How security leaders can quantify risk and respond with confidence.
For any cybersecurity leaders who have ever had to sit in front of their executive committee or members of their board and answer the question: “Are We Secure?”, they know the answer to that question is not that simple.
When it comes to cybersecurity, “Are we secure?” is not a binary yes or no answer.
There is no such thing as “Yes, we are 100% secure from cyber attacks”. So, by default, the answer can only be “no”. But no, is not an answer any executive leader or board member wants to hear.
So, the real question that needs to be asked here is: “How exposed are we?”.
Measuring Cyber Risk Exposure
Answering the question of cyber risk exposure does not happen on a simple Yes or No scale. Here at Cymulate, we measure an organization’s overall risk on a scale from 0 – 100 to provide an accurate reflection of their current security posture.
Now, when an executive asks: “How exposed are we?”
You can confidently answer with:
- We have minimal risk and exposure to cyber-attacks.
- We have a low risk of being breached by a cyber attack.
- Well, we do have medium risk and need to make some changes to avoid becoming the next breach victim.
- Sorry to inform you, but we currently are at high risk of a cyber breach and need to make some immediate investments to better protect our business.
As you look your executives in the eye and answer the question with conviction, you will need real concrete evidence and belief that your security program is effective, and that your organization has an “acceptable level of cyber risk” given your business context.
So, what is considered “acceptable” when it comes to cyber risk exposure.
Since 2016, more than 500 enterprises have turned to Cymulate for an easy-to-deploy, SaaS-based platform for continuous security and exposure validation of their cybersecurity controls. The platform assesses security controls and immediate threats by running a comprehensive suite of attack simulations. The output of these assessments quantifies the organization’s exposure level and provides the evidence required to go to the board with confidence and justify the need for further investments to improve security controls and mitigate risk.
“With Cymulate, we can present quantifiable data to the board and show a direct correlation between investments and the reduction in risk.” said Avinash Dharmadhikari, CISO, Persistent Systems (view full case study).
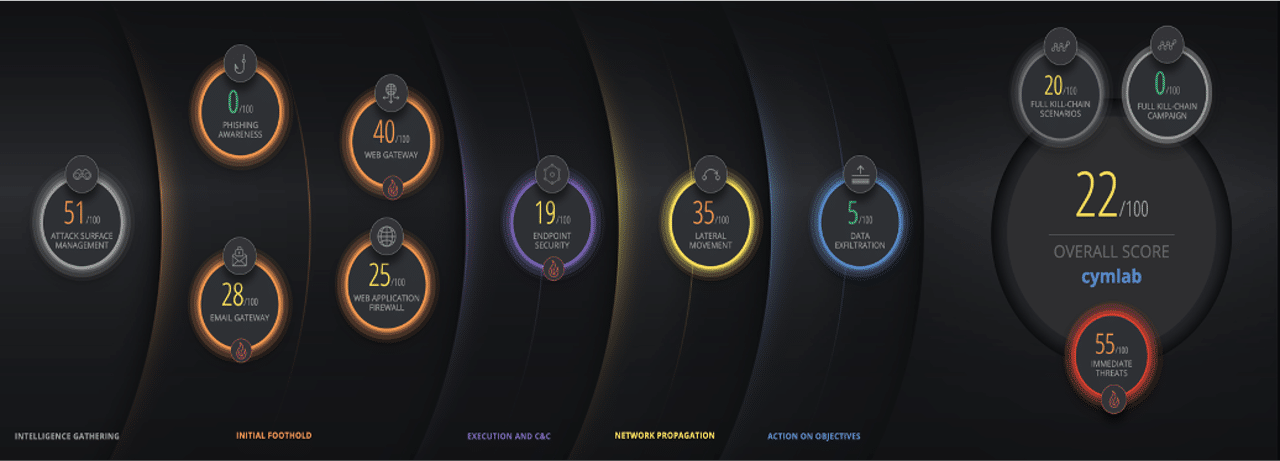
Cymulate customers can track their results and quantify the exposure level using their overall score and the scores for the individual security controls as shown in the example dashboard above.
“The best thing is that within 24 hours, Cymulate enabled us to check our security systems and report the results to our CEO.” said Haim Inger, CTO, Clal.
Achieving an Acceptable Level of Risk
Based on an analysis of scores across the Cymulate platform, we recognize that organizations that achieve an overall score of 33 or less typically have an acceptable level of cyber risk. Of course, this can vary from organization to organization depending on their business context and the nature of the information they are trying to protect, but in general minimal risk to low risk is considered acceptable risk and scores in that range (0 – 33) are what organizations aspire to achieve and maintain.
For those organizations that fall into the medium risk to high risk category (34 – 100), they have work to do to reduce their risk and bring their score down over time to a level they would regard as “acceptable”.
Providing Concrete Evidence of the Need for More Cyber Investments
Once you have quantified the level of risk exposure to executives, their next likely question is: “How do we know?”.
By running frequent automated attack simulations against your security controls, you will always be armed with the latest results as proof and evidence as shown in the executive summary example below.
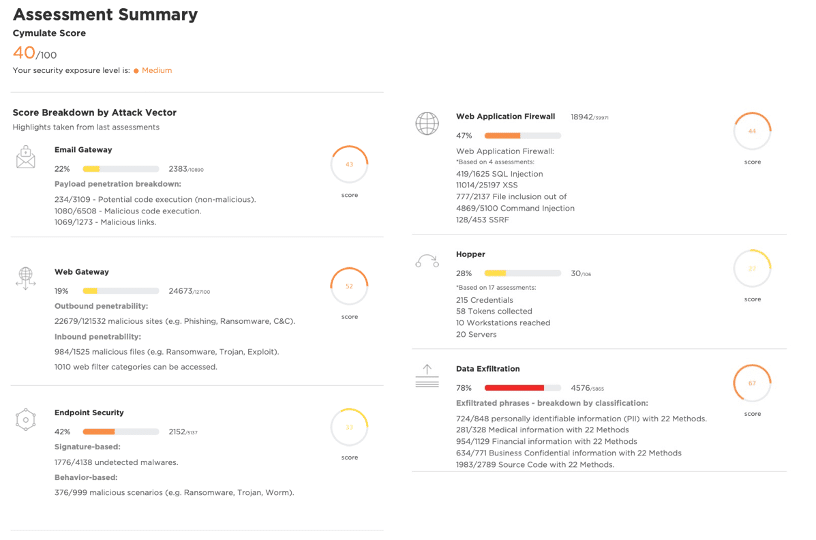
The results of these offensive security tests validate your security controls and highlight areas of concern and exposure that need to be addressed to get to an acceptable level of risk. The executive summary clearly shows the current security posture of your controls and the areas of weakness that require improvement.
In addition to the assessment summary, you will also be armed with a prioritized mitigation plan created to reduce your security exposure level and get you better protected, faster.
Cyber Security is a Game of Continuous Improvement
Regardless of your score, we know that cyber security is a game of continuous improvement that starts with a baseline score of where you are today and continues to make improvements over time to enhance your security posture and ultimately reduce your risk profile as measured by your Cymulate score.
And even when you do get down to an acceptable level of risk, you still need continuous validation (daily assessments of immediate threats and weekly assessments of security controls) to avoid experiencing drift resulting from the constant changes to your IT environment and the ever-evolving threat landscape and new tactics by threat actors.
Organizations are always going to have vulnerabilities (and most will have lots of them) due to the dynamic nature of the IT environment and the latest tactics and techniques being used by threat actors to exploit those vulnerabilities.
Security and Exposure Validation Improves Your Security Posture
Conducting pen tests or red team exercises on an annual or even semi-annual basis is no longer sufficient to keep pace with the speed at which adversaries operate these days.
You need continuous security and exposure validation against immediate threats that are discovered on a daily basis and changes that are made to your security controls every week.
Cymulate has established the following security validation best practices to validate security controls, immediate threats, and operational responses.
| Validate Controls | Validate Threats | Validate Response |
|---|---|---|
| Email Gateways | Immediate Threats | SOC Exercises |
| Web Gateways | Lateral Movement | Purple Teaming |
| Web Application Firewalls | Full Kill-Chain Attacks | |
| Endpoint Security | ||
| Cloud Security | ||
| Data Loss Prevention | ||
| SIEM Observability |
The Cymulate platform enables continuous validation and improvement across your cybersecurity program so you can:
- Continuously measure and convey cyber effectiveness and risks to your leadership
- Validate controls, discover security drift, and understand your emergent threat risk
- Prioritize your vulnerabilities and understand exposures mapped to your preferred security frameworks (MITRE ATT&CK, NIST)
- Rationalize cyber security spend and manage your costs.
So, the next time you are scheduled to meet with your executive committee or members of the board to answer questions about the level of cybersecurity exposure of your organization, answer with confidence (and evidence) with the Cymulate platform.
Don’t wait, schedule your demo today.
Related Resources:











