Not All Security Automations Are Born Equal
As business environments grow more complex and the threat landscape evolves, security teams increasingly rely on automated security testing. This shift enables more frequent, thorough, and streamlined testing. However, automation doesn’t necessarily mean simplicity. Just as pilots must train extensively to manage autopilot systems, automated pen-testing is most effective in the hands of expert pen testers. On the other hand, Breach and Attack Simulation (BAS) makes security testing more accessible for security analysts with diverse skill levels, simplifying the process.
To understand the differences in automated pen-testing and BAS, let’s examine their unique approaches. While both can identify security gaps, they differ in scope, frequency, and results.
Scope of Automated Penetration Testing
In automated pen-testing:
- The scope and objectives are pre-defined.
- The test yields a binary result: was the objective achieved?
- Skilled pen testers use automation to speed up repetitive tasks, adapting their efforts to each test’s scope.
Automated pen-testing answers the question, “Can an attacker get in, and how?” It automates repetitive actions, allowing pen testers to:
- Identify gaps in specific security controls.
- Detail the techniques used to evade controls.
- Provide remediation recommendations, specifically aligned with the test’s scope.
Scope of Breach and Attack Simulation
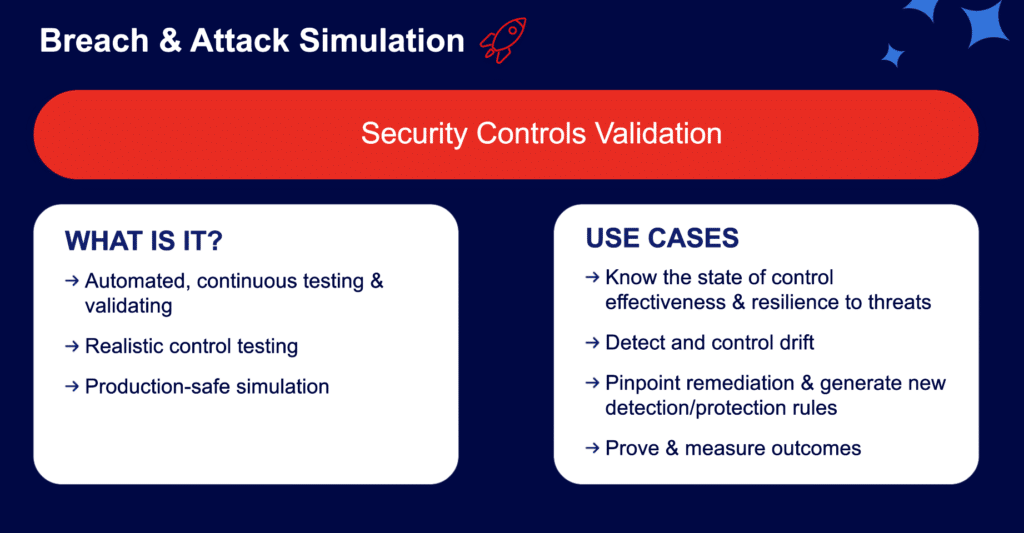
Breach and Attack Simulation (BAS) takes a different approach by testing each security control and the full kill chain as often as needed. It answers, “How well do our controls detect and stop attackers?” BAS offers three primary benefits:
- Individual Control Testing: BAS evaluates the effectiveness of endpoint, web gateway, email gateway, DLP, and web application firewall controls, providing scores and mitigation tips.
- Broad Security Posture Assessment: BAS assesses an organization’s readiness against both known and emerging threats.
- Comprehensive Visualization: BAS maps all potential lateral movement paths using techniques similar to pen testers but without a defined scope limitation.
BAS relies on the platform’s embedded expertise rather than the end-user’s skill level. This simplicity does not sacrifice detail; it provides a broad, accurate report based on a wide array of tests that reflect real-world scenarios beyond a scoped pen test.
Frequency and flexibility of BAS
With the need for security teams to adapt to ever-changing threats, BAS outshines automated pen-testing in its frequency. BAS allows continuous testing, supporting a proactive, adaptable defense.
Why Cymulate for Breach and Attack Simulation?
Cymulate is a SaaS-based BAS platform that empowers organizations to test, measure, and optimize their security controls continuously. With just a few clicks, Cymulate simulates thousands of attacks, revealing exposures and offering actionable fixes—integrating security seamlessly into daily operations.
Ready to see how Cymulate can elevate your security testing? Book a demo today to experience firsthand how continuous security validation can help protect your organization. Discover your vulnerabilities, gain actionable insights, and make security a seamless part of your everyday operations.










