This is the final installment of this series. Last week, we looked in-depth into purple teaming non-technological waterfall benefits that, adding to the technological advantages examined two weeks ago, make a convincing case for adopting purple teaming.
Today, we take a closer look at what is required to run efficient purple teaming practices. Before we begin, here are some additional resources that you might find interesting:
- My “Essential Purple Teaming Management” podcast with Tracy Maleeff from InfoSecSherpa as a special guest
- An upcoming live demo of Cymulate’s Advanced Purple Team Framework is scheduled for April 26
Now, without further ado, let’s dive into the most effective and easy way to incorporate purple teaming into your security operations. I am talking, of course, of automating the bulk of the process.
Automating Purple Teaming
Implementing comprehensive automation is a three-pronged process that includes:
Techniques
Find a technology platform with a built-in capacity to cover:
- Continuous and extensive automation with off-the-shelf templates:
– Automation is crucial to enable continuous purple teaming without increasing qualified staff.
– Templates cut down difficult and tedious work, so you can focus on testing and if needed, customized templates for your environment
- A framework to run customized scenarios to test various situations, and establish risk and risk reduction for:
– Remote access over your VPN (for example, your grandson playing Minecraft on your work machine)
– Third-party risk (third party applications in data centers)
– Supply chain
– New application rollout
– Opensource software used for application
- Comprehensive testing:
– Testing across the entire kill chain, your entire environment, and security controls
– External Attack Surface Management (ASM) to detect attackers scanning your environment, the internet, and the darknet for assistance in gaining an initial foothold
– Attack Based Vulnerability Management (ABVM) to detect and assess vulnerabilities’ risk to your specific environment and evaluate the effectiveness of compensating security controls
– Regular phishing campaigns as phishing remains the main initial foothold vector; continuously validating your employees’ alertness through phishing campaigns enables identifying weak links and targeted remedial awareness classes for the right employees
– Running realistic and opportunistic (like a real hacker) tests; tests need to be chained and complete with the ability to try new methods and ways to continue when the attack reaches a dead-end
- Detailed output:
– Visibility into risk through granularly mapping your exposure
– Prescriptive remediation output
– Enable-IT and SOC teams to remediate risks and exposures found
– Translate the results into business risks and how to mitigate them.
Actionable Intelligence
The number one question I get asked by prospects is: “How do we know if we are safe from the latest threat?” Immediate Threat Intelligence automation can help answer that question because it takes into consideration the constantly evolving threat landscape and digital infrastructure. Immediate Threat Intelligence should:
- Include the option to automatically update daily based on the latest IoCs and TTPs because it is impossible to update this manually without considerably increasing the staff
- Accommodate the changes in infrastructure following new deployments
- Be flexible enough to integrate the shift of baselines due to changes in business goals
Usage Accessibility
To accommodate teams of various degrees of maturity, a purple teaming framework should be accessible for:
- Cyber professionals of all cyber-maturity levels:
Beginner
– Provide easy-to-understand explanations
– Ties to MITRE ATT&CK Framework, NIST, etc.
– Basic automation
Expert
– Advanced automation
– Customization
- Executives, leadership, and other SOC/IT roles
This constellation of capabilities is included in he Cymulate Exposure Management and Security Validation platform. The platform has built-in libraries of assessments, scenarios, individual attacks, and deactivated payloads, across a comprehensive array of execution methods, including a dedicated purple teaming framework for savvy users.
Once the baselines are set and the automation is loaded, the Cymulate platform automatically enables you to easily follow trends over time, identify critical exposure, and provide rapid remediation.
How Purple Teaming Enables Baselining and Trending over Time
Continuous purple teaming is what ties together Cybersecurity, IT and DevOps, and business executives—the core elements of the three-legged stool that support a solid security posture, as we delved into last week.
Now it is time to see these three supporting legs interact to provide a clear, understandable, and up-to-date view of the trending security posture, variance from baselines, and the general evolution of security posture management.
The first step to effective purple teaming is establishing baselines that will serve as reference points to monitor and analyze trends. Baselines are defined in collaboration with the board and designed to match the organization’s risk appetite. Ideally, baselines should be established granularly according to priorities.
Once the initial set of baselines is defined, an efficient purple team needs to set up the relevant automation to ensure continuous validation of the parameters underlying the baselines.
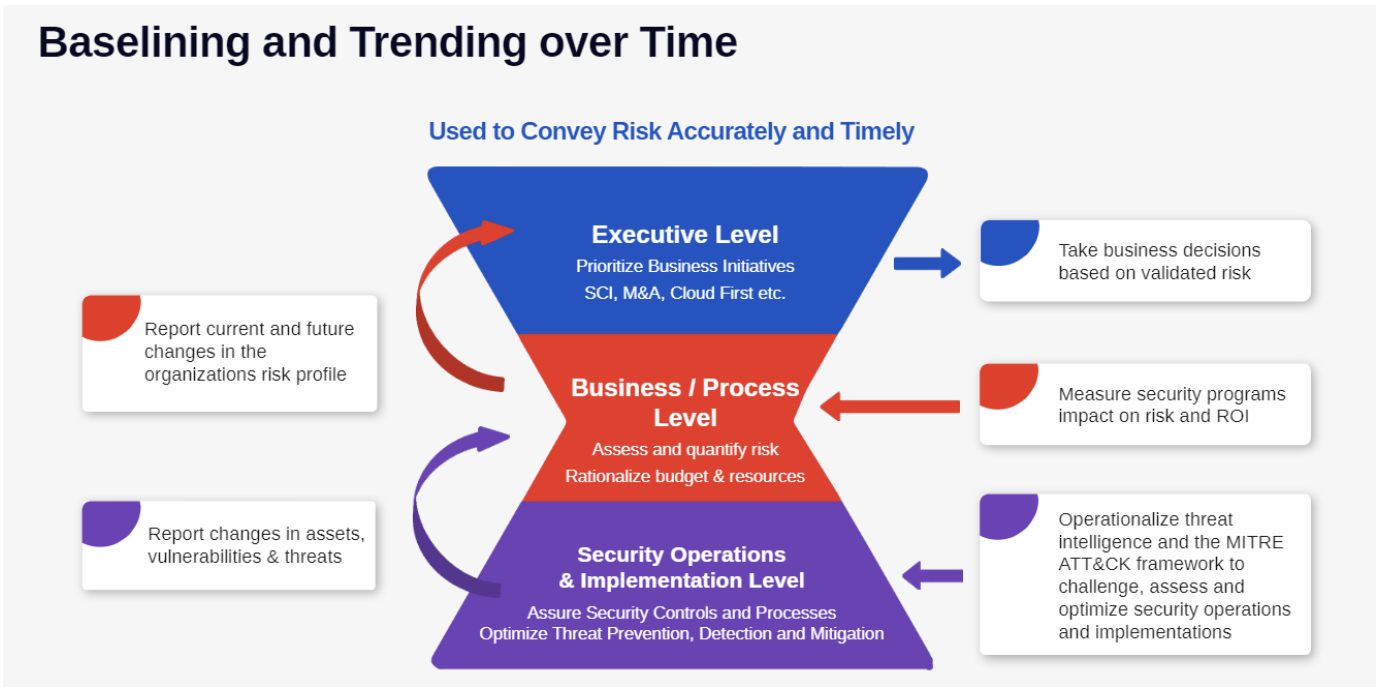
With the help of the graph above, we will examine how purple teaming efficiently is key to integrating cybersecurity into all decision-making levels in a recursive flow. Though a cycle does not have a beginning or an end, we need to start somewhere, and, as the whole idea of purple teaming is to include red teaming in the process, in this case, we will start in the middle of the graph.
- At the security operations and implementation level, the purple team runs comprehensive end-to-end attack scenarios and campaigns to assess security controls configuration effectiveness in compensating for detected CVEs, evaluating the impermeability of segmentation between processes, and optimizing threat prevention and detection, and mitigation.
- The purple team then reports any modification in the risk exposure, whether stemming from changes in assets, the emergence of new vulnerabilities due to internal changes or recently uncovered vulnerabilities in the wild, and resilience to new threats.
- These modifications are correlated with related baselines to measure trending and prevent security drift.
- This information is integrated at the business/process level.
- At the business/process level, this information is leveraged to
a. Assess and quantify the risk in a format designed to transparently inform the executive level with fact-based metrics and without relying on complex technical explanations.
b. Measure the efficacy of the existing security programs and evaluates the solutions continued effectiveness, and take proactive measure to rationalize the tools stack to eliminate overlapping capabilities and re-affect resources to missing ones. - Upon receiving itemized reports about the current state and the foreseeable evolution of the organization’s risk profile, the executive level makes informed decisions and prioritizes business initiatives with minimal risk of endangering the organization.
- The security impact of these new initiatives is automatically evaluated as they are implemented, and the security operation and implementation level produce updated reports that follow the same process, and the cycle starts again.
This continuous cycle enables a clear view of the security posture at any time and prevents security drift.
For more insights into purple teaming, you are warmly invited to listen to my “Essential Purple Teaming Management” podcast with Tracy Maleeff from InfoSecSherpa and to register for the upcoming live demo of Cymulate’s Advanced Purple Team Framework scheduled for April 26.
Essential Purple Teaming Management – Cymulate Cybersecurity Podcast







