Breach and attack simulation (BAS) tools have emerged as a critical component of a modern cybersecurity program. As threats continue to increase in sophistication, solutions capable of validating security controls’ efficacy and exposing potential vulnerabilities are key to closing security gaps before attackers exploit them.
Top BAS Use Cases
While validating security controls and assessing overall posture are the primary applications, advanced organizations can get additional value from tailored BAS programs.
1. Risk-based vulnerability management
BAS simulations are instrumental in prioritizing patching efforts based on real-world exploitability rather than just CVSS scores. Leveraging BAS to simulate the exploitation of known vulnerabilities yields actionable insights into which vulnerabilities are likely to be successfully exploited within their environment despite the security measures in place. This enables smarter vulnerability prioritization and the allocation of resources to vulnerabilities, misconfigurations, and other security gaps that pose the highest contextual risk.
By testing vulnerabilities against the specific compensating controls implemented, BAS validates whether firewalls, network segmentation, endpoint security, and other defenses sufficiently mitigate each vulnerability’s exposure risk. If the simulation succeeds in exploiting a vulnerability despite controls, it is prioritized for patching, while vulnerabilities blocked by existing security measures are deprioritized.
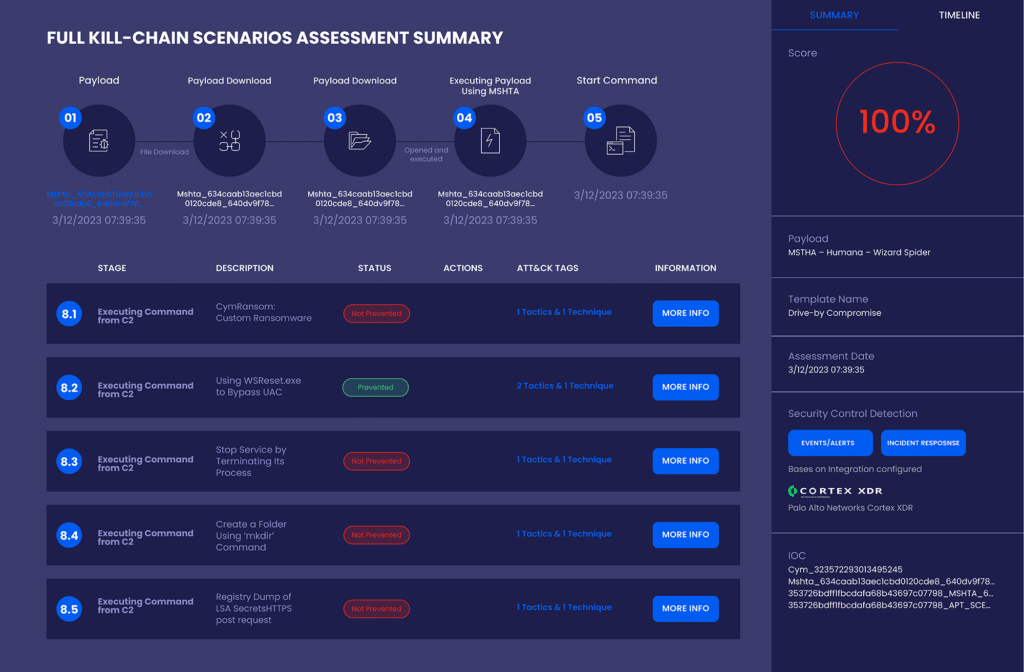
How it works: Ready-made or customized attack scenarios can be scheduled or launched ad-hoc to simulate exploitation techniques. These scenarios attempt to exploit vulnerabilities, challenging the efficacy of security controls like web application firewalls and endpoint detection.
2. Measure and improve security operations
BAS is effective in moving from security baselining to quantifying cyber performance by benchmarking and tracking improvements in key performance metrics. BAS data quantifies changes in detection rates, investigation timelines, and remediation speeds. These continuous and objective measurements identify security drift early, prompting early remediation action. They also demonstrate each tool stack component’s ROI and identify redundant tools and missing capabilities, which facilitate budget optimization and request for further investment.
How it works: The first run of attack simulation provides baseline metrics to evaluate the exposure of each assessed security control type (i.e., Endpoints, WAF, firewalls). Subsequent launches of similar or emerging attack simulation scenarios provide visibility into each security control cyber-resilience evolution, and granularly identify the tools’ ability to detect and/or respond to raise alarm or stop the launched attack scenarios.
3. Test security posture against emerging threats
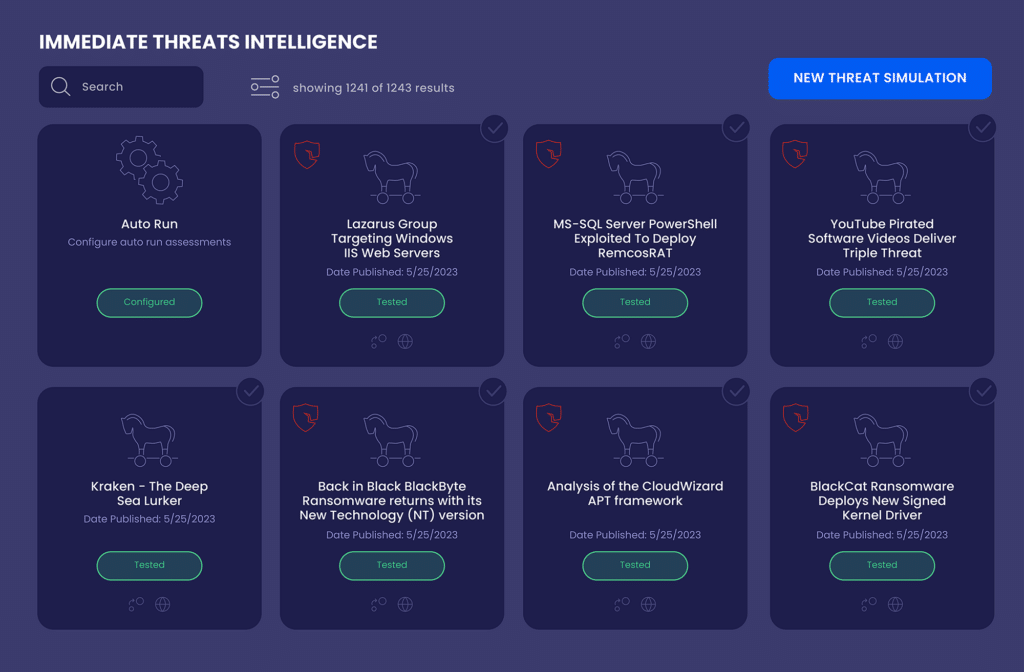
By Integrating with threat intelligence feeds, BAS can assess organizational resilience against new and emerging threats. The more advanced BAS solutions can rapidly develop and deploy simulations of emerging threat techniques and adversary campaigns. This enables security teams to validate, in near real-time, whether their existing controls and detections can withstand the latest attack behaviors.
How it works: BAS vendors develop new tactics or scenarios to defend against new malware, exploits, and adversary TTPs as soon as they are reported by threat intel sources. Scheduling and running these simulations as soon as they are released assesses the defenses’ effectiveness against these emerging threats. Findings identify control gaps and detect blind spots to be addressed.
4. Optimize SIEM
Security Information and Event Management (SIEM) systems collect and analyze log and event data from across an organization’s infrastructure to enable real-time detection and response to threats. However, SIEMs require extensive expert configuration and continuous fine-tuning to maximize value. BAS provides a robust methodology for validating and optimizing SIEM detection efficacy.
Most SIEMs come with default rules and algorithms to identify potential attacks. But these generic detections result in poor signal-to-noise ratio and threat coverage gaps in the unique environment of each organization. Properly configuring correlation rules and machine learning models to the specific infrastructure, behaviors, and threat landscape is challenging.
How it works: BAS simulates real-world threats generating high-fidelity event data tailored to the environment. Security teams analyze BAS telemetry to identify detection gaps, false positives, and optimization opportunities. New correlation rules and ML refinements are developed based on BAS findings and validated with additional simulations, rapidly improving SIEM threat alerting accuracy and coverage. This ultimately reduces mean-time-to-detect and incident response burdens.
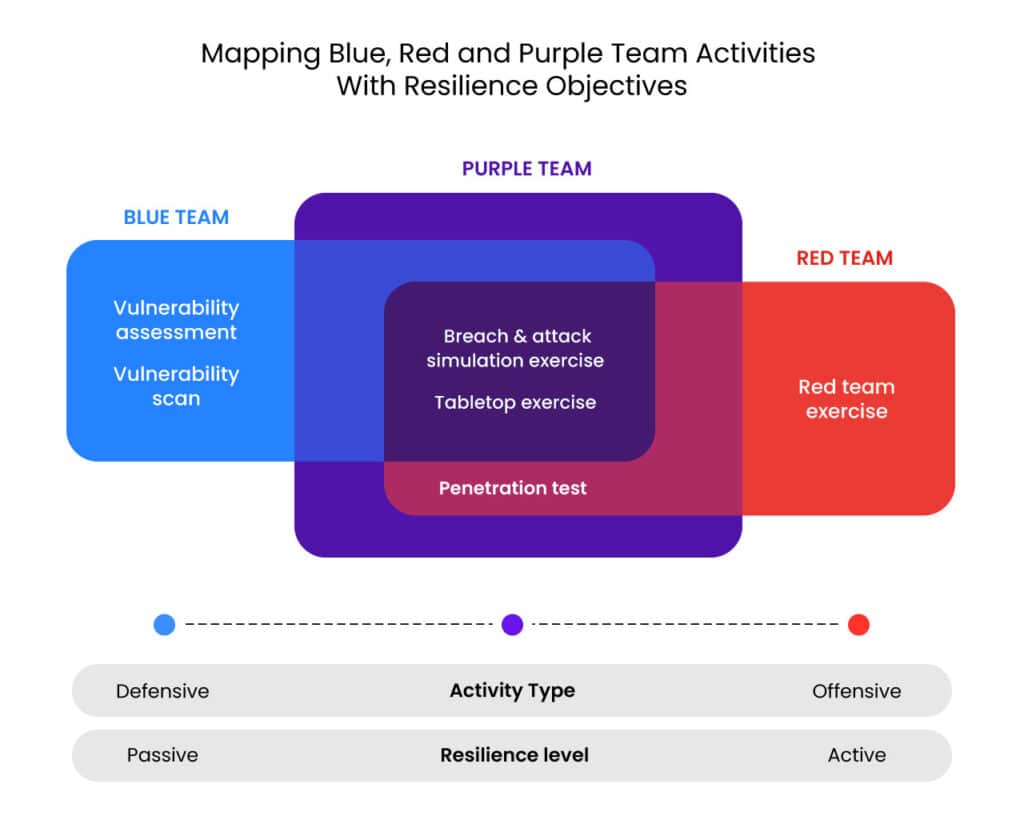
5. Red team and purple team activities
Organizations with a more mature cybersecurity infrastructure and in-house advanced security teams may want to conduct sophisticated adversarial simulations that would be too risky for real red team engagement. BAS supports activities like red team operations and purple team exercises, fostering collaboration between offensive and defensive teams to identify and address vulnerabilities effectively. These simulations incorporate advanced techniques like anti-forensics and defense evasion without jeopardizing production environments.
BAS frees up red teams to focus on high-quality assignments and enables blue teamers to re-run an assessment following remediation.
How it works: BAS gives red teams an environment to build template-based or custom scenarios incorporating risky but realistic attacker behaviors. These targeted simulations enable assessing systems’ resilience to cutting-edge techniques, yet without operational risk or impact. This leads to palliating exposure or developing playbooks to accelerate response.
6. Due diligence for mergers & acquisitions
In acquisition scenarios, BAS delivers an efficient way to baseline the security posture and risk level of targets without needing any access to the target’s systems and networks. By running focused BAS assessments pre-acquisition, organizations gain data-driven insights into the cyber risks being inherited through the merger that can inform valuation and security integration planning.
How it works: BAS attack scenarios are configured to simulate attacks against the intended partner or acquisition systems. This resulting quantitative risk assessment informs financial valuation and security integration planning without directly accessing the target’s environment.
7. Assess third-party cyber risk
BAS can perform some level of controlled security assessments of third parties such as suppliers and partners and a more extensive evaluation of the added risks potentially introduced by new suppliers. By providing a non-intrusive way to continuously evaluate security controls, BAS enables transparency into potential vendor risks without compromising sensitive data. BAS assessments can also be ongoing to continuously validate controls as partnerships evolve.
How it works: Depending on the level of authorization obtained from the supplier or partner, either BAS is deployed in an isolated environment mirroring the target vendor infrastructure or attack simulations are launched directly on the vendor or partner production infrastructure to evaluate their cyber-resilience.
Top BAS Capabilities
To find a comprehensive BAS platform, the following elements should be considered:
- Breadth of simulations– BAS tools should include a variety of pre-built templates across at least email and web gateways, web application firewall (WAF), endpoint security, and data exfiltration network, cloud, and more. The larger the library, the more security layers you can validate.
- Customizable attack scenarios – BAS tools should provide the flexibility to create new simulations tailored to your environment and emerging threats.
- Assessment history and mitigation guidance – BAS tools should enable viewing the history of all assessments and drill down further per assessment to access results and remediation guidance.
- MITRE ATT&CK mapping – BAS tools should link findings or remediation guidance to MITRE tactics and techniques for contextual prioritization and insights.
- Automation – Seek BAS solutions with scheduling, workflows, and APIs to enable continuous testing.
- Dynamic dashboards and automated report generation – BAS tools should enable immediate visualization with customizable dashboards and reports.
Best Practices for BAS Implementation and Adoption
Follow these best practices to gain full advantage from your investment in BAS:
- Promote continuity – Position BAS as an ongoing program, not a one-time project. Build it into processes like vulnerability management instead of a separate entity.
- Include executives – Educate leadership on BAS value to secure alignment on objectives and include them in assessments and reporting.
- Leverage actionable insights – Focus on using BAS findings to drive security hygiene improvements. Do not just collect data.
- Promote skill development – Leverage BAS scenarios to train SOC teams through practical lessons on detecting and responding to threats.
BAS solutions empower organizations to validate controls, expose risks, and refine defenses against ever-evolving threats. Following the strategies outlined here will help you maximize their capabilities and business impact.










