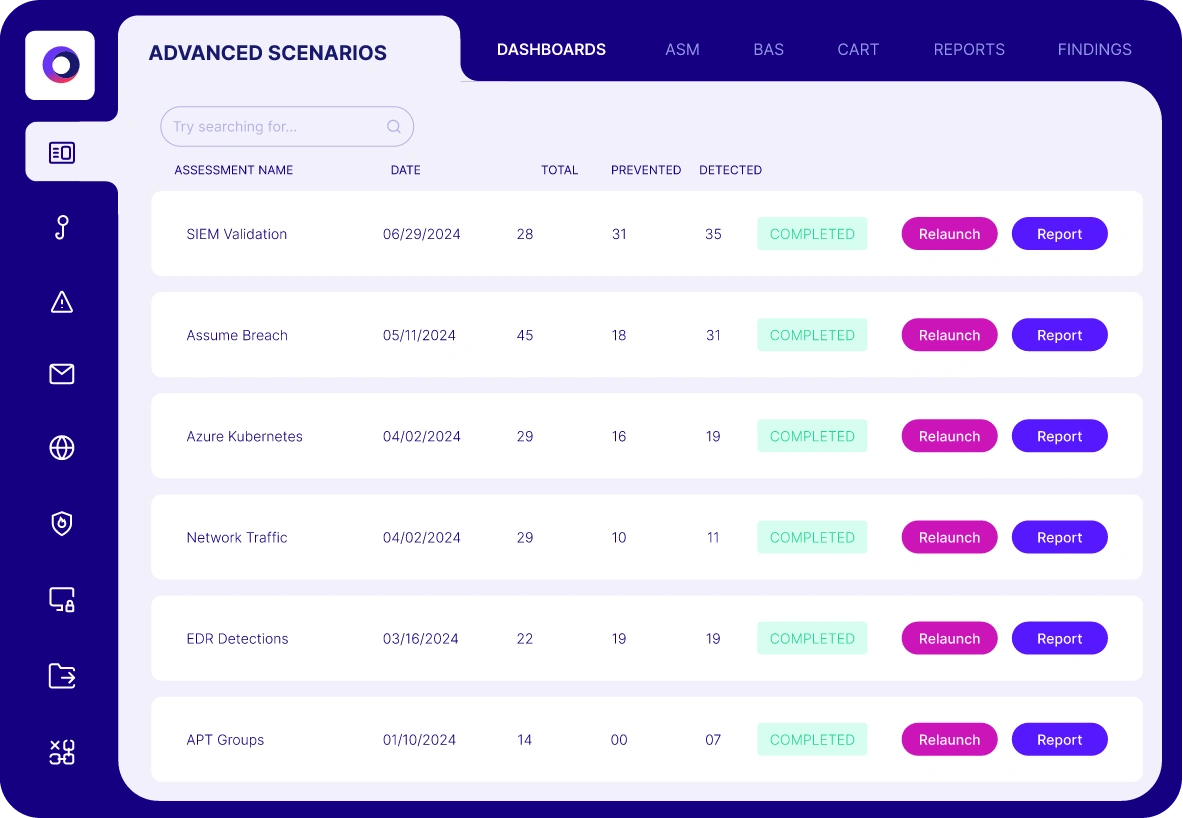
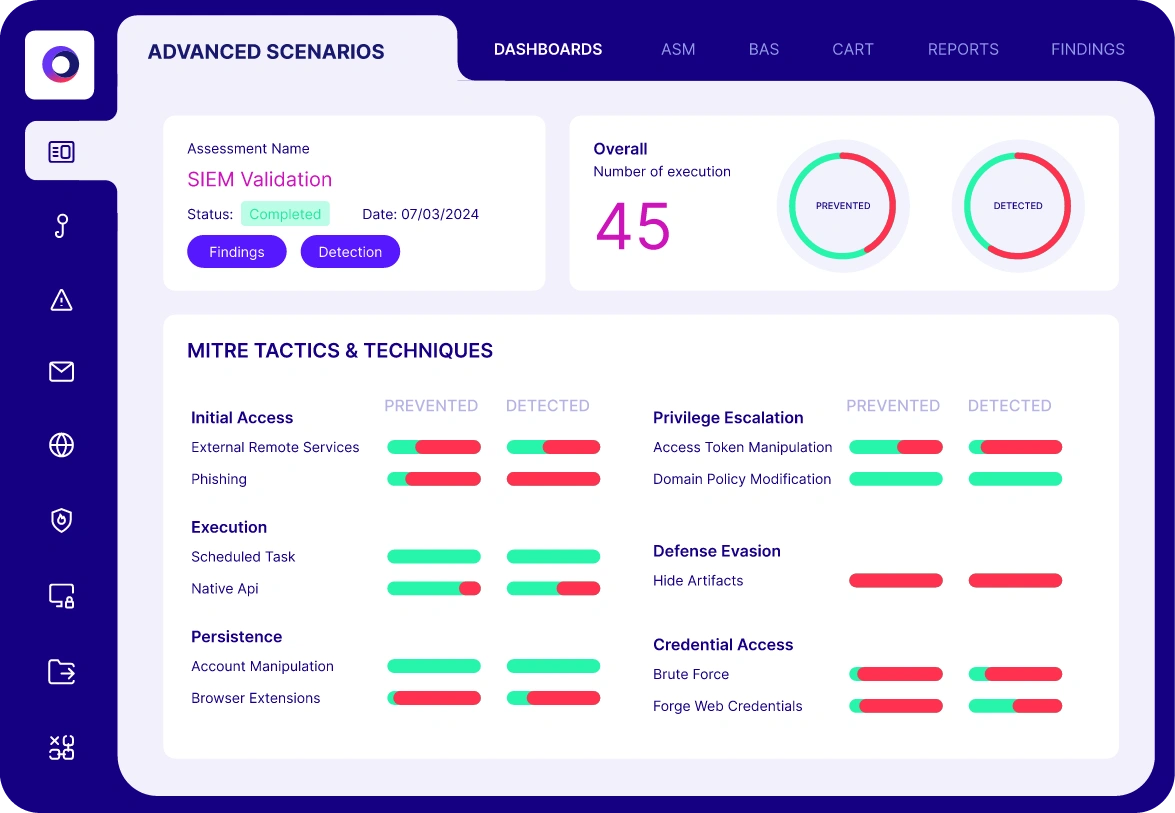
SIEM Validation
Test and optimize your SIEM detections against the latest attack tactics and techniques.
Detection is your last line of defense against exposure to a potential cyber incident.
Average coverage of
MITRE techniques
Source: IBM
Average days to
discover a breach
Source: IBM
Average cost of
a data breach
Source: IBM
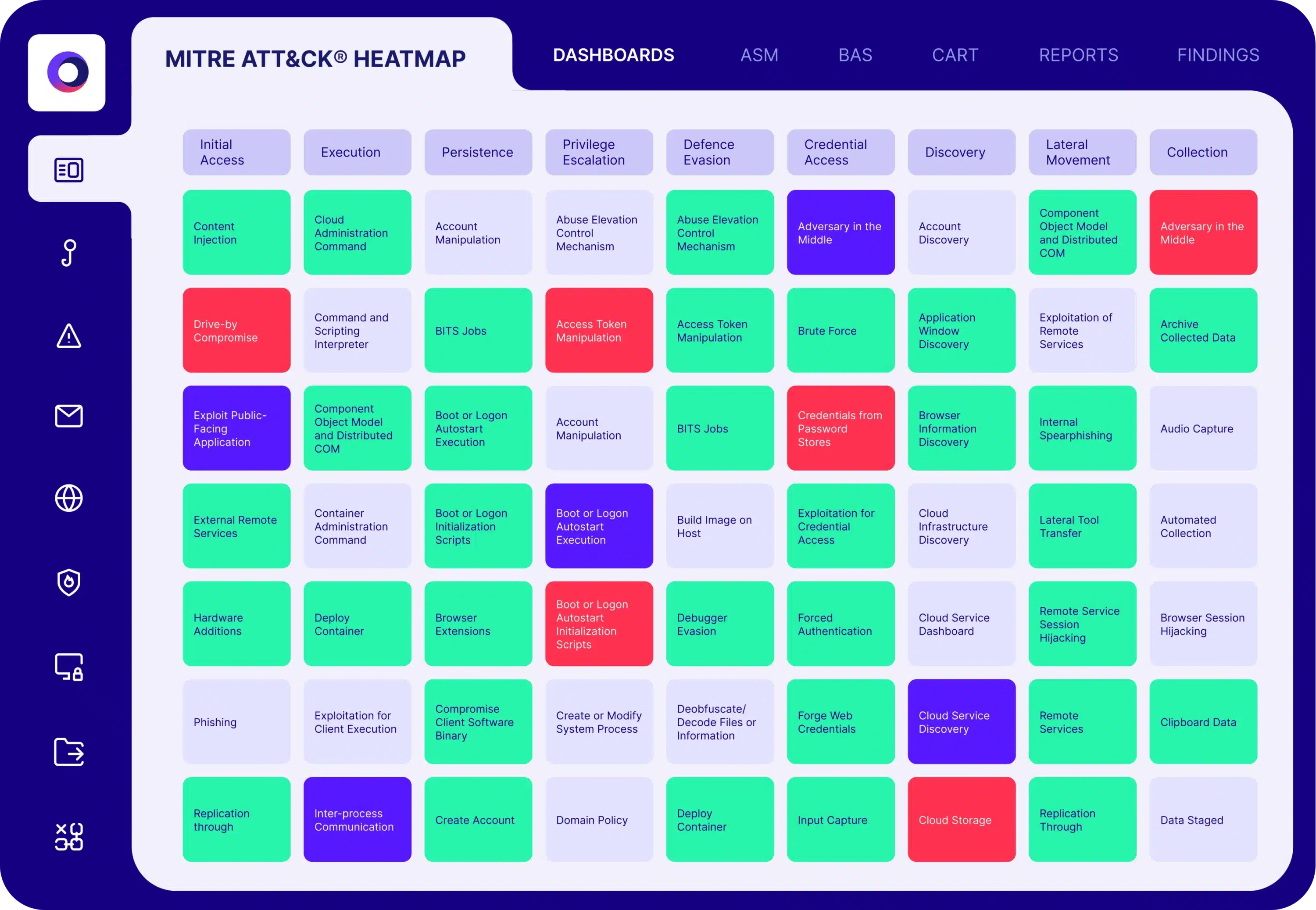
Automated Security Validation for SIEM
Cymulate uses breach and attack simulations to test and optimize the effectiveness of your SIEM detection rules. The automated security validation simulates different types of attack scenarios and high-privileged activities that should generate detections within your SIEM from:
- Immediate threats
- Endpoint threats
- Cloud and container threats
- Assume breach (high-privilege) threats
- Other persistent threats
Solution Results
91%
Improvement in malicious
file detection
50%
Improvement in the prevention of known exploit techniques
168
Exploits prevented from a single recommended policy change
Solution Benefits
Continuous validation
Identify missed detections
Optimize security controls
Reduce exposure risk
What our customers say about us
Organizations across all industries choose Cymulate for automated security validation, proactively confirming that defenses are robust and reliable-before an attack occurs.