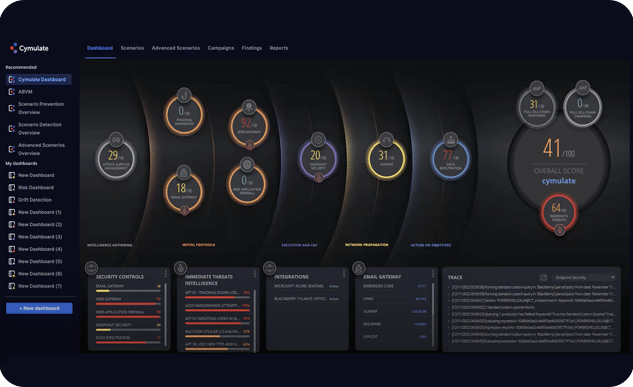
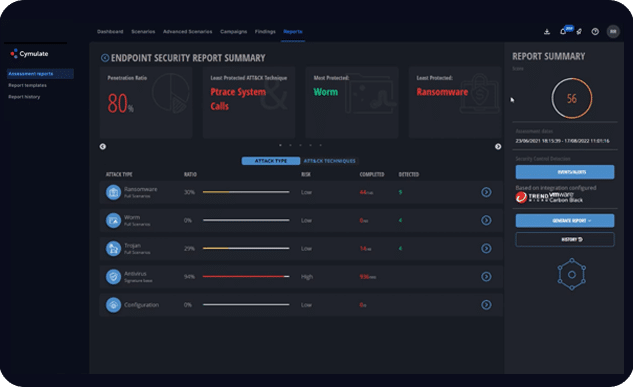
Why Integrate SIEM With Cymulate?
Together with our SIEM Partners, Cymulate can help organizations fine-tune their configuration to ensure better coverage of security incidents, provide additional context to security events to help prioritize and optimize response efforts to ensure that the most critical threats are addressed first.


Splunk Enterprise Security – (Splunk ES) SIEM solution aims to provide data-driven insights, combat threats, protect organizations and mitigate risks at scale with actionable analytics.


IBM® QRadar® – Security Information and Event Management (SIEM) helps security teams accurately detect and prioritize threats across the enterprise, and it provides intelligent insights that enable teams to respond quickly to reduce the impact of incidents.


Crowdstrike Falcon LogScale – Formerly known as Humio, is a centralized log management technology that allows organizations to make data-driven decisions about the performance, security and resiliency of their IT environment.


Rapid7’s InsightIDR – identifies unauthorized access from external and internal threats and highlights suspicious activity so you don’t have to comb through hundreds of data streams. Rapid7’s InsightIDR provides incident detection and response, authentication monitoring, and endpoint visibility.


LogRhythm – provides a comprehensive and dynamic security operations platform, technology partnerships, and advisory services to help SOC teams close security exposures.LogRhythm specializes in Security Information and Event Management (SIEM), log management, network and endpoint monitoring and forensics, and security analytics.


Micro Focus ArcSight – is a cybersecurity product that provides real-time data security analytics and intelligence software for security information and event management (SIEM) and log management. ArcSight helps customers find and prioritize security threats, categorize and track incident response activities, and simplify audit and compliance activities.


Microsoft Azure Sentinel – Azure Sentinel, renamed to Microsoft Sentinel, is a cloud native security information and event management (SIEM) and security orchestration, automation, and response (SOAR) solution that runs in the Azure cloud.
RSA Netwitness -NetWitness is a comprehensive XDR solution that accelerates threat detection and response. It collects and analyzes data across all capture points (logs, packets, netflow, endpoint and IoT) and computing platforms (physical, virtual and cloud), enriching data with threat intelligence and business context.


Sumo Logic – provides automatic collection, ingestion, and analysis of application, infrastructure, security, and IoT data to deliver actionable insights immediately. Sumo Logic delivers its platform as a true, multi-tenant SaaS architecture for maximum convenience and efficiency.


Trellix – Trellix (formerly FireEye and McAfee Enterprise) is a privately held cybersecurity company founded in 2022. It has been involved in the detection and prevention of major cybersecurity attacks.


Securonix – Securonix collects massive volumes of data in real time, detects advanced threats using innovative machine learning algorithms, enables you to quickly investigate the alerts that matter the most, and provides actionable security intelligence for an automated response.


Google Chronicle – a cloud service, built as a specialized layer on top of core Google infrastructure, designed for enterprises to privately retain, analyze, and search the massive amounts of security and network telemetry they generate.


McAfee – is an award-winning antivirus software protects your data and devices. McAfee tries to ensure that private data would not be compromised by offering a variety of services for identity protection: a password manager, a VPN, a file shredder, etc.

Exabeam SIEM – extends the cloud-scale capabilities of Exabeam Security Log Management with additional features for threat, detection, investigation, and response (TDIR). Exabeam SIEM includes Threat Center, over 160 pre-built correlation rules, integrated threat intelligence, automation management, and powerful dashboarding capabilities.


Elastic SIEM – The solution unifies the capabilities of SIEM and security analytics, endpoint detection and response (EDR), and cloud security. Get more from a SIEM solution engineered for tomorrow’s threat landscape. See how Elastic Security works in this short SIEM demo.
Why Integrate EDR With Cymulate?
Cymulate continuously tests the effectiveness of EDR solutions to provide organizations with more robust and effective cybersecurity posture management. Together with our EDR ecosystem partners we can uncover security gaps that can expose organizations to threats, provide insights to prioritize and optimize response efforts, and give organizations a more proactive and comprehensive approach to its cybersecurity posture.


VMware Carbon Black – Cloud is a software as a service (SaaS) solution that provides next-generation anti-virus (NGAV), endpoint detection and response (EDR), advanced threat hunting, and vulnerability management within a single console using a single sensor.


Microsoft Defender for Endpoint – provides multiple monitoring and control features to help prevent threats from removable devices, including new settings to allow or block specific hardware IDs.


SentinelOne – is an endpoint protection platform designed for enterprises in the healthcare, education, finance, and energy industries


BlackBerry® CylancePROTECT – prevents breaches and provides additional security controls to safeguard against script-based, fileless, memory, and external device-based attacks.
BlackBerry® CylanceOPTICS – is an AI-driven endpoint detection and response component providing consistent visibility, root cause analysis, scalable threat hunting, and automated threat detection and response.


Crowdstrike Falcon LogScale – Formerly known as Humio, is a centralized log management technology that allows organizations to make data-driven decisions about the performance, security and resiliency of their IT environment.


Cynet – converges essential cyber security technologies that help enterprises to identify security loopholes and threat intelligence and manage endpoint security.


Palo Alto Cortex XDR – is the world’s first detection and response app that natively integrates network, endpoint, and cloud data to stop sophisticated attack


Trellix – Trellix (formerly FireEye and McAfee Enterprise) is a privately held cybersecurity company founded in 2022. It has been involved in the detection and prevention of major cybersecurity attacks.


The Cybereason – defense Platform moves beyond endless alerting to instead recognize, expose, and end malicious operations before they take hold. The result: Defenders can end attacks in minutes.


Trend Micro’s – cybersecurity platform protects hundreds of thousands of organizations and millions of individuals across clouds, networks, devices, and endpoints. As a leader in cloud and enterprise cybersecurity, the platform delivers a powerful range of advanced threat defense techniques optimized for cloud environments like AWS, Microsoft, and Google, and central visibility for better, faster detection and response.


Tanium’s Cloud Platform – is a single platform that delivers complete, accurate and real-time endpoint data regardless of scale and complexity. Tanium is a feature-packed endpoint management and endpoint security platform designed to strengthen and optimize an organization’s cybersecurity efforts.


Cisco Secure – is Cisco’s comprehensive security product portfolio. Cisco Security products offer unmatched efficacy in data protection, providing security that’s not only agile and adaptable, but also incredibly easy to use. Cisco Secure Endpoint offers cloud-delivered endpoint protection and advanced EDR across multi-domain control points. We stop threats and block malware then rapidly detect, contain, and remediate advanced threats that evade front-line defenses.


Harmony Endpoint – Harmony Endpoint is a complete and consolidated endpoint security solution with advanced EPP, EDR and XDR capabilities, built to protect the remote workforce from today’s complex threat landscape. Single Agent EPP, EDR & XDR, all in a single client and management console.
Why Integrate Vulnerability Management With Cymulate?
Together with our Vulnerability Management partners, Cymulate can help identify vulnerabilities and prioritize them based on their severity, while testing and validating remediation efforts to ensure the organization’s systems and applications are secure. Automating vulnerability testing can make security teams more efficient and reduce the burden on IT to identify vulnerabilities and move quickly to reduce the risk of successful attacks.


Powered by Nessus technology, Tenable.io and Tenable.sc provides the industry’s most comprehensive vulnerability coverage with the ability to predict which security issues to remediate first. It’s your complete end-to-end vulnerability management solution.


Microsoft Defender VM – serves as an infrastructure for reducing organizational exposure, hardening endpoint surface area, and increasing organizational resilience.


Rapid InsightVM – provides visibility into the vulnerabilities in modern IT environments—including local, remote, cloud, containerized, and virtual infrastructure. It adds clarity into how those vulnerabilities translate into business risk and which are most likely to be targeted by attackers.


Qualys Vulnerability Management – is a cloud-based solution that detects vulnerabilities on all networked assets, including servers, network devices (e.g., routers, switches, firewalls, etc.), peripherals (such as IP-based printers or fax machines) and workstations. Qualys can assess any device that has an IP address.
Why Integrate your SOAR and GRC Systems with Cymulate?
With the Cymulate integration, organizations leverage assessment data within other platforms and workflows which permits higher levels of automation and streamlined compliance operations.


Palo Alto Cortex XSOAR (Demisto) – is a comprehensive security orchestration, automation and response (SOAR) platform that unifies case management, automation, real-time collaboration and threat intel management to serve security teams across the incident lifecycle.


IBM Resilient SOAR – The IBM Resilient SOAR platform provides your security team the ability to automate case management for security or privacy events and can be used to automate and document your incident response plans.
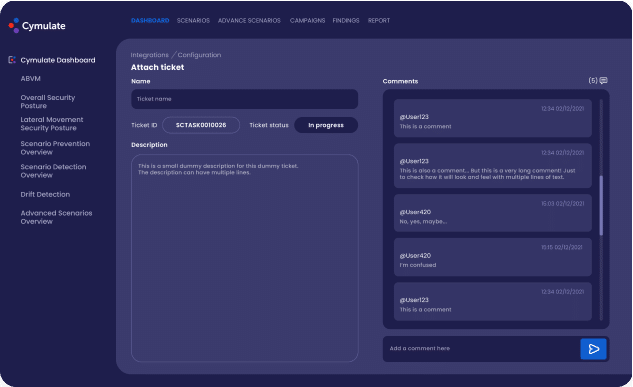
Why Use Ticketing Solutions Integrated With Cymulate?
Together with our Ticketing Systems partner, we help organizations improve their security posture by providing security teams with increased visibility and improved remediation efforts by automatically generating tickets for identified security issues. With an integrated ticketing system, security teams can streamline workflows and reduce the time it takes to respond to security incidents.


Servicenow – is a cloud-based platform that automates everyday service requests.Their AI-powered
Now Platform syncs data across applications and systems to provide workflow automation at an enterprise scale. Cymulate’s integration with ServiceNow enables security teams to manage security tasks from
within the Cymulate platform. This integration helps streamline security ticket management so security
and IT teams can respond to threats faster, more efficiently, and stay focused on what is most critical
to the organization.


Jira – Cymulate’s integration with Jira allows your development team to become more efficient. It can instantly communicate, create, share and organize project development documentation, schedule and track Jira issues, and better plan a project development strategy.
Why Integrate your Firewall Systems with Cymulate?
Together with our Firewall Systems partners we challenge an organization’s network firewall against a comprehensive set of attacks to validate inbound and outbound communication’s configuration settings and policies. This integration enables the results to appear directly in Cymulate’s reports so organizations can respond to threats faster and streamline remediation.


Palo Alto Networks Next-Generation Firewalls – Palo Alto Networks offers superior architecture with superior benefits: Complete visibility and precise control: Our next-generation firewalls provide complete visibility into all network traffic based on applications, users, content and devices.
A next-generation firewall (NGFW) is a firewall designed to protect against the modern cyber threats that companies face. In addition to the core functions of a firewall, NGFWs integrate a range of other capabilities to protect against advanced cyber threats.

Visibility Across The Full
Cyber Kill-Chain
Assure daily the operational effectiveness of your security stack
that protect your IT environment, cloud initiatives, and critical
data against threat evolutions

The Partner Ecosystem
Overview
which makes it simple to measure and improve security posture across
the full attack kill-chain.
and benefit existing security solutions, while automating and
simplifying security control validation.
“Cymulate has been helping me to evaluate my security posture against behavior based as well zero day threats.”
– IT Security & Risk Management Associate
“Technical capabilities provided are outstanding, customer service is highly responsive and product mgmt. is flexible in supporting us with our requests.”
– Security Operations Analyst
“The Cymulate BAS is delivering excellent outcomes, contributing significantly to enhancing my security effectiveness.”
– IT Security & Risk Management Associate
“My experience with the platform was exceptional. It delivers on its promises with easy navigation, effective mitigation steps, and top-notch after sales support.”
– Chief Risk Manager
“Always willing to help offering training sessions and encourage use of the product’s additional available features.”
– Senior Software Engineer
“I believe that Cymulate brings a vision of risks, vulnerabilities and actions that we are unable to pay attention to in our work day.”
– Security Operations Specialist
“The range and breadth of attack scenarios, potential targets and how well each tool integrates is really excellent.”
– Penetration Tester
“We had an excellent experience with Cymulate, from product deployment to while using the platform.”
– Senior Cybersecurity Engineer
“Awesome customer Support and techniques used by Cymulate to identify security gaps.”
– IT Security & Risk Management