December 2nd, 2024
Under the EDR Radar: A Deep Dive into Binary Exploitation
August 15th, 2024
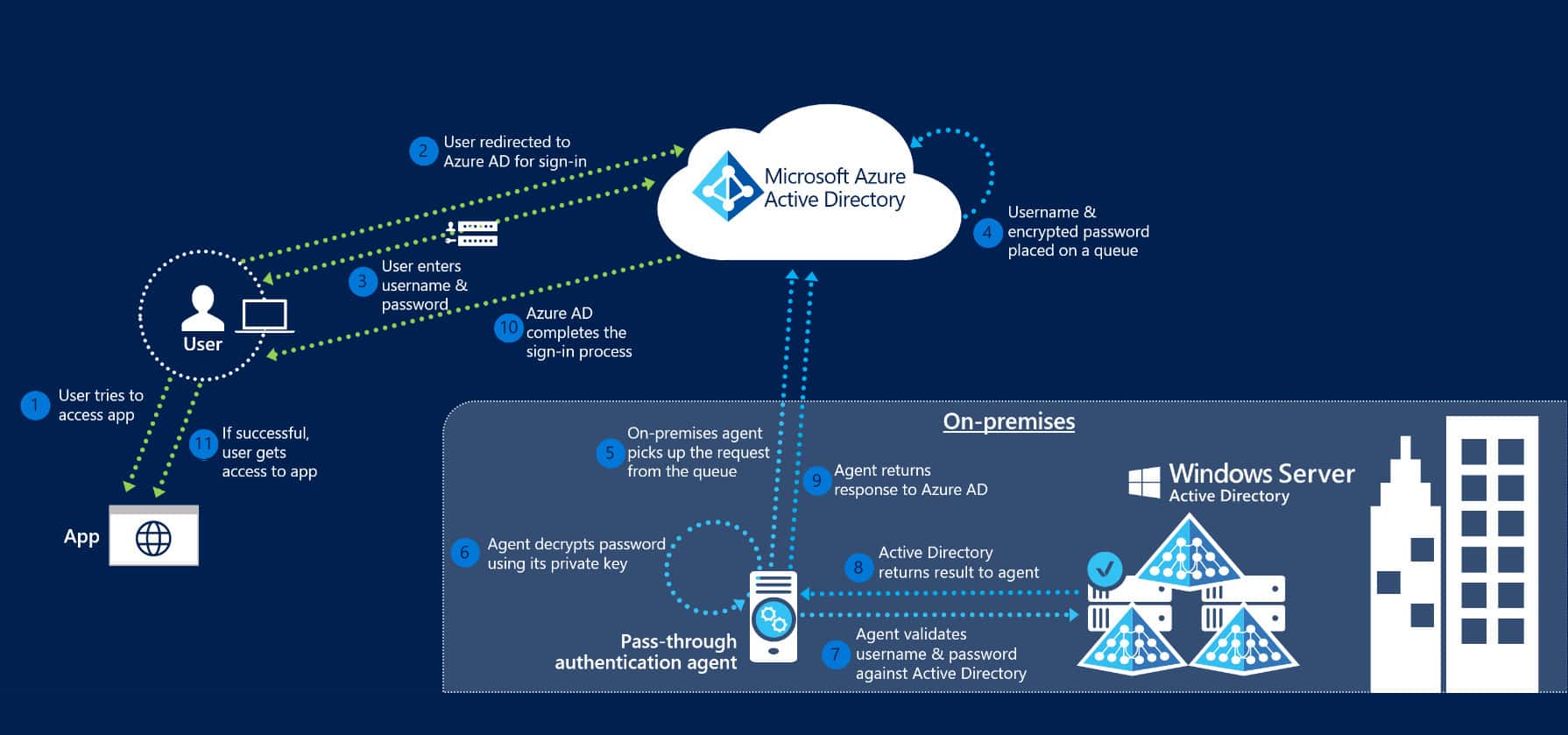
Double Agent: Exploiting Pass-through Authentication Credential Validation in Azure AD

February 14th, 2024
How Attackers Bypass EDR: Techniques & Defense Strategies

February 8th, 2024
Understanding Endpoint Defense: EDR, XDR, and Anti-Virus Explained

February 1st, 2024
Cyber Threat Breakdown January 2024

January 3rd, 2024
Cyber Threat Breakdown December 2023

December 14th, 2023
Why Legacy Malware Keeps Succefully Attacking Networks

December 7th, 2023
How to Keep Network Traffic Secure with Security Validation

December 5th, 2023
Cyber Threat Breakdown November 2023

July 25th, 2023







