PCI DSS recently published the latest version of the PCI DSS standards, version 4.0. This latest version includes many modifications aimed at:
- Adapting security methods to the evolving threats
- Promoting security as a continuous process
- Enabling additional support to payment technology innovation
- Improving verification methods and procedures
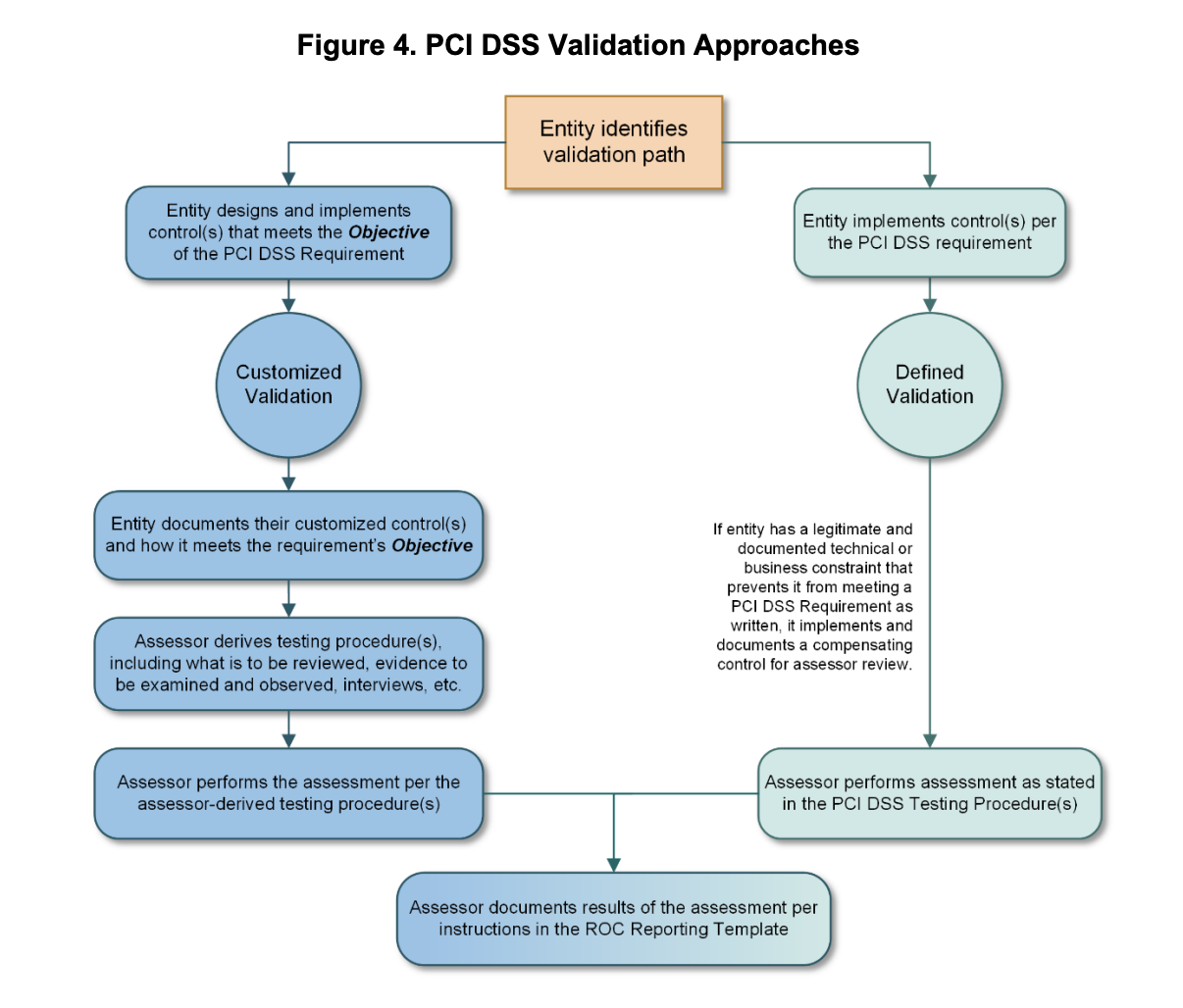
Organizations falling under the PCI DSS scope have until March 2025 to transition from the current 3.2.1 version, but that will be retired in March 2025. In preparation for complying with PCI DSS v4.0, especially the evolving threats and continuous validation and verification methods and procedures aspects, it helps to look around for advanced assessment technologies. This is especially critical for this recent version as v4.0 includes a new “Customized Validation” path in addition to the traditional “Defined Validation” one. For any organization that targets hardening its security posture rather than simply achieving compliance, this added option opens a lot of avenues.
As opposed to the “Defined Validation” path that follows the “letter of the Law,” so to speak, the “Customized Validation” path requires the creation and implementation of controls meeting the objective of PCI DSS requirements.
This provides organizations with far larger freedom of movement. It opens the opportunity to kill two birds with one stone: Focusing on hardening your security posture and meeting PCI regulators’ requirements.
Intended for risk-mature entities that demonstrate a robust risk-management approach to security, including, but not limited to, a dedicated risk management department or an organization-wide risk management approach, this customized validation path’s key factor is the design and implementation of controls meeting the objectives of the PCI DSS requirements.
How to implement PCI DSS v4.0
For the qualifying requirements, implementing a PCI DSS v4.0 customized approach requires:
- Documenting and maintaining evidence about each customized control.
- Performing and documenting a targeted risk analysis for each customized security control.
- Perform testing of each customized control to prove effectiveness, document testing performed, methods used, what was tested, when testing was performed, and results of testing in the controls matrix.
- Monitor and maintain evidence about the effectiveness of each customized control.
- Provide completed controls matrix(es), targeted risk analysis, testing evidence, and evidence of customized control effectiveness.
This greater flexibility afforded to organizations requires them to:
- Demonstrate that the innovative security practices they integrated do meet the requirements.
- Validate that their security controls configurations meet PCI DSS v4.0’s most stringent requirements.
Effortless PCI DSS v4.0 Compliance with Cymulate: Streamlined Security Validation and Documentation
For organizations that integrated advanced continuous security validation technologies such as those used together in Cymulate Exposure Management and Security Validation platform, this is extremely easy. Both performing and documenting the requirements of points 1. to 4. are automatically generated. When looking at point 5., the only element that might need a little bit of additional work is the targeted risk analysis, which might require creating a specific custom dashboard. That can easily be achieved with Cymulate’s customizable dynamic dashboards.
For organizations that adopted security controls management methods that differ from those matching the PCI DSS v4.0 defined validation specification, integrating their SIEM and SOAR with the Cymulate Exposure Management and Security Validation platform by default answers all the assessment and documentation requirements to qualify for the customized validation option.
Optimize Security and Ensure Compliance with Cymulate’s Advanced Validation Technologies
The Cymulate Exposure Management and Security Validation platform provides modular access to a range of advanced assessment and security validation technologies, including:
- Attack Surface Manager (ASM) – that emulates attackers’ performing reconnaissance to discover exposed assets.
- Breach & Attack Simulation (BAS) – that simulates thousands of attack scenarios and correlates them to security controls detection and response data collected through API integrations, and, in addition, provides actionable mitigation guidance.
- Advanced Purple Teaming Framework – that enables security teams to create complex scenarios from pre-built resources and custom binaries and executions without any limits or restrictions. Those scenarios can be used to exercise incident response playbooks and proactive threat hunting or automate security assurance procedures and health checks. The framework launches attacks and correlates them to security controls findings through API integrations, in addition to providing actionable detection and mitigation guidance.
- Red Teaming campaigns – that attempt to penetrate the organization by analyzing the external attack surface, discovering vulnerabilities, and autonomously deploying attack techniques that penetrate and gain an initial foothold within the network and then attempt to propagate within the network in search of critical information or assets.
- Advanced Vulnerability Prioritization Technology – Attack Based Vulnerability Management that drastically reduces the number of critical vulnerability patches required by checking which vulnerabilities are effectively compensated for by security controls
The Cymulate platform validates email, web, web application, endpoint, and DLP security controls either individually or by simulating the flow of an APT across the full attack kill chain. The platform is updated daily with new threats, attacks, and adversarial tactics and techniques to validate the current effectiveness of your security controls against emerging threats.
These capabilities are far more comprehensive than the most stringent PCI DSS v4.0 customized validation requirements, ensuring compliance, and, as a bonus, or, actually, as a primary function, provide you with continued optimization of your security posture.










