might execute the attack (objectives and methods). Security teams can perform thorough risk assessments, ensure compliance with security frameworks and prioritize defenses around their “crown jewels.”
Attack modeling is about being proactive: it identifies likely threat scenarios before they occur, so organizations can fix vulnerabilities and refine controls in advance.
What are the benefits of modeling cyberattacks?
This rising digital risk, coupled with stricter regulations on breach reporting and security controls, means organizations must take steps.
Attack models provide a blueprint of possible attack paths, allowing teams to rehearse and prepare for incidents before they happen.
Consider a few key benefits of cyberattack modeling (supported by industry observations and best practices):
- Realistic defense testing: By simulating the most common cyber attacks and advanced tactics, organizations can safely uncover security gaps.
- Better resource allocation: Attack modeling focuses attention on high-impact threats. By mapping likely attack paths, security teams can prioritize fortifying the weakest links and high-value assets first.
- Faster breach response: Practicing attack scenarios improves incident response. Teams that have walked through model-based scenarios (e.g. a ransomware attack model) can detect and respond faster in reality.
- Audit and compliance support: An attack model serves as evidence that you are testing controls against known threat scenarios. This can demonstrate compliance with frameworks and regulations, you can show auditors that you’ve modeled, say, a data theft scenario and validated that your DLP and logging controls would catch it.
- Informed security design: Modeling attacks yields insights that feed back into security architecture. For example, if an attack model shows an attacker could exploit a certain vulnerability or misconfiguration to reach critical data, that informs architects to redesign that system or add specific controls.
Companies can significantly reduce their risk by proactively simulating attacks with attack models.
Components of an attack model
When creating an attack model, it’s important to include several core components that collectively capture the threat scenario. Key components typically include:
- Adversary profile: Who is the attacker? Define the threat actor’s type (e.g. cybercriminal, nation-state APT, insider), their resources, skills and intent. A well-rounded profile answers “who is attacking and why,” whether it’s a financially motivated ransomware gang or a hacktivist group.
- Objectives: What does the attacker want to achieve? Clearly state the goals, for example, data theft, financial fraud, service disruption, espionage or sabotage. Objectives should align with the adversary’s motive (stealing intellectual property, causing reputational damage, etc.).
- Capabilities and tools: Outline the tools, malware, or exploits the adversary is capable of using. An APT might wield zero-day exploits and sophisticated malware, while a script-kiddie might rely on off-the-shelf phishing kits. This helps gauge the technical methods likely to be seen.
- Attack surface and entry points: Document the potential entry routes into the system, all possible attack vectors the adversary could exploit. This could include phishing emails, exposed RDP ports, vulnerable web applications, supply chain partners or even an insider planting a USB. Essentially, map out the attack surface and enumerate where the attacker could first breach (the initial foothold).
- Techniques and tactics: Detail the tactics, techniques, and procedures (TTPs) the attacker might use at each stage. This often means mapping actions to frameworks like MITRE ATT&CK.
- Constraints and assumptions: Finally, note any assumptions or scope limits in the model. For instance, you might assume the attacker starts with zero insider knowledge, or conversely assume they already have stolen credentials. Also list environmental constraints (e.g. “DMZ network is segregated”) that could affect the attack’s path. These assumptions make it clear what conditions the model is built around.
The attack model transforms into a detailed and realistic scenario with these elements, specifically adapted to your environment. It effectively addresses: potential attackers, their motives, methods, tools and your most vulnerable areas.
Types of attack models and frameworks
The cybersecurity community has developed several attack modeling frameworks to systematically describe and analyze cyberattacks. These frameworks range from classical models to modern, granular approaches.
Below, we segment a few of the most common cyberattack models and frameworks, and compare their core focus:
| Cyber Attack Model Type | Core Focus | Example Techniques/Features |
| Cyber Kill Chain | Linear stages of an attack from reconnaissance to actions on objectives. Emphasizes stopping attacks early in the chain. | Phases: Reconnaissance, Weaponization, Delivery, Exploitation, Installation, Command and Control, Actions on Objectives. Example: Phishing email (Delivery) -> malware install (Installation) -> data exfiltration (Actions). |
| MITRE ATT&CK | Matrix of adversary tactics & techniques covering the entire lifecycle (not strictly linear). Focuses on cataloguing TTPs in detail. | Techniques mapped to tactics like Initial Access, Privilege Escalation, Lateral Movement, Exfiltration, Impact, etc. Example: Technique T1566 Phishing, T1059 Command-Line Execution, etc., which can occur in various orders. |
| Attack Trees | Hierarchical model of attack goals and sub-goals. Visualizes how an attacker can achieve a goal via multiple paths (branches). | Root node = attacker’s main goal; branches = different attack paths or steps. Example: Goal “Gain Unauthorized Access” -> Path 1: Brute-force password, Path 2: Exploit SQL injection, Path 3: Social engineering. Each branch can further split into sub-techniques. |
| Attack Graphs | Node-link diagram of all possible attack paths in a network, often generated algorithmically. Shows how multiple conditions/vulnerabilities can chain together. | Nodes represent system states or vulnerabilities; edges represent exploits transitioning the state. Often used to chart attack path analysis in complex IT environments, highlighting chained exploits Example: Weak credential -> unsecured share -> privilege escalation -> critical server access). |
Each framework has its strengths. The cyber kill chain is great for high-level understanding of the stages of an intrusion (and is often used for training and organizing defenses by phase).
MITRE ATT&CK is very detailed and useful for threat intelligence and technical defensive gap analysis (you can map your detections to specific techniques).
Attack trees and attack graphs are more flexible modeling techniques often used in threat modeling and academic contexts, they excel at visualizing complex or non-linear attack paths (trees focus on logical breakdown of goals, while graphs focus on network state transitions).
These frameworks can complement each other. You might use the cyber kill chain to ensure you have security controls at each stage, use MITRE ATT&CK to verify coverage of specific techniques, and employ attack graphs to perform attack path analysis on your network for weaknesses.
How do attack models work in practice?
An attack model looks like a scripted scenario or roadmap of an attack, which security teams can use for simulation and analysis.
Think of it as a play-by-play of how an adversary would move through your systems. For example, a simple attack model scenario might be:
- Initial compromise: An adversary sends a convincing phishing email to an employee, who clicks a malicious link. The attacker thus gains initial access to the corporate network (mapping to a phishing technique in MITRE ATT&CK for Initial Access).
- Establish foothold: The attacker executes malware that installs a backdoor on the employee’s machine (this corresponds to techniques in Execution and Persistence tactics). Now they have a persistent presence.
- Privilege escalation: The malware exploits a local vulnerability to gain administrator rights on that machine (an Privilege Escalation technique). The attacker can now access sensitive data on the compromised host and use its credentials.
- Lateral movement: Using the stolen credentials or malware, the attacker moves laterally to another server on the network such as, accessing a file server or database (a Lateral Movement tactic, e.g. using pass-the-hash or remote service execution).
- Data collection: Once on a critical server, the attacker locates valuable data (databases, file shares) and aggregates it (this involves Discovery tactics to find data and collection techniques to gather it).
- Exfiltration: The attacker then exfiltrates the data out of the network, perhaps by uploading it to a remote server or cloud drive (Exfiltration tactic).
- Impact: Finally, as an example of an impact action, the attacker might deploy ransomware or destroy logs to cover tracks (Impact tactic, e.g. data encryption or destruction).
Each step in this scenario can be directly mapped to defined tactics and techniques (for instance, MITRE ATT&CK technique T1566 for phishing, T1055 for process injection in escalation, T1021 for lateral movement via remote services, etc.).
7-step process of attack modeling in cybersecurity
Building and using an attack model can be formalized into a repeatable process. Here’s a typical seven-step process cybersecurity teams follow for attack modeling:
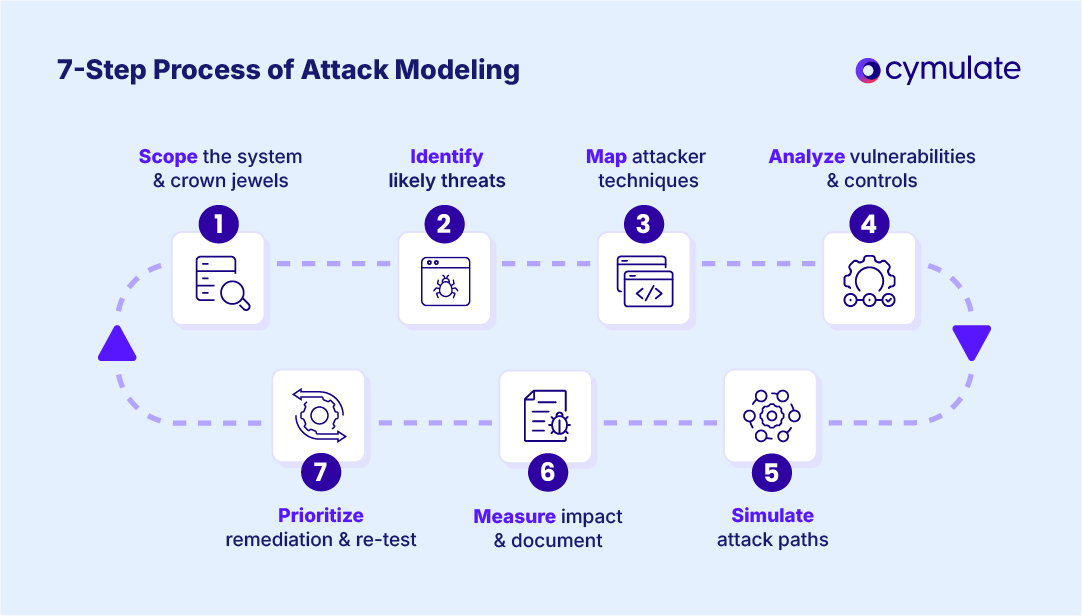
1: Scope the system and crown jewels
Define the boundaries of the system or application you’re modeling (infrastructure, apps, data flows) and identify your “crown jewels,” the critical assets most likely to be targeted. This sets the focus for the modeling exercise.
2: Identify likely threats and objectives
Determine the threat actors and their motives that are relevant to your organization. Are you worried about cybercriminals seeking financial gain? Nation-state espionage? Insider threats?
For each, clarify what their objectives would be (e.g. steal customer data, sabotage operations). This ensures the model addresses realistic threats.
3: Map attacker techniques to your environment
For the chosen threats, brainstorm or research the attack techniques they have used or could use, especially in contexts similar to yours.
Leverage threat intel and frameworks, e.g., map out which MITRE ATT&CK techniques an attacker might employ at each stage against your environment. This creates the skeleton of the attack model.
4: Analyze vulnerabilities and control coverage
Assess your current system for vulnerabilities and security control gaps that correspond to the attack path.
For each step/technique in the model, ask:
- Do we have a control to prevent or detect this?
- Are there known vulnerabilities that would make this step easier for the attacker?
Document where controls might fail or where vulnerabilities exist (for instance, a missing EDR might mean a payload execution could go undetected).
5: Simulate attack paths
With the theoretical model in hand, execute simulations or breach and attack simulation exercises to validate it. This could mean running a red team exercise or using continuous automated red teaming tools to carry out the steps in a safe manner.
The idea is to see if the attack model holds true in practice and to observe how your security responds at each stage.
6: Measure impact and document findings
Observe what happened during simulation, which attacks succeeded, which were blocked and what impact a successful step had. Document the findings thoroughly.
For example: “Phishing simulation: 2 out of 10 users clicked; malware was executed and EDR failed to detect it.” Quantify potential impact (e.g. “attacker could access 5000 customer records in database”). This step turns the model into evidence.
7: Prioritize remediation and re-test
Use the findings to prioritize fixes. If the model revealed certain high-risk gaps (say, weak segmentation allowed easy lateral movement), plan remediation for those first. Implement the improvements, then re-test by running the attack model (or a variant of it) again later.
This continuous cycle ensures that once a weakness identified by the model is fixed, it stays fixed (and if something breaks again, you catch it).
Organizations integrate attack modeling into their security management process by using all these steps, it’s not a one-time activity, but a cycle of model, test, fix and repeat. Over time, this dramatically improves security maturity and resilience.
Best practices for effective attack modeling
To get the most value from cyber attack modeling, organizations should follow some best practices drawn from industry experience and frameworks:
Map threats to known frameworks
Use established models like MITRE ATT&CK or the Cyber Kill Chain to ensure consistency in your attack models. Mapping your scenario to these frameworks makes sure you cover all relevant Tactics, Techniques and Procedures (TTPs) and speak a common language.
Maintain updated models with current threat intelligence
Threat tactics are constantly evolving. Regularly update your attack models with the latest threat intelligence on attacker TTPs and campaigns targeting your industry. An effective model today might be obsolete next year if new exploits or attack vectors emerge.
Use breach and attack simulation tools for validation
Don’t rely on theory alone. Make use of automation to validate your attack models. Modern breach and attack simulation platforms can execute attack scenarios in production-like environments to see how your controls hold up.
This acts as continuous automated red teaming, allowing you to frequently test your defenses at scale.
Cymulate can automatically run multi-stage attack campaigns (phishing to exfiltration) safely, providing empirical evidence of what would happen and where improvements are needed.
Simulate destructive as well as stealthy tactics
When modeling, include not just data theft scenarios but also destructive ones. Many teams focus on data exfiltration and ransomware, but it’s wise to simulate data destruction tactics (e.g. disk wiping, encryption of backups) as found in MITRE’s Impact tactics (TA0040).
This ensures you’re prepared for attackers whose goal is sabotage or maximal damage, not just theft. Testing your resilience against destructive techniques (like corrupting databases or wiping servers) is crucial for comprehensive readiness.
Involve cross-disciplinary teams
Involve both red teams (offense) and blue teams (defense), and even IT operations in building and reviewing attack models.
Red teamers contribute to the attacker's perspective and creativity, while blue teamers and engineers contribute knowledge of the environment and defensive measures.
This collaboration leads to more realistic models and also shared understanding. In practice, some organizations run purple team exercises (joint red-blue) specifically to develop and refine attack scenarios. A collaborative approach breaks down silos and improves the overall security culture.
Document multiple attack types
Don’t limit modeling to one type of threat. Over time, develop a library of scenarios covering different attack types, e.g. a supply chain attack model, an insider threat model, a cloud account takeover model, etc.
This helps ensure you’re not only prepared for the “common” attacks but also have plans for less frequent yet high-impact scenarios. Each model will teach something new about your security posture.
The goal is to move from reactive to proactive: constantly anticipating attackers’ moves and rehearsing defenses, so that if (or when) a real attack comes, it’s not uncharted territory.
How to measure the effectiveness of cyberattack modeling
Like any security initiative, attack modeling should be measured to ensure it’s delivering value. Simply creating diagrams isn’t enough, we need to track outcomes that show improved resilience.
Here are ways to measure the effectiveness of your cyber attack modeling efforts:
1: Define measurable outcomes
Establish concrete metrics that link attack modeling to security performance. For example, you might track:
- Coverage: % of MITRE ATT&CK techniques or kill chain stages modeled and tested.
- Detection rate: % of simulated attacks detected by SIEM/EDR/XDR.
- Time to detect (MTTD): How quickly security controls identify simulated attacks.
- Time to respond (MTTR): How quickly incidents are contained once detected.
- Success/failure rate of simulations: How many simulated attacks succeeded vs. blocked.
- Remediation closure rate: % of prioritized gaps fixed and successfully re-tested.
Over time, you can report these metrics to leadership to demonstrate value (e.g. “We increased our attack detection rate from 60% to 90% in the last 6 months through attack modeling and validation exercises.”).
2: Benchmark against baselines
To know if you’re improving, compare your metrics against both internal and external baselines. Internally, use your initial assessment as a baseline, for example, the first time you ran a full attack simulation, maybe only 50% of steps were caught.
Six months and several fixes later, maybe 80% are caught. Show that positive trend. Externally, you can compare against industry benchmarks or peer data if available. Resources like the annual MITRE ATT&CK evaluations (which test EDR products against ATT&CK techniques) can provide a sense of how well top solutions perform in detection, you can gauge if your detection capabilities are on par.
Similarly, if an industry report says “on average it takes 24 hours to detect a breach,” and your drills show you can do it in, say, 4 hours, that’s a competitive advantage to highlight.
The point is to use baselines to contextualize your performance and drive continuous improvement. If progress stalls or lags behind peers, that’s a sign to invest more effort or resources in the program.
3: Tie to business outcomes
Translate technical results into business risk terms. Through regular attack modeling, you might demonstrate a reduction in breach likelihood or impact. Maybe before, a certain attack path had a high probability of success, but after improvements, you’ve reduced that probability significantly (lowering overall risk).
Or, perhaps your cyber insurance premiums are lowered because you can show underwriters that you conduct rigorous attack simulations and have fewer security gaps. Also consider compliance and audit outcomes, effective attack modeling provides tangible evidence for auditors that you are testing controls (which can satisfy requirements for frameworks like ISO 27001, NIST CSF, etc.).
And don’t forget cost savings: by finding and fixing weaknesses proactively, you potentially avoid the much higher costs of a real breach. Businesses can also save money by optimizing security investments.
Measuring effectiveness might look like: “Over the past year of attack modeling, we increased our MITRE technique coverage from 60% to 95%, improved phishing detection time from 8 hours to 1 hour, and closed 100% of critical findings. Consequently, our assessed risk of a major customer data breach dropped by 40%, and we passed our last audit with zero major findings, a direct result of our continuous testing program.”
Those kinds of results show that attack modeling is not just an academic exercise but a cornerstone of your Continuous Security Validation and risk management strategy.
Bring cyberattack models to life with Cymulate
Developing cyber attack models is only half the battle, to truly benefit, you need to continuously exercise and validate them.
This is where Cymulate can be revolutionary. Cymulate operationalizes attack modeling through continuous, automated testing, effectively bringing your cyberattack models to life.
It combines breach and attack simulation with continuous automated red teaming capabilities to safely mimic real threats end-to-end, so you can see how your defenses stand up in real time.
With Cymulate, you can launch simulated attack campaigns that follow the same multi-stage patterns as your attack models, whether it’s a ransomware outbreak, a supply chain compromise, or an insider data leak scenario.
The platform will then report exactly which steps succeeded, which were detected, and where improvements are needed, delivering actionable remediation guidance.
Over time, Cymulate helps you trend these metrics and continuously hone your security posture. In essence, it serves as an exposure management platform that integrates attack modeling into daily security operations, ensuring your team is never complacent and your controls are always tested against the latest threats.
Ready to turn your attack models into action?
With Cymulate, you can automate and scale attack simulations tailored to your environment. We invite you to take the next step: Request a demo of the Cymulate Platform and see firsthand how continuous, automated attack modeling can fortify your security strategy.
Frequently asked questions
Threat modeling identifies potential threats, vulnerabilities, and controls, asking “what can go wrong?” Attack modeling zooms in on the attacker’s path, detailing the steps an adversary could take to exploit those weaknesses.
In short: threat modeling is broad and preventive, attack modeling is scenario-specific and simulative. Both are complementary and often overlap.
Yes. Attack models can start from trusted access (e.g. a malicious insider) or unconventional entry points like supply chain compromises or IoT devices.
Frameworks like MITRE ATT&CK cover insider activity, and attack trees/graphs can map any path. Custom scenarios ensure organizations prepare for both common and less traditional threats.
Attack models should be treated as living documents. Update them after system changes, new threat intelligence, or major incidents.
For dynamic environments, quarterly reviews are recommended; at minimum, review every 6 months. Regular updates ensure models reflect current threats and defenses.