What is Vulnerability Prioritization?
Vulnerability prioritization is the process of sorting through detected vulnerabilities, pinpointing those that pose the highest risk, and creating a prioritized patching list designed to minimize exposure.
With new cyber threats emerging daily, organizations face the challenge of managing an overwhelming number of patches. There are thousands upon thousands, if not hundreds of thousands of different patches that might need to be applied within any given environment. This poses a major problem to security teams, as it is not logistically possible to patch everything.
By prioritizing the most critical vulnerabilities, organizations can allocate their resources and focus their efforts on building a robust security posture and preventing costly breaches.

What is Considered a Vulnerability in Cybersecurity?
A vulnerability in cybersecurity refers to any weakness or flaw in a system, network, software or application that can be exploited by attackers to compromise the system’s integrity, confidentiality or availability.
These vulnerabilities can arise from various sources, such as coding errors, misconfigurations, outdated software or even inherent design flaws. Common types of vulnerabilities include:
- Software bugs or code flaws
- Unpatched systems with outdated software
- Misconfigurations in system settings or security policies
- Weak authentication mechanisms, like weak passwords
- Insecure APIs or interfaces
How Vulnerability Prioritization Works
The goal of any vulnerability prioritization method is to emulate the Eisenhower Matrix. Also known as the Urgent-Important Matrix, the Eisenhower Matrix helps deciding on and prioritizing tasks by urgency and importance, filtering out less urgent and essential tasks that can be postponed or ignored altogether.
Each new vulnerability prioritization technology aims at fine-tuning such a matrix based on two main parameters:
- Ensuring optimal security and resilience
- Minimizing the number of vulnerabilities that require patching
There are, however, different paths to achieve that result, with varying degrees of success based on the accuracy and depth of the input data, the ability to integrate the context, and the resulting correlation options.
The Most Common Methods for Prioritizing Vulnerabilities
The most common methods for vulnerability prioritization focus on assessing the risk and impact of each vulnerability, allowing organizations to prioritize patches effectively. These methods include:
- CVSS (Common Vulnerability Scoring System) scores: These numerical scores help assess the severity of vulnerabilities.
- Asset value: Vulnerabilities affecting high-value assets or systems with sensitive data are prioritized.
- Exploitability: Vulnerabilities that are easy to exploit or have known exploits available are given higher priority.
- Potential impact: The damage that could result from an exploit, such as data breaches, financial loss, or service disruption, is considered.
- Business context: The specific industry or business environment influences how vulnerabilities are prioritized, with some vulnerabilities posing more risk based on operational needs.
The Role of Common Vulnerability Scoring System (CVSS)
The “Common Vulnerability Scoring System” (CVSS) is the dominant method used today for vulnerability prioritization. It offers a standardized way to assess and rank vulnerabilities based on their theoretical severity.
CVSS is divided into three key metric groups: Base, Temporal and Environmental. Each metric group assesses different aspects of a vulnerability’s severity.
1. Base Score (Fundamental Severity of the Vulnerability)
The Base score is the most commonly used part of CVSS and evaluates the inherent characteristics of a vulnerability that do not change over time or across environments. It is divided into two components: Exploitability Metrics and Impact Metrics.
Exploitability Metrics measure how easily a vulnerability can be exploited:
- Attack Vector (AV): How the vulnerability can be exploited (network, adjacent network, local, or physical).
- Attack Complexity (AC): How difficult it is to exploit the vulnerability (low or high).
- Privileges Required (PR): What level of access is needed to exploit the vulnerability (none, low, or high).
- User Interaction (UI): Whether exploiting the vulnerability requires human intervention (none or required).
- Scope (S): Whether the vulnerability affects other systems beyond the vulnerable component (changed or unchanged).
Impact Metrics evaluate the potential consequences of exploiting the vulnerability
- Confidentiality Impact (C): The impact on the confidentiality of data (none, low, or high).
- Integrity Impact (I): The impact on the integrity of data (none, low, or high).
- Availability Impact (A): The impact on the availability of the affected system or data (none, low, or high).
The Base score is calculated from these metrics and is expressed as a number from 0.0 to 10.0, where:
- 0.0–3.9: Low
- 4.0–6.9: Medium
- 7.0–8.9: High
- 9.0–10.0: Critical
2. Temporal Score (Changing Over Time)
The Temporal score adjusts the Base score based on factors that evolve over time, such as:
- Exploit Code Maturity (E): The availability and sophistication of exploit code (unproven, proof-of-concept, functional, or high).
- Remediation Level (RL): How widely patches or mitigations are available (official fix, temporary fix, workaround, unavailable).
- Report Confidence (RC): The degree of confidence in the existence and technical details of the vulnerability (unknown, reasonable, confirmed).
These adjustments refine the Base score, providing a more accurate measure of the vulnerability’s current severity.
3. Environmental Score (Specific to the Organization’s Environment)
The Environmental score tailors the Base and Temporal scores to the specific environment of the affected organization. It takes into account factors like the importance of the affected systems and the presence of mitigating controls.
- Security Requirements (CR, IR, AR): These reflect the importance of confidentiality, integrity, and availability to the organization. Each can be classified as low, medium, or high, depending on the criticality of the system impacted by the vulnerability.
- Modified Base Metrics: Adjustments can be made to Base metrics (e.g., modifying the attack vector or privileges required) based on the actual environment to better reflect the risk.
The Environmental score helps organizations prioritize vulnerabilities in their specific context, as vulnerabilities that might be critical for one organization could be less important for another based on how and where the affected systems are used.
The final CVSS score is a combination of the Base, Temporal, and Environmental metrics. Many organizations use only the Base score for vulnerability prioritization, but the Temporal and Environmental metrics add important context that can better align risk to the organization’s specific needs.
The problem with the Common Vulnerability Scoring System (CVSS)
While CVSS Base scores provide a helpful starting point, they lack the crucial context needed to make informed decisions for individual organizations.
CVSS Base scores rely on generic metrics that are agnostic to the unique environment of any specific organization. These scores assess vulnerabilities based on predefined criteria like the attack vector, complexity, and impact, but do not take into account compensating controls, business context, or real-world evidence.
Without these critical factors, CVSS Base may provide an incomplete or even misleading picture of the actual risk posed by a given vulnerability, resulting in:
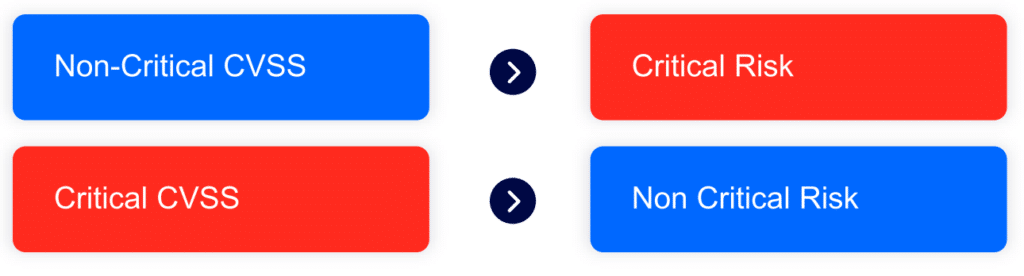
Because of this, security leadership today relies less on CVSS and more on Contextual Data. Analysts export CSV/XML reports and manually compile reports from them. Security data engineers attempt to stream data from the security stack into data aggregators. While these are good solutions on paper, organizations struggle to implement them. They often end up being manual, partial, and expensive. As a result of these implementation issues, these solutions fail to meet the original purpose of reducing the time to mitigation.
The move from traditional vulnerability management to exposure management
Traditional vulnerability management focuses on improving your security posture by identifying and addressing Common Vulnerabilities and Exposures (CVEs), which are industry-recognized weaknesses that attackers might exploit. In contrast, exposure management shifts the perspective to that of the attacker, concentrating on the most critical security gaps specific to your organization’s risk profile.
Exposure management offers a comprehensive view of an organization’s security landscape. By adopting this approach, security resources can be allocated more strategically, with actions prioritized based on the actual risk they pose to the organization. For example, a high-severity vulnerability in a critical system that handles sensitive data would demand immediate attention.
On the other hand, a similar vulnerability in a less essential system, which is well-protected by other security layers, could be deprioritized. Moreover, exposure management goes beyond just identifying vulnerabilities—it also considers other types of exposures, such as misconfigurations and control gaps, to determine which ones pose the greatest risk to the organization.
Cymulate Contextualized Vulnerability Management
Cymulate Exposure Analytics ingests exposure data from various sources, connects between the data points, and analyze the context of each vulnerability. Contextual Data is key for an effective prioritization solution:
- Saves time and resources for the remediation teams
- De-prioritize non-critical vulnerabilities
- Provide data-backed evidence for auditors to justify SLA extensions
- Highlights the priority of truly critical vulnerability and drive effective remediation
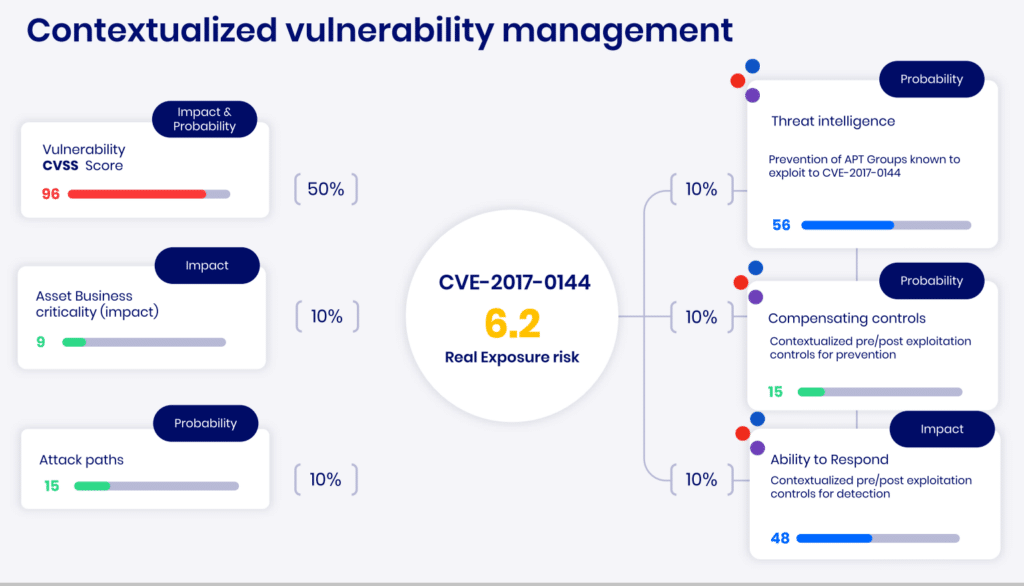
The Cymulate approach focuses on continuous scanning and assessment, mimicking the mindset of an attacker. By simulating real attack paths and scenarios, it uncovers exposures that could lead to potential breaches. Continuous monitoring of the attack surface ensures that emerging threats are addressed in real-time, avoiding the blind spots often left by periodic assessments.
Experience the power of Cymulate firsthand—book a demo today to see how it can help you streamline remediation, prioritize critical vulnerabilities, and stay ahead of emerging threats in real-time.










