To a lion, the watering hole is more than just a drinking source – it’s the perfect place to attack unaware prey. Waiting for victims to lower their guard is much easier than the usual tracking and attacking method. To a hacker, the game plan is largely the same when conducting a cyberattack in this method. Infect a website typically frequented by an individual of a specific group and wait.
What is a “Watering Hole” attack?
A watering hole attack is a cybersecurity strategy where attackers compromise a website or service frequently visited by a specific target group. The attackers infect the website with malware to gain access to the visitors’ systems.
The goal is usually to swipe username and password combinations, or infect a victim’s computer and gain access to a larger network, such as their employer.
Watering hole attacks are designed to potentially capture a larger network of victims than just those who were attacked originally. They focus on specific groups or communities, seeking out particular interests.
Cybercriminals often use new or hacked websites, exploiting unknown software flaws and hidden methods to bypass regular antivirus programs. These attacks are often successful, making them a big challenge for cybersecurity.
Watering Hole Attacks vs Phishing
While phishing typically involves sending deceptive emails or messages to individuals, enticing them to click on malicious links or provide personal information, watering hole attacks take a more indirect route by exploiting the trust users place in familiar websites.
Watering Hole Attacks vs Pharming
In a watering hole attack, cybercriminals compromise legitimate and websites known to the victim, while pharming on the other hand involves redirecting website traffic to fraudulent versions of legitimate websites, often by tampering with DNS settings or exploiting vulnerabilities in networking infrastructure. Both tactics aim to deceive users and steal sensitive information, watering hole attacks leverage compromised websites, while pharming manipulates the domain name resolution process to direct users to malicious sites.
How Does a Watering Hole Attack Work?
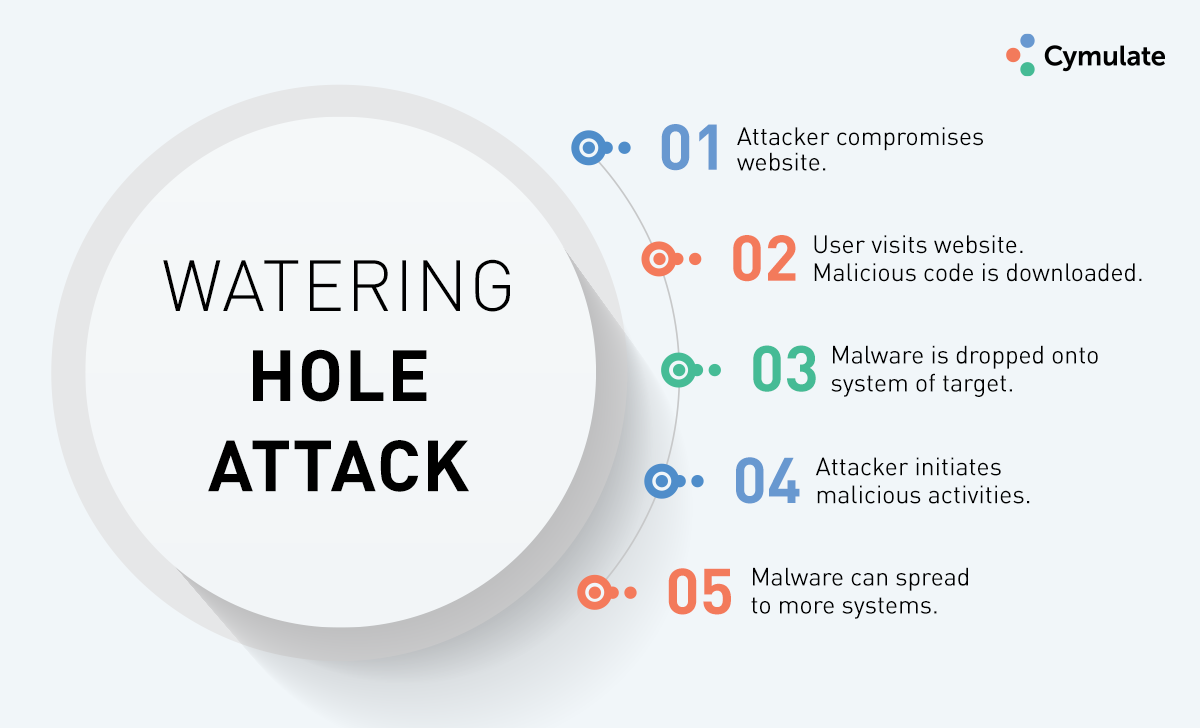
- First, the attackers profile their targets by industry, job title, etc. This helps them determine the type of websites and targeted applications often visited and used by the employees or members of their targeted entity.
- The attacker then creates a new website or looks for vulnerabilities in these existing websites and applications to inject malicious code that redirects the targets to a separate site where the malware is hosted.
- The exploit drops the malware onto the target’s system.
- The attacker now uses the dropped malware to initiate its malicious activities. Also, knowing that most people still sadly reuse passwords, the attacker often collects usernames and passwords to attempt credential-stuffing attacks against targeted applications, enterprises, and sites.
- Once the victim’s machines, applications, enterprises, and sites are compromised, the attackers will perform lateral movements within the victim’s network and ultimately exfiltrate data.
Examples of known attacks and common targets
Typical victims of watering hole attacks tend to include employees of organizations within specific industries, such as finance, healthcare, or technology, as well as government agencies, research institutions, or companies involved in sensitive areas like defense or energy.
A diverse victim set, watering hole attacks are being used by everyone from the Chinese government against political dissidents, foreign APTs against US nuclear scientists, and industrial espionage against US/UK defense contractors, as well as organizations such as the U.S. Council of Foreign Relations who were infected in 2012 by a zero-day vulnerability in Microsoft’s Internet Explorer.
The Holy Water Campaign
In 2019, a large, sophisticated watering hole attack that became known as the Holy Water Campaign, targeted religious and charitable websites primed at Asian religious minorities. The attackers compromised these sites to deliver malware, specifically the ScanBox framework, to the website visitors.
The Holy Water campaign was designed to gather extensive data from infected users’ systems, including their browsing habits, and other sensitive information. The campaign was attributed to the threat actor group TA413, commonly believed to be sponsored by the Chinese government.
How to prevent watering hole attacks
Preventing watering hole attacks requires a combination of proactive measures and ongoing security efforts. Some steps to help mitigate the risk of falling victim to such attacks:
- Continuously test your current security solutions and controls to verify they provide adequate defense against application and browser-based attacks.
- Ensure your security controls prevent criminal redirection, malware, and rootkits from being successfully deployed. Ensure that browser control and endpoint software are adequately tuned and that web content and security proxy gateways are well configured. Organizations must seek additional layers of advanced threat protection, such as behavioral analysis, which is more likely to detect zero-day threats.
- Update systems with the latest software and OS patches offered by vendors.
- All third-party traffic must be treated as untrusted until otherwise verified. It should not matter if content comes from a partner site or a popular Internet property like a Google domain.
- Educate your end-users on what watering hole attacks are by creating easy-to-understand corporate materials you distribute.
How Cymulate can help
Cymulate specializes in continuous security validation, designed to help prevent watering hole attacks and other cyber security threats by using the following methods:
- Simulation: Cymulate can simulate watering hole attacks to test the effectiveness of your current security measures. By running these simulations, organizations can identify weaknesses in their defenses and take proactive measures to address them before a real attack occurs.
- Endpoint Security Testing: assess the security posture of endpoints within an organization’s network. This includes testing for vulnerabilities that could be exploited by watering hole attacks, such as outdated software or misconfigured security settings.
- Web Application Security Testing: evaluate the security of web applications to ensure they are not susceptible to exploitation by attackers. This includes checking for vulnerabilities such as SQL injection or cross-site scripting (XSS) that could be used in a watering hole attack.
- Email Security Testing: Since watering hole attacks often involve the use of phishing emails to lure victims to the compromised website, Cymulate can simulate phishing attacks to assess the effectiveness of an organization’s email security controls. This helps in identifying and mitigating risks associated with phishing-based watering hole attacks.
- Continuous Monitoring and Assessment: Pprovide continuous security validation, allowing organizations to regularly assess their security posture and adapt to evolving threats. By continuously monitoring for potential watering hole attack vectors, organizations can detect and respond to threats in a timely manner.
- Training and Awareness: Cymulate can also be used to simulate phishing attacks as part of security awareness training programs. By educating employees about the dangers of watering hole attacks and how to recognize and respond to phishing attempts, organizations can reduce the likelihood of successful attacks.











