Breach and attack simulation (BAS) tools can automatically spot vulnerabilities in an organization’s cyber defenses, akin to continuous, automated penetration testing. BAS solutions often recommend and prioritize remediation to maximize security resources and minimize cyber risk.
A few vendors refer to advanced BAS solutions as security validation. Several of these tools also assess broader security defenses and potential attack paths, a market known as attack surface management. Artificial intelligence and machine learning are an important part of the BAS market, as automated cybersecurity tools are needed to keep up with the huge volume of vulnerabilities and emerging threats.
We analyzed the market for BAS tools to come up with this list of the top 19 vendors, plus an additional 8 honorable mentions, followed by more on breach and attack simulation technology and buying considerations.
Cymulate
Best for usability and user experience
Cymulate is the first of two Israeli vendors in our top-tier BAS solutions. Founded in 2016, the Rishon LeZion-based vendor specializes in breach and attack simulation and security posture verification. By employing the MITRE ATT&CK framework and mimicking an array of advanced hacker strategies, the Cymulate platform assesses network segments, detects vulnerabilities, and optimizes remediation.
To confront the dynamic threat landscape, Cymulate offers continuous security validation that provides consistent guidance for action. Deploying Cymulate with near-unlimited attack simulations can be completed within minutes via a single lightweight agent.
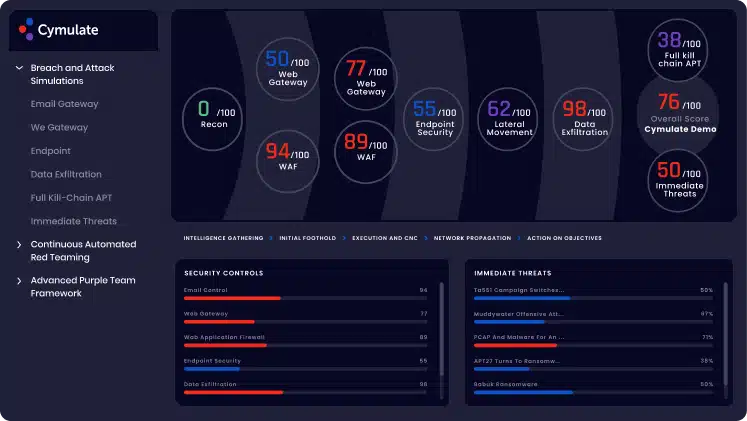
Cymulate Features
- Attack remediation: Allows you to prioritize remediation based on attackable vulnerabilities
- Endpoint security: Detects and prevents endpoint ATT&CK TTPs such as ransomware and worms
- Data exfiltration: Ensures that company sensitive data can not be exfiltrated
- Full kill chain APT: Validate your enterprise defense against APT attack scenarios such as Fin8, APT38, Lazarus and custom scenarios
- Email gateway: Test your security against thousands of malicious email formats, attachments, and URLs
- Web app firewall: Evaluate your security against web apps attack such as OWASP top ten





