Organizations constantly face the question: Can an attacker breach our system? One effective way to find out is through penetration testing. By simulating real-world attacks, pen-testing teams attempt to expose vulnerabilities that could be exploited.
What is Penetration Testing?
Penetration testing, also known as pen testing, is an intentional, systematic process of evaluating an organization’s cybersecurity status by simulating real-world cyber attacks against a computer system, network or web application to identify vulnerabilities that could be exploited by malicious actors.
By imitating the tactics, techniques and procedures (TTPs) of real attackers, organizations can uncover security gaps and weaknesses and provide valuable, data-driven insights before they can be exploited.
The penetration testing process
Penetration tests are usually goal-based, where the testers are trying to get from point A to B within the organizations security systems. They can be performed on networks, systems or even people (known as social engineering) to identify security vulnerabilities that could be exploited by real attackers.
Pen testing is conducted by human testers (in-house or outsourced) who attempt to evaluate the security of an organization’s infrastructure by safely exploiting vulnerabilities. Those vulnerabilities may be present in operating systems, services, or applications, resulting from faulty configuration or caused by careless end-user behavior. In other words, the corporate network, application, devices, and/or people are attacked to check whether a cyber-attacker would be able to penetrate the organization. The tests reveal how deep an attacker could penetrate, and if the attack payload could be executed, i.e., data exfiltration, file or system encryption, infrastructure disablement or destruction.
Penetration testing procedures typically follow a structured approach, such as the structure outlined below. By following this framework, you can help ensure thorough and consistent assessments, meeting and exceeding the goal of improving your security posture:
- Planning and Scoping: Define the scope of the test, including the systems to be tested, the testing methods and the timeline.
- Information Gathering: Collect information about the target environment to identify potential entry points. This can include domain names, IP addresses and organizational structure.
- Vulnerability Assessment: Use automated tools and manual techniques to identify vulnerabilities within the target systems.
- Exploitation: Attempt to exploit the identified vulnerabilities to determine how deep an attacker could penetrate the system.
- Post-Exploitation: Assess the impact of successful exploitation, including data access and system control.
- Reporting: Document findings, detailing vulnerabilities discovered, the methods used and recommendations for remediation.
Manual Penetration Testing vs Automated Penetration Testing
Manual Penetration Testing involves skilled security professionals actively probing systems for weaknesses. These experts bring a human element, allowing them to think like real-world attackers, uncover nuanced vulnerabilities, and exploit complex issues like business logic flaws or social engineering opportunities. However, manual testing is time-intensive and typically performed on a periodic basis, meaning it may not always catch emerging threats or evolving attack vectors.
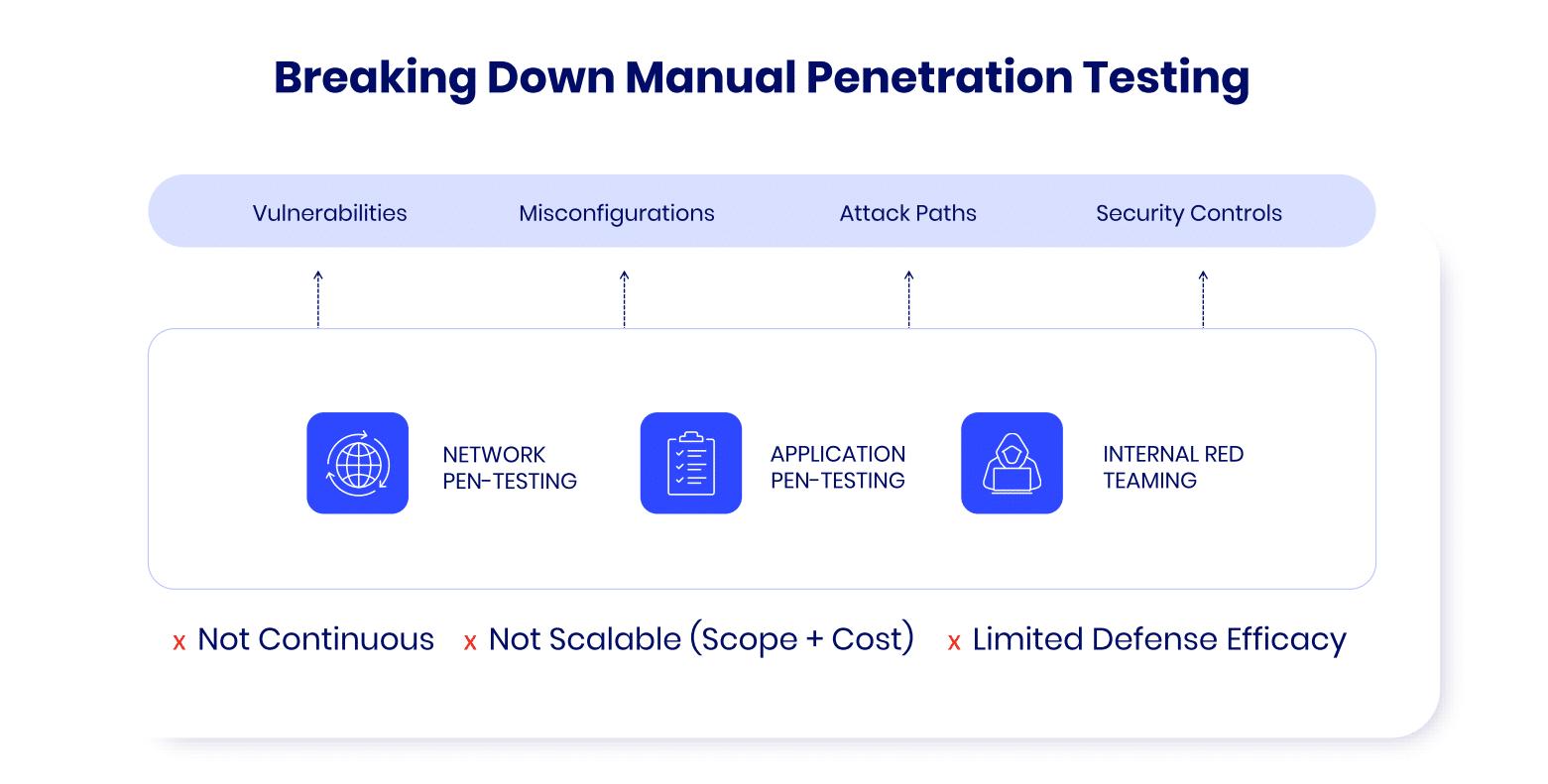
Automated penetration tests assist in identifying vulnerable or high-risk pathways into an environment more quickly. They can emulate multiple threat actor techniques and even different payloads, but they typically don’t replicate and fully automate the full TTPs of a real threat actor, so the environment could still be vulnerable to threat variants or highly expert attackers.
Automated penetration tests also still rely on skilled human pen-testers, whose expertise can vary widely, making it difficult to gain consistent data over time or across all controls in your environment. Even with automation, pen testing takes time to scope, conduct and analyze, slowing your ability to respond accurately to current threats.
These tools also tend to be weak at recognizing vulnerabilities in business logic, which can skew results. In addition, automated tools tend to generate more false positive alerts, which then require human investigation and analysis. Therefore, it’s crucial for cybersecurity teams to choose the right automated penetration testing tools to gain actionable data.
What are the three types of penetration test?
What is shared ahead of an engagement can have the biggest impact on the outcome. That all depends on how much access the tester has to the target environment, which is how we’ve come to classify penetration testing into three main types based on the level of accessible knowledge: black box, whitebox and grey box.
Black box
Starting with the level where the tester (or threat actor) has no prior knowledge of the target environment and must figure out the organization’s weaknesses using publicly available information. The black box level is costly both in time, resources and money, however, it also most closely represents a real-life scenario. The level also can leave much to be desired for a penetration tester, as it may not uncover all vulnerabilities due to the lack of insider knowledge.
White box
In contradiction to the black box, the white box offers the penetration tester full knowledge and access of the target environment, including network and system information, network maps and credentials. This full knowledge, in comparison to the black box, is a major time-saver and reduces overall costs of an engagement. A white-box penetration test allows for a more thorough and efficient assessment, however, may not as accurately represent a real-life attack.
Grey box
The grey box of penetration testing is exactly what you would expect, the middle ground of both the black- and white-box approaches. In this testing scenario, the penetration tester has limited knowledge of the target environment, usually in the form of login credentials, and may have some access to internal documentation. Grey-box testing hopes to achieve the efficiencies of white-box testing while accomplishing the realistic cyber threat black-box testing.
Various Penetration Testing Methods: From Networks to Social Engineering
Penetration testing can be categorized into several types, each focusing on different aspects of security:
- Network Penetration Testing: This involves testing the security of an organization’s internal and external networks. The goal is to identify vulnerabilities in network devices, firewalls and servers.
- Web Application Penetration Testing: Focused on web applications, this type of testing seeks to find security flaws such as SQL injection, cross-site scripting (XSS) and insecure API endpoints.
- Mobile Application Penetration Testing: With the rise of mobile apps, this type targets mobile platforms to find vulnerabilities in mobile applications.
- Social Engineering Testing: This method tests the human element of security by attempting to manipulate employees into revealing confidential information or granting access to secure areas.
- Physical Penetration Testing: This involves testing the physical security of a facility, evaluating how easily an attacker could gain unauthorized access.
- Cloud Security Penetration Testing: Focuses on cloud environments and services, examining configurations and vulnerabilities specific to cloud infrastructures.
- Red Teaming: A comprehensive approach where a team simulates a real-world attack, combining multiple attack vectors to assess the organization’s overall security posture.
- Wireless Network Penetration Testing: Assesses the security of wireless networks to identify vulnerabilities in wireless protocols, encryption and configurations.
Pros and Cons of Penetration Testing
Even with security control validation options, the more traditional approach of penetration testing offers advantages for organizations, though there are some significant weaknesses one needs to be aware of. Below is a breakdown of the benefits and challenges of penetration testing, helping organizations make informed decisions about its role in their security approach.
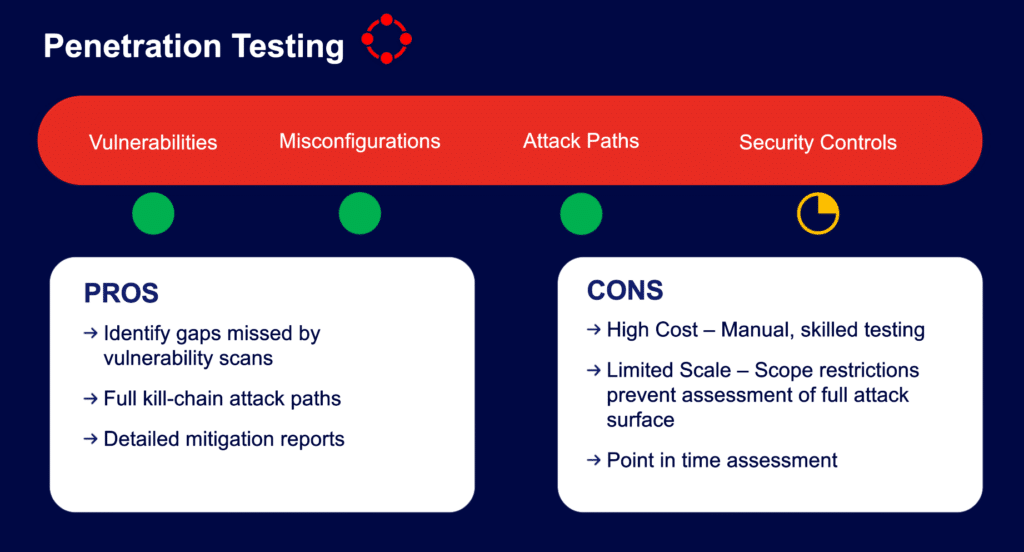
Benefits
Identifies vulnerabilities: Penetration testing uncovers weaknesses that attackers could exploit, giving organizations a chance to address them proactively.
- Strengthens security posture: By exposing security gaps, organizations can improve their defenses before real-world threats emerge.
- Supports compliance: Many regulations require regular security assessments, and penetration testing helps organizations meet these compliance standards.
- Boosts security awareness: Educates employees about potential threats and reinforces the importance of adhering to security protocols.
- Builds customer trust: Demonstrates a commitment to security, enhancing customer confidence and improving brand reputation.
Challenges
- Expensive: Penetration testing is often expensive and resource-intensive, making it less accessible for smaller organizations.
- Snapshot in time: Penetration tests only provide insights at a specific moment, leaving gaps in continuous security monitoring.
- Time-consuming: Preparing, executing and reporting on penetration tests takes significant time, potentially delaying immediate remediation.
- Resource strain: In-house red teams may spend more time on repetitive tasks and administrative duties, limiting their ability to focus on advanced attack simulations.
- Team misalignment: Lack of collaboration between red and blue teams can lead to delays in remediation and inconsistent threat responses.
- Increased time on reports: Red teams often spend a large portion of their time generating reports, reducing their capacity for creating sophisticated attack scenarios.
Do you need Security Control Validation or Penetration Testing?
With the transformational shift towards security control validation, both penetration testing and security control validation are must-have methods to have in place in cybersecurity assurance strategies. Security control validation aims to ensure that controls like firewalls, access controls or intrusion detection systems are functioning as intended. It verifies whether these controls can effectively mitigate identified risks and comply with established security policies and standards.
Security control validation offers verification of the effectiveness of existing controls, while penetration testing seeks to uncover vulnerabilities that could be exploited by attackers. With structured assessments, such as audits or compliance checks, security control validation makes conducting interviews and performing configuration checks a breeze.
Security control validation assessments are often performed regularly and can be done on an automated schedule as part of compliance or risk management practices.

Key Takeaways
Penetration testing is a critical component of having a robust cybersecurity strategy. By proactively identifying and addressing vulnerabilities, your organization can significantly reduce their risk of a potential cyberattack. With the constant evolution of threats, staying vigilant through regular testing and assessments is imperative.
Cymulate provides red teams a platform to increase their operational efficiency and scale their adversarial activities in a production-safe environment. Assessments are easily customized, automated and scheduled. Blue teams that want to run offensive campaigns can also benefit from these capabilities with easy-to-use, out-of-the-box assessments.
To learn more, schedule a demo today.










