AMPLIFY is the new expert-led security assurance program that combines the advanced capabilities of the Cymulate Exposure Management and Security Validation platform with the assistance of an advisor.
I am proud to lead the effort that gave rise to AMPLIFY. Our professional security advisors build, operate, and maintain your security validation framework and report on your security posture, leveraging the world-class Cymulate XSPM platform and the Cymulate Security Assurance process.
This framework is a repeatable program that can be implemented by any size organization.
Born Out of Necessity
AMPLIFY was born out of the necessity for clients to operationalize security posture data and build a repeatable program that produces measurable, sustainable results and increases security effectiveness while reducing risk. After spending considerable time talking to CISOs across many verticals, the need for such a framework became abundantly clear.
Drawing on the wealth of data gathered, we combined this information with our deep industry knowledge and crafted a program that addresses this emerging need based on the top key suggestions for a Security Optimization program:
- The program must be easy to digest and consume.
- The program must support Full Kill Chain capabilities
- The program must be based on evidence and score risk
- The output must provide mitigation guidance
- The program must monitor for security regression.
AMPLIFY also addresses numerous other crucial areas of concern:
Trending over time – Ensuring that your security posture trends in the right direction is critical to achieving the expected outcome. After obtaining positive security improvements, you do not want to regress. Just about every security workshop we engage with raises this issue. “Am I still protected against that attack? Am I better off than I was last quarter, this time last year?”
How change affects posture – Teams want to understand how one change in the environment might affect downstream capabilities and overall security posture. There is no effective way today to capture this information quantifiably. “If I make a change to my environment to support the business, how does that affect my security posture?” is a recurring question.
Vulnerability optimization – Organizations need to quickly and dynamically understand how they may be affected by immediate threats like LOG4J. “Do I have this vulnerability, and is it part of an attack path?” Vulnerability Prioritization Technology (VPT) is of high importance to combat the patching problems experienced today.
Attack Surface – There is a need to uncover digital assets, shadow IT, leaked credentials, and intelligence that can be used against the organization. This information needs to be seamlessly fed to an automated system for analysis and mitigation. “Do I have this particular vulnerability, and do my compensating controls mitigate this threat?” is a question that should never be left unanswered.
Reporting – CISOs struggle to communicate cyber effectiveness to the board. Dynamic risk-based reporting based on empiric metrics is needed to produce meaningful conversations. It answers the question: “How can I better communicate cyber effectiveness and consistently report?”
Cybersecurity attacks and resulting damage are increasingly making headlines. The likelihood that every organization will face attacks is almost assured. Agile development and cloud migration are contributing to expanding attack surfaces. Many believe that a threat-informed security posture is impossible to achieve due to limited resources and staff.
Yet, Cymulate leading Full Kill Chain assessment capabilities give you the power to gather security posture evidence, and the AMPLIFY program provides you with the experts. Dynamic reporting gives you the ability to extract what is mission-critical, provides you with environment-specific immediate threat exposure reports, and a full kill-chain exposure report to present to the board.
What our clients have asked for, we have delivered! With Cymulate + AMPLIFY, our experts help your experts effectively build and run an Extended Security Posture Management program.
Why AMPLIFY?
With AMPLIFY, you benefit from a dedicated advisor to assist in implementing, running, and analyzing the Cymulate Exposure Management and Security Validation platform. From day one, you’ll be able to challenge, validate, and manage your cybersecurity posture end-to-end. Your defense will be mapped across the entire MITRE ATT&CK® framework for ultimate optimization.
Weekly, monthly, and quarterly cadence sessions with your Cymulate advisor will enable you to:
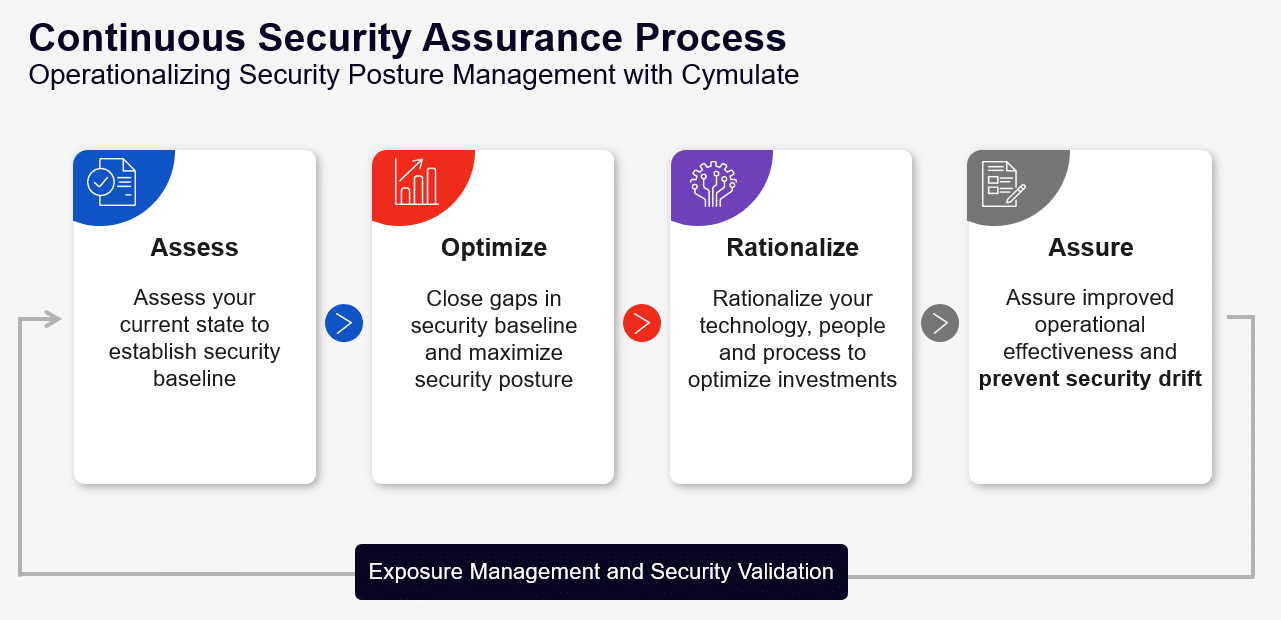
- Assess your current state and establish a security baseline
- Evaluate and quantify your security resilience
- Remove security blind spots and gaps Rationalizing your technology, people, and process to cut overlap and increase efficiency
- Leverage existing security skills with zero added coding
- Improve operational effectiveness and prevent security drift
- Prioritizing mitigations based on your specific environment
- Accelerate recovery when attacked
- Monitor for Security Drift
By constantly proactively monitoring your environment, you have the ability, likely for the first time, to leverage evidence of cyber hygiene issues, make immediate adjustments, retest, and optimize your security posture. This programmatic approach allows you to predictably reduce risk over time and report with confidence.
What Organization is Right for AMPLIFY?
Organizations of all sizes are leveraging AMPLIFY. Whether you are a small retailer with limited resources needing extended visibility into your security posture, or a large organization building a dedicated program for security optimization, Cymulate AMPLIFY will supercharge your effort into continuous security validation.
Limited resources are no longer a barrier to accessing the Cymulate platform and building a repeatable program. Our experts follow our Security Assurance Process to ensure you maximize your investment and reap the benefits of becoming more mature while reducing risk.
SecOps teams, red teams, blue teams, GRC teams, SOC teams, all benefit from quantifiable evidence of the current security posture. Such invaluable data provide a clear path forward to optimization and reporting on cyber effectiveness.
CISOs can accurately report on security posture relative to spending and risk and calculate cybersecurity solutions’ array ROI. Removing ambiguity from the decision-making process allows room for evidence-based decisions, which leads to a more effective organization.
We would love the opportunity to discuss how AMPLIFY can help improve your security posture and deliver world-class results.








