
Ruben Jami, July 14th, 2022
Sigma Rules: Revolutionizing SOC Efficiency and Lightening Engineers’ Workloads

Aviva Kochavi , November 8th, 2021
Continuous Security Validation: The Key to Proactive Cybersecurity
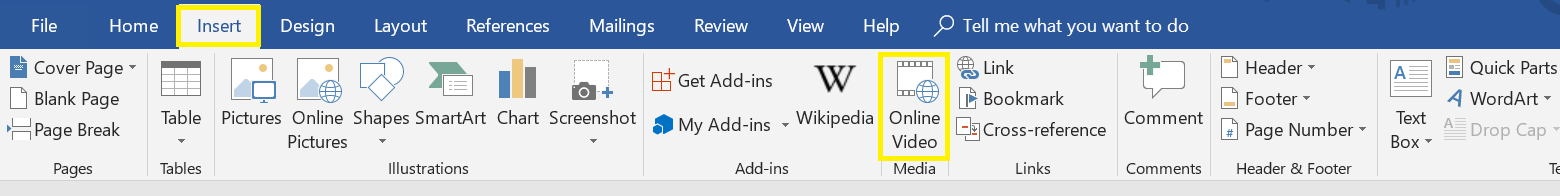
October 6th, 2021
Abusing Microsoft Office Online Video

Eyal Aharoni, February 21st, 2021
Watering Hole Attack: How It Works and How to Prevent It
Show






