Enumeration
Enumeration is fundamentally changing security dynamics by making information gathering more accessible and efficient for both attackers and defenders.
Attackers can quickly identify vulnerabilities, network configurations, and potential weaknesses, enabling them to plan targeted attacks with greater precision.
On the flip side, defenders use enumeration to actively identify and address potential security gaps. The increased use of automation and sophisticated tools has amplified the power of enumeration even more. Every day is a test of adaptability, strategy, and resilience.
What Is Enumeration in Cybersecurity?
At its core, enumeration in cybersecurity refers to systematically gathering detailed information about a target system, network, or application. This information can range from usernames and operating system details to open ports and active services.
The process serves a dual purpose:
Ethical use: In penetration testing, enumeration is used to identify vulnerabilities and assess system weaknesses. For example, penetration testers might gather information about an organization's email server configuration to recommend better security measures.
Malicious use: Attackers use enumeration to map systems, identify weaknesses, and launch attacks. For instance, discovering a valid username through enumeration can pave the way for brute-force login attempts.
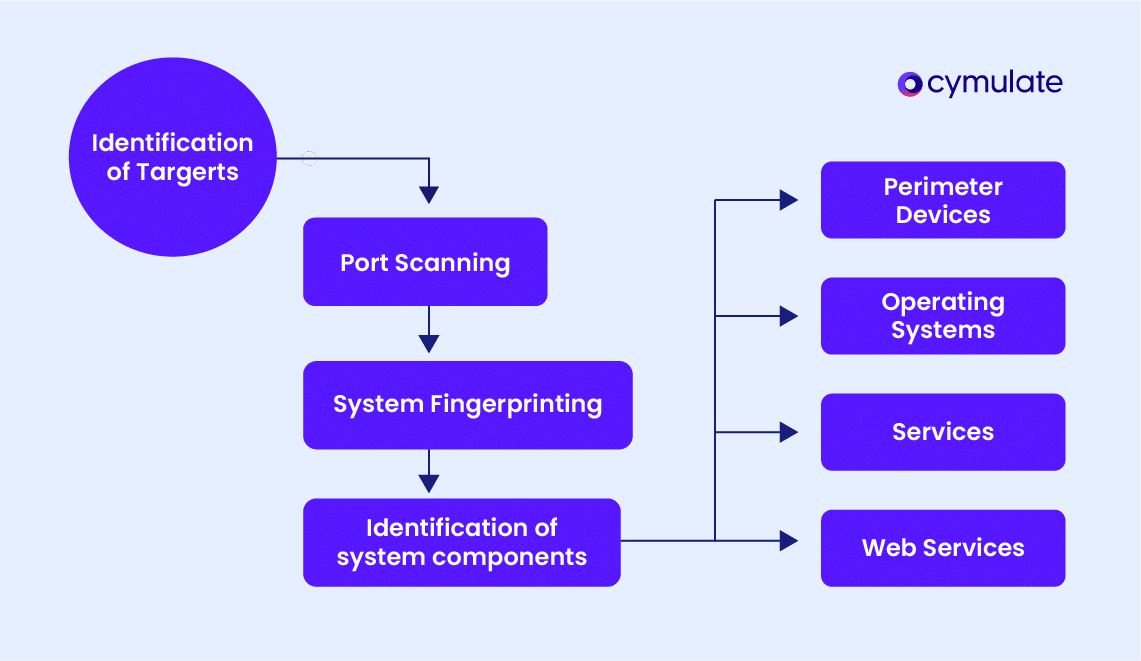
Examples of data gathered through enumeration
- Usernames and group memberships.
- System configurations and software versions.
- Running services and open network ports.
- Password policies and configurations.
Enumeration represents a critical step in both ethical and malicious activities, making it vital to understand its nuances and implement countermeasures.
Types of Enumeration
1. User enumeration
User enumeration involves identifying valid usernames on a system. This typically occurs through login portals, email systems, or APIs that inadvertently reveal whether a username exists. Attackers exploit these details to narrow down their attack targets.
For instance, a login page that states “Username not found” gives attackers a clue that invalid usernames are being filtered, inadvertently confirming valid ones. Avoiding specific error messages can help mitigate such attacks.
2. Network enumeration
Network enumeration focuses on mapping the network’s topology and identifying devices within it. Attackers use network enumeration to pinpoint entry points and high-value assets that they can exploit for further attacks.
Tools like Nmap can be used to discover IP addresses, open ports, and active protocols. By reducing network exposure, such as closing unnecessary ports, organizations can mitigate this type of threat.
3. System enumeration
System enumeration involves uncovering operating system details, including versions and patch levels, which attackers can use to identify and exploit vulnerabilities.
For example, identifying an outdated Windows Server version can make it a target for known vulnerabilities. Keeping systems updated and patched is critical to minimizing risks from system enumeration.
4. Service enumeration
Service enumeration identifies active services and their configurations. Attackers exploit this information to find vulnerable services that they can target.
Such as detecting an exposed database server running on port 3306 could indicate a configuration weakness that might allow unauthorized access. Hardening service configurations and restricting access can significantly reduce these risks.
Detection of Enumeration Attacks
Identifying enumeration activities early can prevent attackers from advancing their objectives. Effective detection involves recognizing key indicators and using specialized tools.
- Unusual network traffic: Unusual network traffic patterns, such as repeated scans or requests to discover open ports or services, can indicate enumeration attempts. A sudden spike in network traffic focused on specific ports might signal an attacker attempting to map the network. Monitoring for repeated or anomalous scanning activities is essential for detecting enumeration in its early stages.
- Multiple failed login attempts: Repeated failed login attempts can indicate attempts to brute-force usernames or passwords, a common tactic in user enumeration. An attacker trying different username-password combinations repeatedly in a short timeframe is a clear indicator of malicious activity. Implementing account lockout policies and using multi-factor authentication can help deter such attempts.
- Increased probing activity: Unauthorized attempts to access specific protocols or resources can indicate increased probing activity related to enumeration. Repeated requests to access restricted services or protocols that are not commonly used within the network can be a red flag.Regularly monitoring network access attempts and maintaining a baseline of normal network behavior can aid in identifying these probing activities.
Tools for Enumeration Detection
Intrusion Detection Systems, such as Snort or Suricata, monitor network activity for suspicious patterns like repeated scans or unusual traffic flows. These systems are vital for detecting enumeration attempts in real-time and enabling security teams to respond promptly.
Security Information and Event Management (SIEM) solutions like Splunk centralize log monitoring and analysis, making it easier to identify anomalies across the network. These tools provide a comprehensive view of network activity, helping to correlate different indicators of enumeration and raise timely alerts.
Best Practices for Monitoring
- Regular log analysis: Regularly analyzing system and network logs for unusual activity is crucial for early detection of enumeration attempts. Proactive log analysis can help identify suspicious patterns, allowing for timely mitigation of threats.
- Configure alerts: Configuring alerts for repeated failed login attempts or high volumes of network traffic is an effective strategy for detecting enumeration. Alerts provide immediate notifications of suspicious activities, enabling a swift response to potential threats and limiting the window of opportunity for attackers.
Enumeration Attacks: Mitigation Techniques
1. Minimize exposure
Minimizing exposure involves reducing the amount of publicly accessible information that attackers can use to conduct enumeration.
This includes removing unnecessary DNS records, securing WHOIS information, and limiting access to internal directories or personnel contact details. By reducing this exposure, organizations make it harder for attackers to gather information that can be used for targeted attacks.
An organization might hide their employee directory from public view to prevent attackers from obtaining valid usernames and email addresses.
2. Implement strong authentication
Implementing strong authentication mechanisms, such as Multi-Factor Authentication (MFA), is crucial for preventing user enumeration.
By adding an extra layer of verification, MFA makes it much more challenging for attackers to brute-force their way into systems, even if they have obtained some valid usernames.
A login portal that requires a time-sensitive code sent to a user's phone in addition to their password can stop an attacker who only knows the username and password.
3. Network segmentation
Network segmentation involves dividing a network into smaller subnetworks, thereby limiting access to sensitive systems and reducing the attack surface for enumeration.
This ensures that even if attackers gain access to one part of the network, they cannot easily move laterally to access critical resources.
Segmenting a payment processing system from the main corporate network helps protect sensitive financial data from attackers who might gain access to less critical parts of the network.
4. Service hardening
Service hardening entails disabling unused services, changing default configurations, and applying security patches regularly.
By doing so, organizations can eliminate potential vulnerabilities that attackers might exploit during enumeration.
Disabling Telnet and using SSH instead for remote access provides a more secure configuration, minimizing the risk of attackers exploiting outdated or less secure services.
By implementing these measures, organizations can significantly reduce the risks associated with enumeration attacks.
Prevention of Enumeration Attacks
Preventing enumeration requires a proactive approach. Here are some key actionable strategies:
Secure login mechanisms
To secure login mechanisms, it is crucial to avoid revealing whether a username exists through error messages like “Invalid username” or “User not found.” Instead, use generic responses such as “Invalid credentials.”
This prevents attackers from easily determining valid usernames, thereby reducing the risk of targeted brute-force attacks. Additionally, implementing rate limiting for login attempts can further protect against automated attacks by slowing down repeated access attempts.
Firewalls and access controls
Firewalls and access controls are critical for restricting an attacker’s ability to probe network resources. By blocking unnecessary ports and protocols, organizations can significantly reduce their attack surface and prevent unauthorized access to sensitive systems.
Configuring firewalls to allow only the required network traffic helps minimize exposure and mitigates the risks associated with network enumeration.
A web server should be configured to block all ports except those needed for HTTP (port 80) and HTTPS (port 443) traffic. This prevents attackers from probing unused ports that may contain vulnerabilities.
Regular security assessments
Regular security posture assessments, such as penetration testing and vulnerability scans, are essential for proactively identifying and mitigating weaknesses before attackers can exploit them.
These assessments help organizations understand their security posture and identify potential vulnerabilities that may be used in enumeration attacks.
By regularly evaluating systems and applications, organizations can stay ahead of emerging threats and ensure that their defenses remain robust.
Employee training
Employee training is a considerable component of preventing enumeration attacks. Staff should be educated about social engineering techniques that attackers use to gather information that could be leveraged during an enumeration attack.
Employees must learn how to recognize phishing emails, pretexting attempts, and other tactics that could inadvertently provide attackers with valuable data.
Prevention measures should be integrated into the organization’s broader security framework, ensuring consistent protection against enumeration threats.
Defend Against Enumeration Threats with Cymulate
Cymulate empowers organizations to detect, mitigate, and prevent enumeration threats.
Role in prevention and detection
- Enumeration simulation: Cymulate allows teams to simulate enumeration attacks, helping identify vulnerabilities and improve defenses.
- Continuous validation: The Cymulate platform ensures that security controls are automatically tested against real-world enumeration tactics.
Integration with phishing awareness campaigns
Cymulate empowers organizations to educate employees on how attackers use social engineering for enumeration. The platform records user interactions with mock phishing emails, identifying risky behaviors and enabling targeted training.
Exposure validation
Cymulate provides real-time visibility into exploitable vulnerabilities through exposure validation, allowing organizations to address risks before attackers can exploit them. With actionable recommendations, the platform strengthens defenses against enumeration and related threats.
Final Thoughts
On the one hand, enumeration provides valuable insights for penetration testers to identify and fix system vulnerabilities; on the other hand, it equips attackers with the information needed to exploit those same weaknesses.
This duality makes enumeration both powerful and dangerous, depending on who wields it. Organizations must go beyond reactive measures and adopt proactive strategies to detect, mitigate, and prevent enumeration-based threats before they escalate and lead to a potential breach.

