Prove the Threat.
Improve Resilience.
Automated validation to optimize threat resilience with actionable mitigation.
Cyber risk is business risk. Is your security ecosystem ready for the next threat?
Board of directors view cybersecurity as a business risk
Source: Gartner
Enterprises report losing existing customers after a breach
Source: Cyber Magazine
Days to recover from a
cyber incident for most organizations
Source: Cohesity
Threat validation reveals your resilience in real time — and how to optimize controls to improve.
You already invest in expensive security controls. Shouldn't you make sure they're set to defend? We make offensive security simple and continuous. With Cymulate, you can easily test critical defenses against the latest threats with automation and AI, identify exploitable gaps and harden resilience with automated mitigation that improves the threat prevention and detection of your existing security controls.
Validate threats
Optimize defenses
Measure resilience
Solution Results
30%
Increase in threat prevention
AVG. of CYMULATE CUSTOMERS
97%
Increase in threat detection
AVG. of CYMULATE CUSTOMERS
60%
Increase in SecOps efficiency
FINANCE CUSTOMER
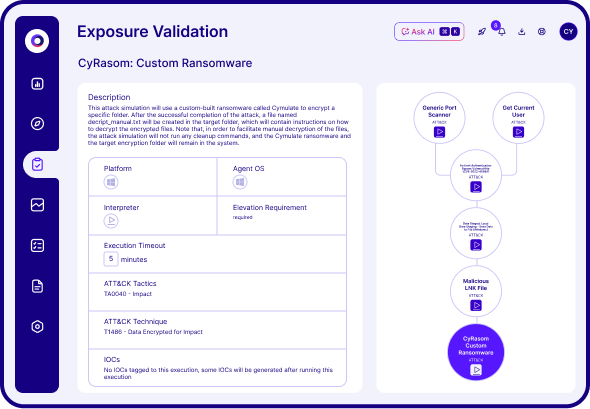
Threat Validation and Control Optimization
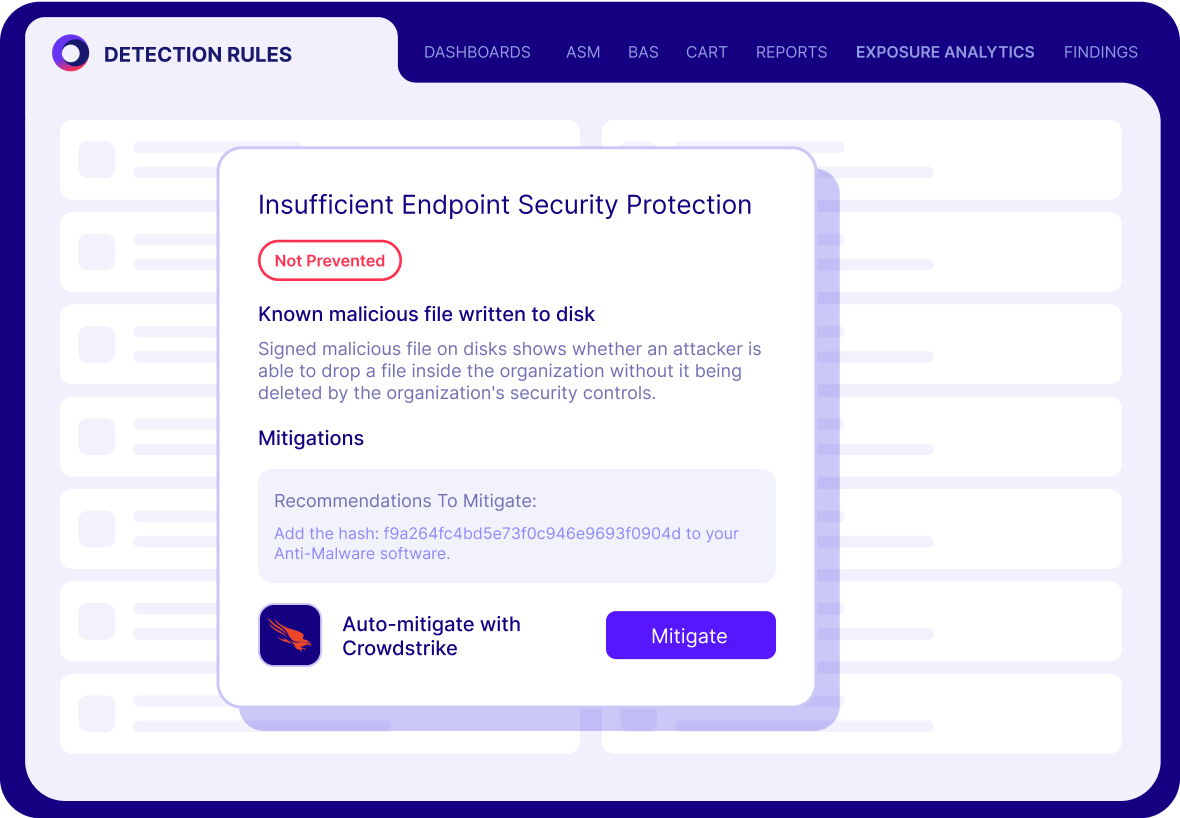
The Cymulate Exposure Management Platform uses breach and attack simulation and automated red teaming to validate threat resilience by testing security controls with real-world attacks that identify control weaknesses. For any validated threat, Cymulate includes policy tuning guidance, automated control updates and custom mitigation rules that can be directly applied to your security controls to improve threat prevention and detection
Solution Benefits
Automated threat validation
Identify gaps and weaknesses
Optimize security controls
Reduce exposure risk
What our customers say about us
Organizations across all industries choose Cymulate for exposure validation, proactively confirming that defenses are robust and reliable-before an attack occurs.
Threat Resilience FAQs
Automated threat validation is the process of continuously testing your security controls using real-world attack techniques. Cymulate uses AI-powered breach and attack simulation (BAS) and automated red teaming to validate your defense posture and identify gaps in threat prevention and detection.
Threat resilience ensures your organization can detect, prevent and respond to cyberattacks before they become incidents and breaches. Cymulate enhances threat resilience by helping teams baseline security posture, validate threats and implement immediate mitigation strategies.
Cymulate identifies vulnerabilities in your security stack and offers automated mitigation and control tuning. Organizations using Cymulate see up to a 30% gain in threat prevention, 3x improvement in detection and 60% operational efficiency gains.
Cymulate validates threats across the full kill chain — including phishing, malware, lateral movement, data exfiltration and zero-day exploits — using daily updated threat templates and AI-generated attack plans.
Yes. Cymulate tests and validates security controls like SIEM, EDR, WAF, email gateways, web gateways, network IPS and firewalls to score current prevention and detection rates and then provide remediation and guidance to improve prevention and detection for threats that were missed.
Cymulate supports continuous and on-demand testing. This allows organizations to regularly assess their resilience and quickly adapt to emerging threats without waiting for periodic audits or manual testing.