Essential Components of a Security Validation Solution
Breach and Attack Simulation (BAS) tools only provide a partial picture of your security posture. End-to-end security validation requires an offensive approach that utilizes continuous assessments to answer these key business questions:
External Attack Surface Management
What digital assets are exposed to an attacker?
Attack Path Mapping
How can an attacker get to my crown jewels?
Security Controls Validation
How well are my security controls performing?
Management and Prioritization
How well are my security controls performing?
Check Your Security Posture
Get Actionable Insights
Take a more holistic approach with Cymulate's Extended Security Posture Management (XSPM) platform.
- Lightweight agent, running on a single machine
- Safely perform attack simulations in your
environment - Allows you to choose which attack vectors you
wish to simulate - It takes only a few minutes to set up
- Provides immediately actionable insights on your security posture
Free 14-Day Trial
Please use your company email address, free email providers (such as Gmail and Outlook) will not be accepted.
Why the Cymulate Holistic Solution is Better
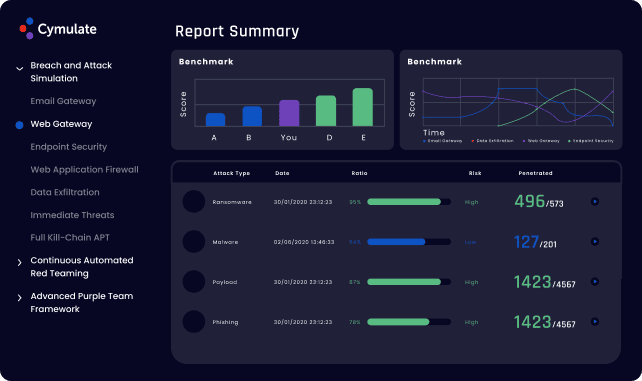
Combines outside-in reconnaissance, security awareness, infrastructure resilience, and security control validation in one platform to provide complete visibility of your security posture.
Combines outside-in reconnaissance, security awareness, infrastructure resilience, and security control validation in one platform to provide complete visibility of your security posture.
Combines outside-in reconnaissance, security awareness, infrastructure resilience
Combines outside-in reconnaissance, security awareness, infrastructure resilience
Combines outside-in reconnaissance, security awareness, infrastructure resilience
Extended Security Posture Management Benefits

Optimize Cybersecurity Effectiveness

Measure the effectiveness of security solutions, processes, and staff workloads, to fine-tune your security spending to align with company priorities.

Minimize Risk Exposure

Discover your external attack surface, map your attack paths, validate your security controls, and prioritize your mitigation efforts.

Measure, Track and Communicate

Measure your current level of cyber risk to draw a baseline and monitor continued success to communicate progress to executive leadership.

Validate Compliance Requirements

Continuously test and ensure that different controls and measures are in place.

Prioritize Vulnerabilities

Integrates with leading third-party vulnerability management solutions to provide context and accurately prioritize remediation, patching, or reconfiguration of compensating controls.









