For many cyberattacks, it’s all about the data. The sophisticated campaigns include techniques from recon to initial access to lateral movement to command and control, all orchestrated to find and exfiltrate data.
The Cymulate 2024 State of Exposure Management & Security Validation report sheds light on a concerning trend: since 2021, the average data exfiltration Cymulate risk score has increased from 39%.
To measure control effectiveness and baseline security posture, Cymulate uses a proprietary 0 to 100 scoring method based on known industry standards, including the MITRE ATT&CK® Framework, NIST Special Publication 800-50, and other benchmarks.
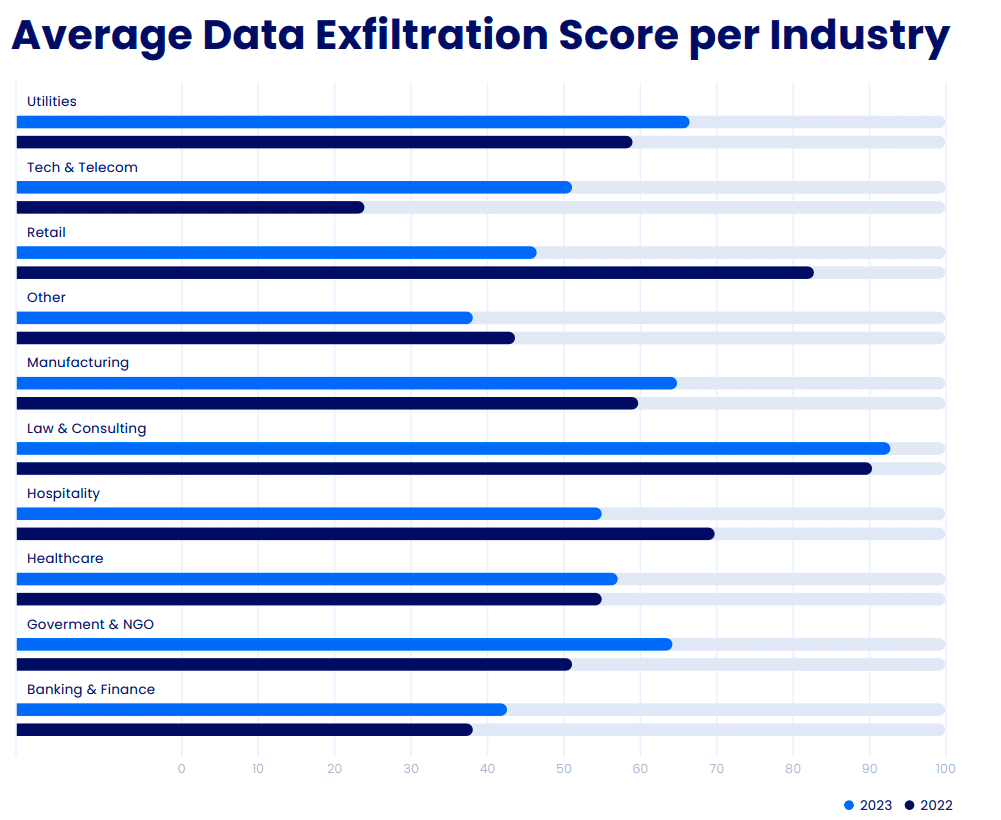
This uptick sends a clear message to businesses to reassess and fortify their data loss prevention (DLP) strategies. Let’s explore further why DLP solutions are at such a disadvantage and the steps you can take to protect your organization from data exfiltration.
Why Traditional DLP Tools are Not Providing Adequate Protection
This increase in the data exfiltration risk for most organizations can be attributed to:
The Evolving Threat Landscape
The digital battlefield is continuously morphing, with attackers continuously engineering new methodologies to sidestep conventional DLP measures. Traditionally, DLP solutions depended heavily on predefined rules and patterns. However, this approach is increasingly ineffective against modern, sophisticated tactics designed to evade these traditional defenses. Our findings highlight organizations’ need to evolve their DLP strategies to counteract these advanced threats effectively.
The Encryption Paradox
While encryption has become a standard practice, enhancing privacy and security for legitimate data transmission, it presents a double-edged sword. Malicious actors now leverage encryption to mask illicit activities, blending seamlessly into regular traffic and evading traditional detection mechanisms. Encryption exploitation increases the need for advanced DLP solutions to distinguish between benign and malicious encrypted traffic.
The Data Deluge Dilemma
The exponential surge in data volume and complexity is another pivotal factor increasing the risk of data exfiltration. As organizations generate and store more data, the challenge of monitoring and securing sensitive information escalates. Existing DLP systems, designed for a less voluminous and complex data environment, are struggling to keep pace with the demands of today’s data-intensive landscape.
Integration and Compatibility Challenges
The rapid adoption of cutting-edge technologies, cloud services, and SaaS applications has revolutionized business operations. However, this technological transformation often pushes DLP considerations to the background. Many traditional DLP solutions encounter difficulties integrating seamlessly with these new-age systems, leaving gaps in an organization’s defense.
Furthermore, the urgency to protect against data exfiltration is amplified by the strict regulatory requirements and the potential financial and reputational damages associated with data breaches. Organizations must not only focus on preventing external threats but also on mitigating risks from within, as insider threats constitute a significant percentage of data breaches.
Proactive Measures and Continuous Assessment
Adopting a proactive stance is essential. Regularly updating security policies, conducting thorough risk assessments, and ensuring continuous monitoring and real-time analysis can significantly enhance the effectiveness of DLP strategies. Additionally, fostering a culture of security awareness among employees can reduce the risk of accidental or intentional internal breaches.
Elevating Security with DLP Control Validation and Detection Engineering
The need to augment DLP control validation becomes even more critical in our pursuit of data security. It’s not just about putting controls in place; it’s about rigorously testing and validating these controls to ensure they perform as expected against evolving threats. This process is vital in identifying potential gaps in our security posture and rectifying them before they can be exploited.
Control validation helps identify vulnerabilities and provides actionable insights for strengthening defenses. Moreover, regular validation exercises encourage a proactive security culture, ensuring measures remain effective against evolving threats and compliance requirements.
Additionally, the role of detection engineering in your security strategy cannot be overstated. It extends beyond prevention, delving into the realm of detecting attempts at data exfiltration swiftly and accurately. Effective detection engineering enables organizations to respond to threats in real-time, mitigating risks and minimizing potential damages. By prioritizing prevention and detection, we can offer a more robust defense against the complex threats of data exfiltration.
For more insights on the importance of security control validation practices, detailed analyses, and actionable advice, read the full report.








