External Asset Discovery Overview
As more and more systems evolve to include one or more externally-facing components, unmanaged
assets (such as Shadow IT) can expand external attack surfaces. Ongoing identification of current and
emergent assets that are publicly visible are critical to cybersecurity resilience.
The Cymulate Attack Surface Management solution efficiently identifies and assesses externally-facing assets
for better control and security.
External Asset Discovery Challenges
Asset Inventory
Asset Inventory
Difficulty identifying and tracking assets across on-premise, hybrid, and cloud infrastructure
Device Proliferation
Device Proliferation
Proliferation of unmonitored assets – from legacy infrastructure, to shadow IT, and more
Network Complexity
Network Complexity
Scaling remote operations and distributed computing create network complexity
Risk Context
Risk Context
Evaluation of the intrinsic risk of identified assets can be challenging without context
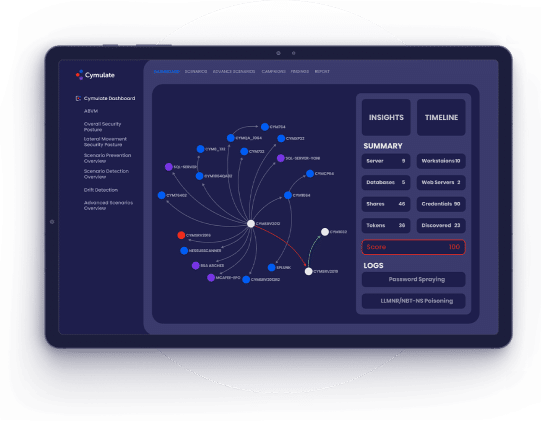
How Cymulate Identifies
Vulnerable Exposed Assets
The Attack Surface Management components of the
Cymulate Platform simulates an extensive set of external
reconnaissance attack phases to identify public-facing assets.
When new assets are identified, a series of non-disruptive
probes and sub-scans determine the susceptibility of that
asset to threat activity.
With appropriate consent, these tools can also be used to scan
third-party tools and systems to evaluate additional areas
of external risk.
How It Works

Dark-Web Compromised User
Information/Credentials

infrastructure
misconfigurations

web applications

party software and indirect
assets (e.g., Shadow IT)
The Benefits of Cymulate External Asset Discovery

Discover
Find exposed assets threat actors may target using the same techniques they would use
Test
Validate discovered assets’ resilience
to attacks and efficacy exposure with compensating controls

Optimize
Prioritize remediation activity according to the potential impact, available controls, and overall scope

Learn More About Cymulate
External Asset Discovery
Solution Validation
Overview of the Cymulate Platform
Attack Surface Management module
Backed By the Industry
“I showed our board of directors the comprehensive visibility that Cymulate provides, and they told me that we needed it before I even had the budget to purchase it.”
Liad Pichon, Director of Cybersecurity, BlueSnap







“Cymulate has been helping me to evaluate my security posture against behavior based as well zero day threats.”
– IT Security & Risk Management Associate

“Technical capabilities provided are outstanding, customer service is highly responsive and product mgmt. is flexible in supporting us with our requests.”
– Security Operations Analyst

“The Cymulate BAS is delivering excellent outcomes, contributing significantly to enhancing my security effectiveness.”
– IT Security & Risk Management Associate

“My experience with the platform was exceptional. It delivers on its promises with easy navigation, effective mitigation steps, and top-notch after sales support.”
– Chief Risk Manager

“Always willing to help offering training sessions and encourage use of the product’s additional available features.”
– Senior Software Engineer

“I believe that Cymulate brings a vision of risks, vulnerabilities and actions that we are unable to pay attention to in our work day.”
– Security Operations Specialist

“The range and breadth of attack scenarios, potential targets and how well each tool integrates is really excellent.”
– Penetration Tester

“We had an excellent experience with Cymulate, from product deployment to while using the platform.”
– Senior Cybersecurity Engineer

“Awesome customer support and techniques used by Cymulate to identify security gaps.”
– IT Security & Risk Management








