Purple Teaming
Purple teaming is more than just collaboration between red and blue teams - it’s a strategic approach that strengthens defenses, speeds up response, and aligns security with business priorities. By integrating offensive and defensive insights, organizations gain measurable improvements across multiple areas:
- Continuous Security with Cymulate: Cymulate’s Breach and Attack Simulation platform enables automated purple teaming, providing real-time threat intelligence, customizable attack scenarios, and actionable remediation insights.
- Bridges the Gap Between Red and Blue Teams: Purple teaming eliminates silos by fostering real-time collaboration, ensuring that attack simulations directly inform defensive improvements.
- Accelerates Remediation: By combining offensive context with defensive insights, mitigation steps are clearer and faster, reducing the time between identifying vulnerabilities and fixing them.
- Maximizes Security Tools’ Value: Joint validation highlights misconfigurations, underused tools, and redundancies, helping organizations rationalize and optimize their security stack.
- Strengthens Communication Across Stakeholders: Purple teaming aligns cybersecurity, IT, DevOps, and executives with shared goals, improving decision-making and reducing conflicting priorities.
What is a Purple Team in cybersecurity?
A purple team in cybersecurity brings together red and blue teams to combine their offensive and defensive testing skills. When blue and red teams work separately, each team focuses on its specific area of expertise:
- Red teams simulate attacks to uncover weaknesses, exploitable vulnerabilities, and other security gaps in their organizations’ security posture.
- Blue teams scan the infrastructure for weaknesses, vulnerabilities, and other security gaps, mitigate them, and monitor the infrastructure to detect and stop attempted attacks.
When working separately, red teams are often perceived by blue teams as finding all the flaws without effectively educating and prescriptively providing feedback on how to fix and remediate them. On the flip side, red teams typically lack a comprehensive understanding of the infrastructure, and their security validation process might lack depth and thoroughness.
Purple teaming combines the capabilities and knowledge of both blue and red teams. This collaboration leads to stronger, more adaptive defenses, quicker attack detection, and better-prepared security teams.
The main goals and benefits of purple teaming
At first glance, purple teaming may seem only to impact how red and blue teams work together. In reality, it affects four key groups: cybersecurity, IT, DevOps, and business executives. While all teams aim to advance the organization's security posture, their priorities often conflict. This conflict arises because each team operates with different goals, responsibilities, and pressures:
- Cybersecurity: Focuses on closing security gaps and balancing risk with operational needs to prevent breaches.
- IT: Caught between securing endpoints, employee demands, and DevOps' need for flexibility, often facing conflicting priorities.
- DevOps: Prioritizes fast software deployment and resents security measures that slow down their progress, facing pressure from executives.
- Business Executives: Aim for smooth, uninterrupted operations, mediating between cybersecurity, IT, and DevOps, with limited technical expertise.
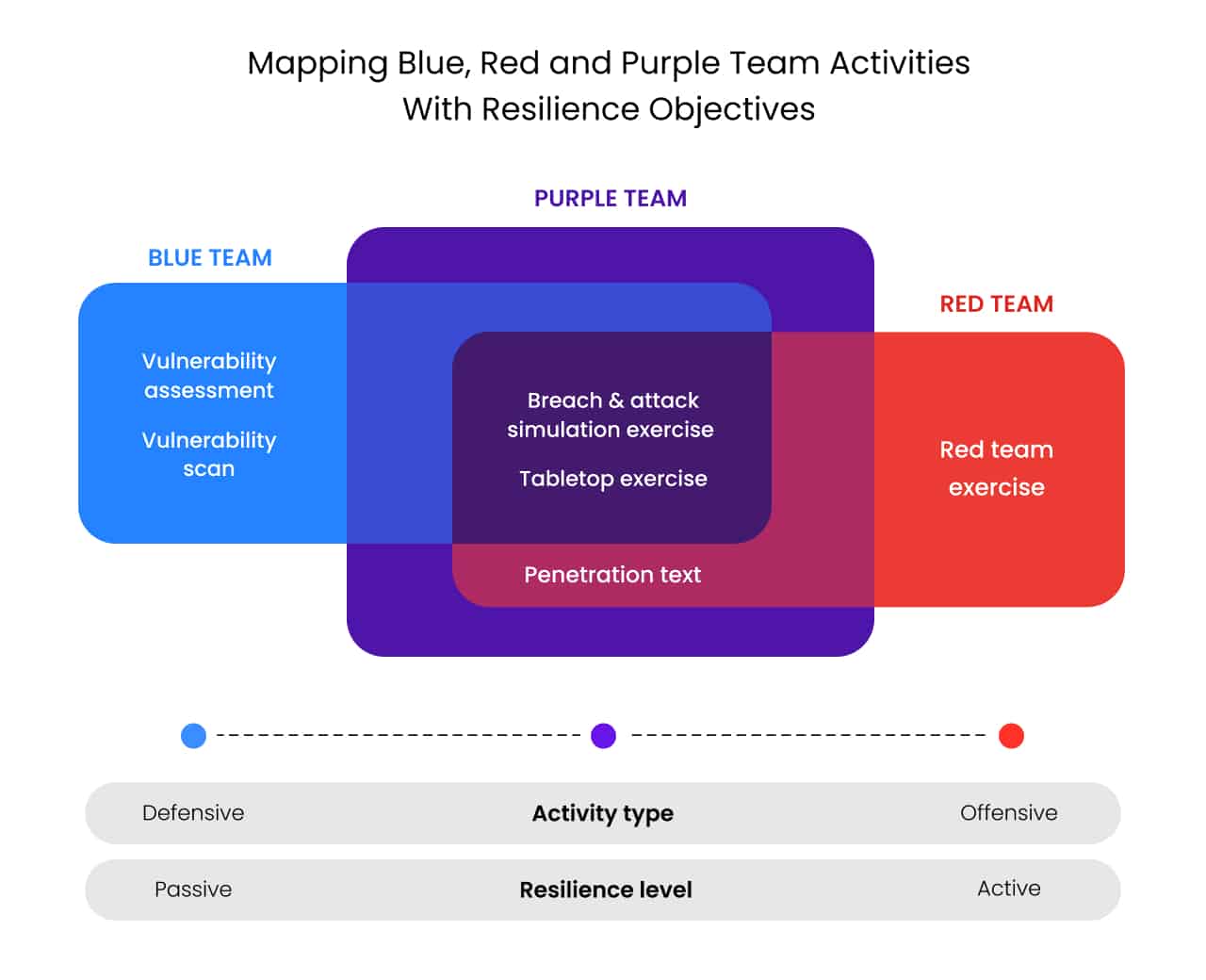
To harmonize those conflicting goals, the first step is to define common ground and shared goals that consider the needs of all stakeholders. Purple teaming combines defense and attack strategies to validate risk assessments, helping set clear security priorities for the entire organization. This includes simplifying the process of patching vulnerabilities, which eases the workload for the IT team. Communication between cybersecurity, IT, and executives becomes smoother with shared and clearly defined goals.
Key Advantages
Detailing the effect of purple teaming on each group gives a more in-depth understanding of purple teaming’s full impact:
1. Increased Efficiency
With segregated blue and red teams, the sequential nature of information flow slows down the mitigation process. The red team identifies and lists securities gaps and sends the list to the blue team. The blue team then needs to:
- Contextualize each gap
- Understand the rationale explaining why each gap creates a security risk
- Define the appropriate mitigation process required
- Forward to other teams for implementation
With purple teaming, the process is considerably shorter as the red team conveys both the context and the rationale, often shortening the mitigation process creation. This leaves only two steps instead of four.
2. Optimized tools
Combining adversarial and defensive perspectives enables a far better documented understanding of the efficacy of the SOC tool stack. When solutions are bought based on vendors’ descriptions and minimally configured, it often results in a tool sprawl with underutilized resources and unintelligible data. Purple teaming identifies ill-configured, under-used, ineffective, missing, or overlapping solutions.
3. Enhanced efficacy
Rationalizing and reconfiguring the defensive tool stack based on the information gathered through purple teaming directly increases cybersecurity solutions ROI and reduces the number of false alerts and the risk of alert fatigue. It streamlines analysts' data flow, thus improving their output accuracy and timeliness.
4. Improved internal communication and collaboration
Measuring security infrastructure resilience based on its ability to withstand comprehensive attacks generates accurate metrics and definitive answers to specific questions that replace prior guesstimates based on adherence to best practices.
This provides a new level of visibility into risk exposure that facilitates communication between the executive and technical departments and cements collaboration. It also eliminates the antagonism between blue and red teams, replacing it with a single team with better-combined knowledge and skill set.
Purple teaming focuses on hardening an organization’s security posture far beyond the basic requirement of checking boxes for compliance purposes. At its core, purple teaming combines a blue team's traditional reactive defensive methods with the insights gained from proactive offensive validation techniques typically used by penetration testers and red teams. The resulting assessments are far more thorough, and the blue and red team collaboration from the start promotes a smooth implementation of the uncovered required mitigations.
When run in tandem with continuous security validation techniques, purple teaming integrated with day-to-day IT and DevOps deployments acts as an enabler by accelerating business goals while simultaneously reducing risk
Purple Team Exercises
Purple team exercises are structured simulations that bring together red and blue teams to test and improve an organization's security posture collaboratively. These exercises simulate real-world attack scenarios to evaluate how well security systems protect against threats and how quickly vulnerabilities can be identified and resolved.
- Customized Attack Scenarios: Rather than relying on generic attacks, purple team exercises focus on customizing attack scenarios that reflect the organization's specific threat landscape and vulnerabilities. These tailored exercises enable the team to practice against threats they are most likely to encounter, ensuring the results are relevant and actionable.
- Real-Time Collaboration: During these exercises, the red and blue teams work together in real-time, unlike traditional isolated simulations. The red team performs attacks, while the blue team responds, and both share immediate feedback. This collaborative approach improves incident response times and enhances the learning process for both sides, leading to faster and more effective mitigation of vulnerabilities.
- Continuous Learning: Purple team exercises are not one-time events. They create a continuous learning loop, where lessons from each exercise are used to refine future strategies. This cycle of constant improvement helps to ensure that the organization is always one step ahead of emerging threats. It also fosters ongoing collaboration between security teams and other departments like IT and DevOps.
- Improved Decision-Making: Purple teaming also benefits decision-makers by providing clear, actionable insights into the organization’s risk exposure and security resilience. Executives can make informed decisions about security investments, resource allocation, and risk management with detailed reports and real-time data.
Building a Culture of Collaboration The ultimate goal of purple teaming exercises is to build a culture of collaboration across the entire organization. By breaking down the silos between security, IT, DevOps, and executives, these exercises promote better communication, stronger teamwork, and a shared commitment to strengthening cybersecurity while supporting business objectives.
Automated Purple Teaming with Cymulate
The most effective way to enable continuous purple teaming without adding significant resources is by automating essential parts of the process. This requires tools that automate tasks and provide accurate, actionable data to help analysts make faster decisions and accelerate remediation.
An automated purple teaming framework should include the following:
- Ready-to-use templates for common attack scenarios to allow teams to run tests and make adjustments as needed quickly.
- Scenario creation wizard to build new, customized attack campaigns using a wide range of attack methods without coding each element.
- Daily updates for the latest threat intelligence, ensuring tests and simulations reflect current threats.
- Comprehensive testing options with agent-based and outside-in attacks that mimic real-world scenarios.
Cymulate Breach and Attack Simulation (BAS) offers all these features, making it easier for teams at any skill level to automate purple teaming and improve their security posture. This approach reduces manual workload, enhances threat detection, and provides clear, actionable insights for remediation.
With its easy deployment, real-time threat intelligence, and detailed reporting capabilities, Cymulate enables red and blue teams to work collaboratively, automating the purple team function. The platform provides comprehensive coverage and customization options, allowing continuous security validation.
This proactive approach helps organizations enhance their resilience by automating threat detection, mitigation, and risk assessment. It creates a unified and automated purple team environment that drives faster, more effective security outcomes.

