Exposure Prioritization and Remediation
Focus on the exploitable by integrating automated validation with exposure discovery.
Validate First, Fix What Attackers Can Actually Exploit
Cymulate Exposure Management tests your defenses against real-world exploits and scores your vulnerabilities to prioritize remediation based on what attackers are most likely to breach.
Integrate Discovery
Aggregate exposures and assets with intelligent connectors.


Validate Exposure
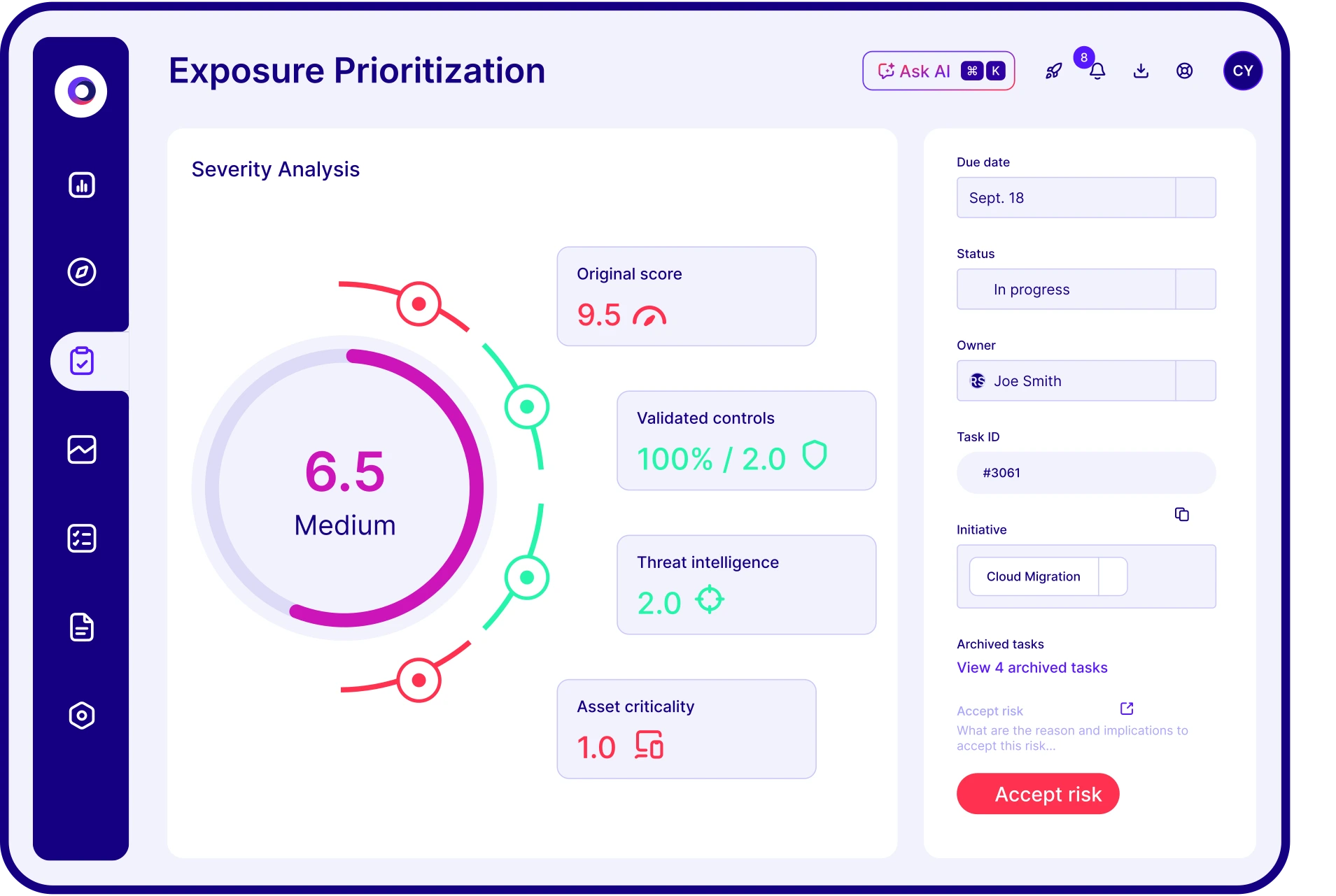
Score exposure context of proven threat prevention and detection


Prioritize Remediation
Prioritize validated exposures with remediation guidance.


Exposure Prioritization Benefits and Outcomes
Cymulate drives full-context continuous threat exposure management (CTEM). By aggregating exposures and assets and automating threat validation, Cymulate provides the source of truth for SecOps, red teams and vulnerability management to focus on validated exposures with the biggest potential business impact.
52%
Less critical exposures
Prioritize exposures based on exploitability with proof of threat resilience and effective mitigation.
60%
More efficient prioritization
Enable automation and improve workflows with intelligent, evidence-based risk insights.
Escalate
High-risk, low-severity
Elevate low and medium exposures that are exploitable and impact critical assets.
Put the “T”
In CTEM
Make threat validation a continuous process with collaboration across security teams.
Aggregate Data on Your Exposures and Affected Assets
Cymulate Exposure Management consolidates exposure findings by integrating with vulnerability scanners and other exposure discovery tools. Cymulate correlates those exposures with Cymulate Exposure Validation attack simulation findings for proof of threat prevention and detection.
What our customers say about us
Organizations across all industries choose Cymulate to prioritize and mobilize remediation efforts where they matter most.
Exposure Prioritization and Remediation FAQs
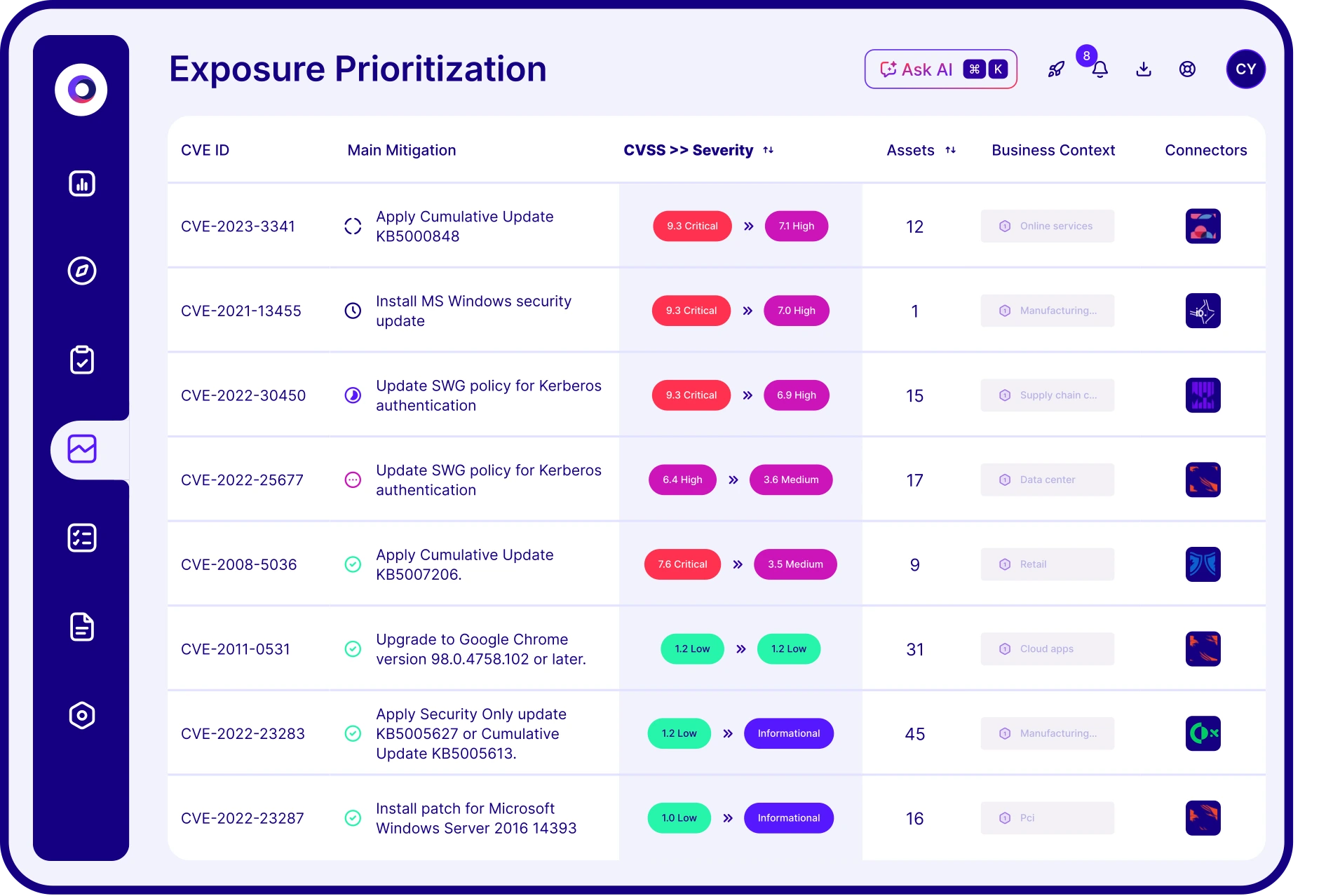
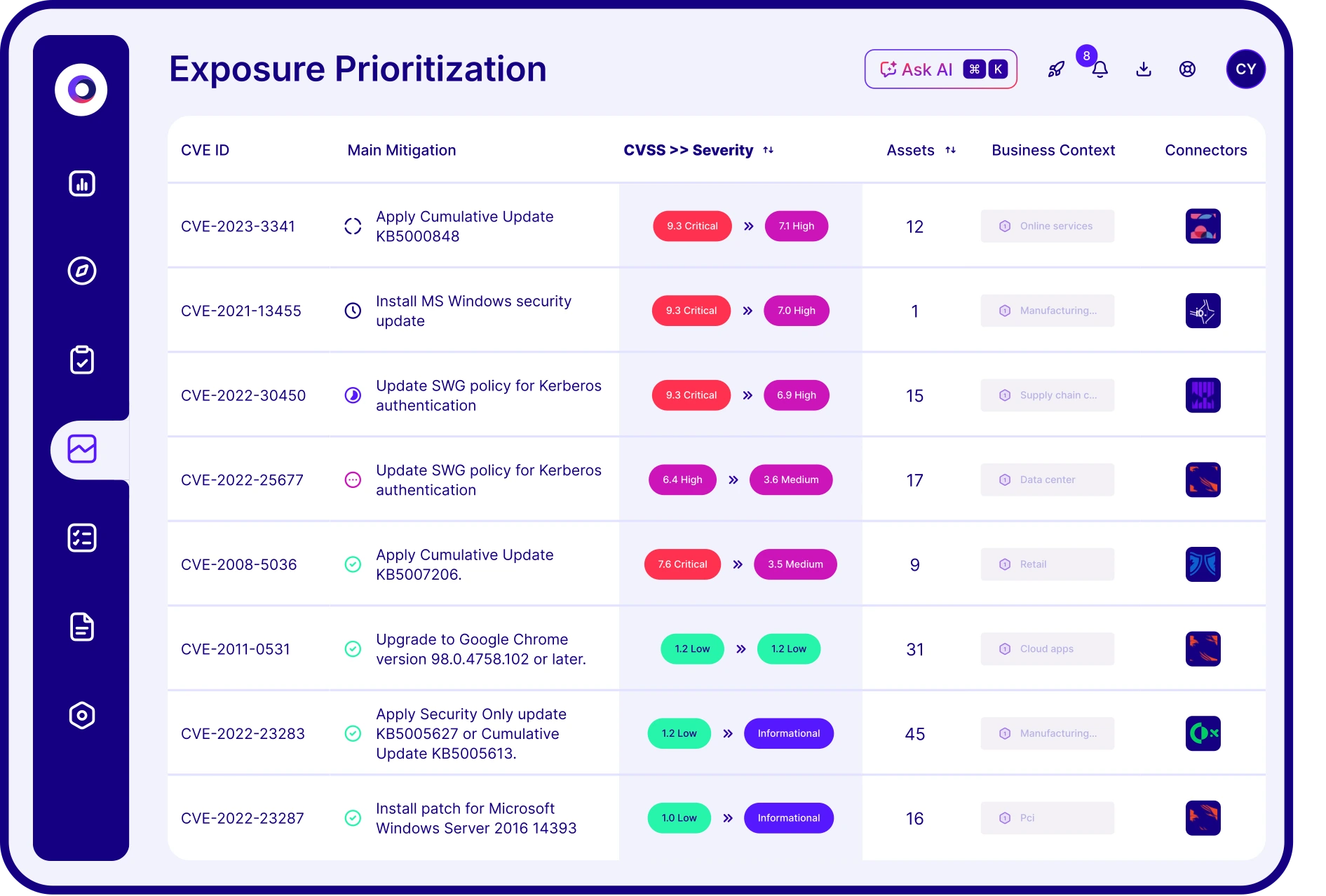
Threat exposure prioritization is the process of identifying and ranking vulnerabilities and other security weaknesses based on their actual exploitability and impact on business-critical assets. Cymulate uses automated threat validation and exposure scoring to help teams focus on exposures that that are not protected by security controls.
Cymulate performs automated attack simulations that test real-world exploitability of identified exposures. It correlates data from vulnerability scanners with threat prevention and detection outcomes to provide proof of resilience against specific threats.
CTEM (Continuous Threat Exposure Management) is a strategic approach that continuously discovers, validates, and remediates exposures. Cymulate puts the “T” in CTEM by integrating threat validation across security operations, red teams and vulnerability management.
CVSS scores indicate severity, but not exploitability. Cymulate helps security teams move beyond static scoring by validating which exposures are actively exploitable — enabling more effective and efficient remediation.
Cymulate customers have seen a 52% reduction in critical exposures by focusing remediation on exposures with proof of exploitability and effective mitigation strategies.
Yes. Cymulate integrates with vulnerability scanners, IT asset management and other security tools to aggregate exposures, validate them through simulation and provide a unified risk-based prioritization view.