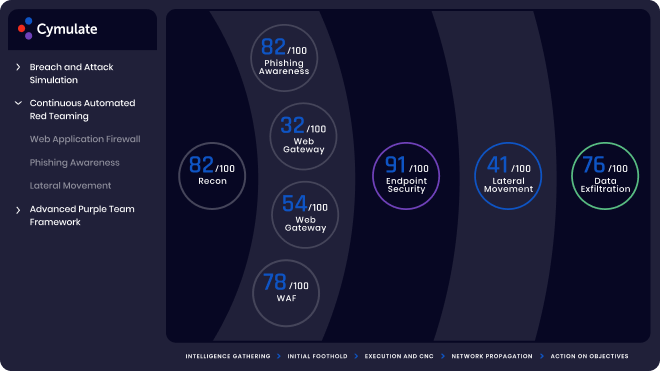
Visibility Across the Full Cyber Kill Chain
Assure daily the operational effectiveness of your security stack that protect your IT environment, cloud initiatives and critical data against threat evolutions
Learn More

Globee Awards
Gold Winner

2024 Leader
for ASM

Most Innovative
Tech Company

Best Breach and
Attach Simulation
Platform

Top 100
Cybersecurity
Startups

Top 100
Cybersecurity
Startups

Best Breach and
Attach Simulation
Platform








