DORA Compliance Checklist: A Practical Guide for Cybersecurity Teams

The EU’s Digital Operational Resilience Act (DORA) is a sweeping regulation aimed at fortifying the financial sector’s defenses against cyber threats and ICT disruptions.
In effect since January 2025, DORA requires banks, investment firms, insurance companies, and other financial entities (plus their critical tech providers) to be “DORA compliant.” DORA compliance for banks means implementing rigorous cybersecurity controls, operational resilience frameworks, and ongoing validation to meet regulatory expectations.
Key Highlights
- DORA compliance is a new EU-wide cybersecurity framework that mandates five pillars of resilience, from robust risk management to continuous security testing for banks and financial services.
- Why it matters: DORA compliance and DORA safety reduce cyber risks through measures like vulnerability scanning and DORA compliance practices, strict third-party oversight, and standardized incident reporting, strengthening the entire financial ecosystem against attacks.
- DORA checklist for teams: A 10-step DORA compliance checklist covers everything from scoping and gap analysis to board training and ongoing improvement, aligning with DORA’s pillars and Article requirements.
- Cymulate Offerings: Cymulate provides an automated solution to help you continuously validate controls, test defenses, and generate audit-ready reports making it easier for your team to stay DORA compliant and resilient.
What is DORA?
The Digital Operational Resilience Act (DORA) is a pivotal regulation from the European Union designed to ensure that financial entities can withstand, respond to, and recover from all types of Information and Communication Technologies (ICT)-related disruptions and threats.
With cyberattacks increasingly targeting the financial sector, DORA mandates comprehensive cybersecurity and operational resilience across the entire digital ecosystem — from internal systems to third-party services.
Why does DORA safety matter?
At its core, DORA ensures secure and authenticated device communication, robust network security compliance, and a standardized approach to cyber risk management across EU financial services.
- Unified security baseline: DORA sets a common standard for cyber risk management across EU financial services, ensuring every institution, large or small, maintains a robust baseline of security controls. This standardized approach to cyber risk management closes gaps between organizations and eliminates weak links.
- Stronger defenses against attacks: By mandating proactive measures like regular vulnerability scanning, penetration testing, and secure device authentication, DORA helps organizations identify and fix security weaknesses before attackers can exploit them. Financial entities must continuously test their defenses under DORA, which significantly reduces the risk of successful cyberattacks.
- Reduced downtime and data loss: DORA’s requirements (e.g. comprehensive backup and recovery plans, network segmentation, and data encryption for DORA compliance) mean that if an incident does occur, firms can contain the damage and restore services faster. This resiliency minimizes downtime, protects sensitive customer data, and preserves the integrity of critical financial operations.
- Sector-wide resilience and trust: DORA promotes information-sharing of threat intelligence among institutions, fostering collaboration through communities like FS-ISAC. When firms openly share indicators of compromise and best practices, the entire financial sector becomes more resilient.
Who must comply with DORA?
DORA applies to a wide range of financial and ICT-related entities within the EU and who operate with EU-based clients, including:
- Banks
- Investment firms
- Insurance companies
- Payment service providers
- Credit institutions
- ICT third-party service providers (e.g., cloud platforms, data centers)
Why it matters: These institutions operate in high-risk digital environments, where secure device authentication and encrypted communications are essential to protect customer data and financial integrity.
DORA compliance requirements: Meeting the five pillars
To align with DORA, organizations must comply with five key pillars. Below is a concise DORA compliance requirement list, tailored for cybersecurity and compliance teams.
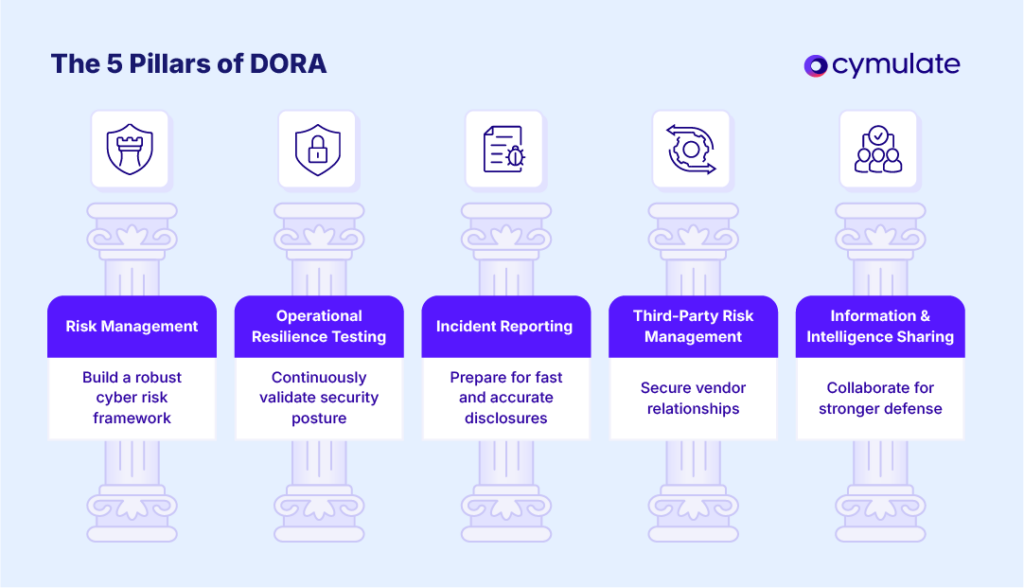
1. Risk management: Build a robust cyber risk framework
Under DORA, financial entities must identify, assess, and mitigate ICT risks systematically. They must implement frameworks that address critical areas of risk.
Action steps:
- Implement a formal ICT risk management framework
- Conduct regular risk assessments of internal systems and third-party services
- Classify and prioritize assets based on criticality
- Establish device authentication policies to verify trusted endpoints
- Integrate vulnerability management and patching into operational workflows
2. Incident reporting: Prepare for fast, accurate disclosures
DORA mandates that significant ICT incidents be reported within strict timeframes to competent authorities. Details must be provided about any incident as well as its impact and steps that were taken for remediation.
Action steps:
- Establish an internal incident response and escalation process
- Use automated tools to detect, log, and report security incidents
- Ensure reports include impact assessments, root causes and cybersecurity risk mitigation steps
- Train security staff on DORA reporting obligations
3. Operational resilience testing: Continuously validate security posture
To comply with DORA, entities must regularly test their digital resilience under realistic threat conditions. These include conducting vulnerability assessments, penetration testing as well as stress testing. These tests will show whether or not systems can withstand a variety of disruptions or attacks.
Action steps:
- Conduct scenario-based and threat-led penetration testing (TLPT)
- Test authentication and data encryption for DORA compliance
- Simulate attacks on communication protocols and data flows
- Continuously validate controls across all attack vectors
4. Third-party risk management: Secure vendor relationships
DORA enforces strict oversight of ICT service providers to minimize third-party vulnerabilities. Many past high-profile data breaches and security incidents begin with vulnerabilities presented by third-party access to critical systems and infrastructure, so securing those relationships is of paramount importance to meet DORA security requirements.
Action steps:
- Maintain an inventory of all ICT third-party providers
- Assess vendors for compliance with DORA-aligned security standards
- Monitor access privileges and ensure secure device communication
- Include security SLAs in vendor contracts
5. Information and intelligence sharing: Collaborate for stronger defense
DORA promotes proactive sharing of threat intelligence among financial institutions to build collective resilience.
Action steps:
- Join threat intelligence sharing communities (e.g., FS-ISAC)
- Integrate shared indicators of compromise (IOCs) into detection systems
- Leverage threat intelligence feeds to inform simulations and test defenses
10-Step DORA Compliance Checklist
Even though we outlined key action items under each pillar above, it’s helpful to have a comprehensive, step-by-step plan.
The following 10-step DORA checklist guides cybersecurity teams from initial assessment to ongoing improvement, aligning each step to DORA’s pillars and article requirements:
1: Scope and gap analysis
Determine if and how DORA applies to your organization, and identify any compliance gaps.
Start by confirming your entity type and obligations, DORA’s scope covers many financial services and critical ICT providers. A compliance or security officer should perform a gap analysis against DORA’s requirements, reviewing your current risk management, incident response, testing, third-party oversight, and policies.
This baseline assessment (often done via a checklist or audit) will highlight what’s already in place and what’s missing.
Responsibility: Compliance officers and security leadership lead this step, reporting findings to the board. (DORA Article 2 defines the scope of financial entities.)
2: Governance and risk management
Establish strong governance structures and a formal ICT risk management framework.
Under Article 5 of DORA, the board and senior management must implement and oversee an internal ICT risk management and control framework. This means putting in place clear roles and responsibilities for cyber risk, allocating budget and resources for resilience, and approving key policies (information security, business continuity, etc.).
If you don’t already have one, develop a comprehensive cyber risk management policy and get board sign-off. Ensure independence of control functions (risk, audit) and set your organization’s risk tolerance levels.
Responsibility: Board of Directors and the CISO or Risk Officer jointly drive this step, with the board bearing ultimate accountability for ICT risk. (Key DORA Articles: 5 and 6 cover governance and risk management requirements.)
3: Incident reporting setup
Implement an ICT incident management process that meets DORA’s criteria.
DORA Article 17 requires firms to have a process to detect, manage, and report ICT incidents. Establish formal procedures for incident handling (from triage to recovery) and ensure you can classify incidents by severity.
Set up internal reporting channels to escalate major incidents quickly to executives and, when needed, to regulators. Prepare templates for incident reports so that if a “major ICT incident” occurs, you can swiftly provide all required information to your national competent authority.
Responsibility: The Security Operations Center (SOC) or incident response team is responsible for execution, with oversight from the CISO. Coordinate with your compliance team for external reporting obligations. (Key DORA Articles: 17–19 cover incident management and reporting obligations.)
4: Resilience testing program
Develop a continuous digital operational resilience testing program.
DORA obligates financial entities to regularly test their cyber defenses, not as a one-off, but via an ongoing program. Create a testing schedule that covers all critical systems and controls. This should include frequent vulnerability scans, annual or biannual penetration tests, tabletop exercises for cyber crisis scenarios, and periodic full-scope Threat-Led Penetration Testing (for those entities required to do TLPT).
Document the plan and ensure tests are conducted by qualified, independent parties (you may use internal teams or hire external specialists, as long as they’re not the ones who maintain the systems being tested). After each test, implement any remediation or improvements identified.
Responsibility: The cybersecurity team (often the red team or security assurance group) leads this, in collaboration with IT. Significant test results should be reported up to management. (Key DORA Articles: 21–22 set out general testing requirements; Article 23 requires TLPT at least every 3 years for significant institutions.)
5: Third-party risk management
Strengthen oversight of ICT third-party service providers.
As required by DORA, craft a formal ICT third-party risk management policy and inventory. Identify all service providers that support critical or important functions. For each, evaluate their security controls and compliance posture.
Update contracts to include DORA’s required provisions (e.g. the provider’s incident notification duty, audit rights, sub-contractor conditions, and termination rights).
Responsibility: Vendor Management or Procurement teams own the inventory and contract updates, with the CISO/CTO and legal counsel collaborating. Risk and compliance teams should review third-party risk assessments. (Key DORA Articles: 28–31 cover third-party risk management and contract requirements.)
6: Information sharing arrangements
Engage in cyber threat information-sharing as appropriate.
While voluntary, DORA Article 45 encourages financial entities to share threat intelligence to enhance collective security. Decide how your organization will participate: this could mean joining FS-ISAC or a similar group, or setting up bilateral info-sharing with peer institutions.
Put in place any necessary agreements (e.g. NDAs or Memoranda of Understanding) that outline what information can be shared and how it will be protected.
Responsibility: The CISO or threat intelligence lead typically coordinates external information-sharing. Make sure compliance/legal is aware of these efforts to align with privacy requirements. (Key DORA Article: 45 relates to information-sharing arrangements on cyber threats.)
7: Documentation and record-keeping
Maintain thorough documentation as evidence of compliance.
DORA places heavy emphasis on documentation, if it’s not written down, it doesn’t count. Ensure you document every aspect of your DORA compliance efforts.
This includes your risk management framework (policies, risk assessments, risk register), incident logs and post-incident analysis reports, results of all resilience tests (with remediation plans), third-party risk assessments and an up-to-date vendor register, change management records, and training records for staff. Keep these documents organized (consider a central compliance repository) and secure.
Responsibility: The Compliance or Risk Management function usually oversees documentation. However, all teams (IT, SecOps, etc.) should contribute by producing and updating records for their activities. (Key DORA Articles: 16–17 cover incident record-keeping; 28 covers the third-party register; 5 requires documentation of the risk framework.)
8: Board accountability and training
Engage senior management and provide DORA-focused training.
DORA makes it clear that the management body (board) is ultimately accountable for ICT risk and resilience. Step 2 established governance; now ensure ongoing board involvement. Provide regular updates to the board on DORA compliance status and cybersecurity risk.
Have the board formally approve major elements like the risk strategy and incident response plan. Importantly, arrange training for board members and executives on DORA, they need to understand their responsibilities and be able to make informed decisions on ICT risk tolerance.
Responsibility: The Board and CEO are accountable; the CISO, CRO, or compliance head typically briefs the board and orchestrates training sessions (often with help from external experts on regulation). (Key DORA Article: 5 underscores management body responsibilities and knowledge upkeep.)
9: Continuous monitoring and improvement
Establish a cycle of ongoing evaluation and improvement.
Compliance is not a one-time project, regulators expect continuous adaptation. DORA implicitly requires firms to periodically review and update their risk management frameworks and controls (at least annually, or after significant incidents).
Set up metrics and Key Risk Indicators (KRIs) to monitor your cyber resilience (e.g. number of high vulnerabilities open, mean time to detect/respond to incidents, etc.).
Use these metrics and the outcomes of tests/audits to drive improvements. For example, if a penetration test finds a recurring weakness, feed that back into your risk assessment and remediate promptly.
Responsibility: The CISO and risk management team should own the continuous improvement program. They report trends and needed enhancements to senior management. (Tied to DORA’s general risk management principle of ongoing improvement, e.g. Article 5 requires annual review of the ICT risk framework, and Article 17 requires post-incident analysis to learn lessons.)
10: Audit readiness and regulatory compliance assurance
Prepare to demonstrate DORA compliance at any time.
Regulators can and will assess firms for DORA compliance through audits or examinations. Be audit-ready by conducting internal audits or mock inspections. This means reviewing whether each DORA requirement is met and evidence is on hand.
Test yourself: can you quickly produce documentation of your last risk assessment or an incident report if asked? Do you have an audit trail of changes and decisions related to operational resilience? DORA empowers authorities to request information and even perform on-site inspections, so having an organized compliance folder (and designated point of contact for regulators) is wise.
Non-compliance carries steep penalties, fines can range up to 2% of annual turnover or €10 million for financial entities, and regulators may impose daily penalty payments up to 1% of average daily turnover for critical ICT providers.
Responsibility: The compliance officer or internal audit department coordinates audit preparedness, working closely with all other teams to gather evidence. Regular reporting to the board on compliance status is also recommended. (DORA enforcement and oversight provisions empower regulators to issue fines and request information, see Article 50+.)
It’s essential to align each step with the relevant DORA articles and guidance, as summarized above. Below is a quick-reference table summarizing the 10 steps, their focus, and related DORA provisions:
| Step | Summary | DORA Reference |
| 1. Scope & gap analysis | Identify in-scope areas and assess current compliance gaps | Art. 2 (Scope) |
| 2. Governance & risk management | Implement ICT risk framework with board oversight | Art. 5 (Management body duties) |
| 3. Incident reporting | Establish incident handling and reporting process | Arts. 17–19 (Incident management & reporting) |
| 4. Resilience testing | Conduct regular security testing (vuln scans, pen tests) | Art. 23 (TLPT requirement) |
| 5. Third-party risk | Manage ICT third-party risks; update contracts & register | Arts. 28–30 (Outsourcing requirements) |
| 6. Information sharing | Participate in threat intel sharing (e.g. FS-ISAC) | Art. 45 (Info-sharing arrangements) |
| 7. Documentation | Maintain logs, registers, and evidence of all compliance efforts | Art. 16–17 (Incident logs); Art. 28 (Vendor register) |
| 8. Board oversight & training | Engage board and train management on DORA roles | Art. 5 (Board responsibility) |
| 9. Continuous improvement | Monitor KPIs, analyze incidents, update controls regularly | Art. 5 (Annual review of framework) |
| 10. Audit readiness | Prepare audit trails and reports; be ready to prove compliance | Art. 50 (Supervisory enforcement powers) |
How to implement DORA
Implementing DORA is less about checking boxes and more about embedding resilience into how your organization operates every day. Success depends on leadership commitment, clear planning, and integrating requirements into routine processes.
Key steps to focus on:
- Secure executive buy-in: Boards and senior leaders must recognize DORA’s importance and commit resources.
- Build a cross-functional team: Involve cybersecurity, IT, risk, compliance and business continuity to drive the program together.
- Follow a structured roadmap: Use the 10-step checklist to guide actions, from gap analysis to updating policies, playbooks and testing schedules.
- Leverage existing frameworks: Map controls to standards like ISO 27001, NIST CSF and ITIL for efficiency and alignment.
- Stay current with guidance: Monitor updates from the European Supervisory Authorities and ENISA to refine your approach.
- Integrate into daily workflows: Make risk assessments part of system rollouts and vendor onboarding so compliance becomes routine.
Consider external support, whether consultants for specialized tasks or automation tools for continuous monitoring to simplify complex requirements. Over time, these practices shift DORA from a regulatory project into a natural part of your organization’s culture of resilience.
DORA compliance deadlines and what they mean for you
The DORA compliance deadline of January 17, 2025 marked the official start of full enforcement. Unlike other regulations, DORA offered no grace period organizations had two years from adoption in January 2023 to prepare, and regulators now expect every in-scope entity to be ready.
What the deadline means for teams:
- If you’re not ready: Immediate action is critical. Any gaps such as missing incident response plans or incomplete vendor registers could trigger scrutiny or penalties.
- If you’re compliant: The work doesn’t stop. DORA is now an ongoing obligation, requiring continuous monitoring, updates and reporting.
Ongoing focus areas:
- Watch for new technical standards and detailed rules issued by the European Supervisory Authorities (EBA, ESMA, EIOPA) and national regulators.
- Add DORA oversight to your compliance calendar with regular reviews and audits (quarterly or biannual) to ensure controls remain aligned.
- Stay proactive so you avoid regulator surprises and continue building resilience, not just compliance.
January 2025 wasn’t the finish line, it was more of a starting point for continuous, enforceable operational resilience under DORA.
What happens if you don’t comply? DORA compliance penalties explained
Organizations that are required to comply with DORA regulations but do not do so could face significant consequences if an incident leads to a finding of non-compliance. As such, non-compliance with DORA can lead to:
- Regulatory fines and legal consequences.
- Increased exposure to cyberattacks and data breaches.
- Reputational damage and loss of customer trust.
- Potential restrictions on business operations by regulators.
In particular, the financial penalties for DORA non-compliance can be massively detrimental. DORA allows leaders to impose financial penalties on ICT providers amounting to 1% of the provider’s average daily worldwide turnover in the previous business year.
Failing to implement DORA’s device and network security mandates could result in unverified endpoints accessing sensitive systems — a risk too great in today’s threat landscape.
How Cymulate strengthens your DORA compliance
Cymulate can help your organization check down the DORA compliance checklist. Cymulate offers an automated, continuous exposure validation platform that aligns directly with DORA’s cybersecurity and operational resilience objectives.
Key Cymulate capabilities
- Real-time exposure validation and management: Understand and reduce your attack surface dynamically.
- Continuous breach and attack simulation: Mimic attacker tactics to test your defenses 24/7.
- Support for audit and reporting: Provide measurable, audit-ready data to support DORA compliance reviews.
- Device and network security validation: Ensure encryption, access controls and authentication mechanisms are tested and effective.
Utilizing the Cymulate platform, your organization can leverage production-safe testing and validation of your ICT security controls with numerous automated test scenarios and templates. These best practice templates can be scheduled to run on a regular basis to perform assessments of key ICT security controls and processes, including:
- Email and web gateways
- Web application firewalls
- Antivirus and endpoint security
- Cloud workload and container security
- Lateral movement and data loss prevention
- Advanced persistent threat scenarios
- Phishing with full kill-chain campaigns
These assessments highlight areas of risk, identifying gaps and weaknesses that could be exploited by threat actors to disrupt financial operations. The detailed findings offer mitigation guidance to configure and tune your ICT security controls to increase resiliency and lower the risk of a cyber breach.
You'll get the proof you need to achieve DORA compliance. The reports and dashboards provide evidence highlighting the effectiveness of your ICT security controls to prevent and detect the latest cyber attacks.
Stay DORA compliant with Cymulate
The DORA compliance checklist isn’t just about checking regulatory boxes — it’s about building lasting operational resilience in financial sector cybersecurity.
With Cymulate, you gain the tools to proactively test, validate, and reinforce your cybersecurity posture in line with DORA requirements. Learn more about how Cymulate can help by downloading and reading our DORA solution brief.
Ready to simplify and strengthen your path to DORA compliance? Book a demo with Cymulate and see how we can help your team stay DORA compliant, resilient and secure.
Frequently Asked Questions
Is my organization in DORA’s scope?
Yes, if you are a financial entity in the EU (banks, insurers, payment providers, investment firms, crypto-asset service providers) or a critical ICT vendor supporting them.
Can we use external consultancies for DORA compliance?
Yes. Consultants can help with gap assessments, policy design and penetration testing. But accountability remains with your organization, so use them as support, not a substitute.
Does DORA mandate specific technical controls?
No. DORA is principle-based. It expects strong practices like encryption, access controls and patching, but leaves exact methods to your risk analysis and proportionality.
What are DORA metrics?
They are KPIs that track resilience, such as incident response times, vulnerability remediation rates, system uptime and results of resilience tests. Metrics provide evidence of ongoing compliance.
How do we prove compliance?
Through documentation and audit-ready evidence. Keep policies, risk assessments, incident logs, vendor registers, test reports and training records organized and up to date.
What role does vulnerability scanning play?
It’s foundational to resilience testing. Regular scans identify weaknesses that must be fixed quickly. Document scan results and remediation actions to demonstrate continuous risk management.


