The Challenge: Optimizing Security Investments
Security and risk leaders lack KPIs and data to quantify the effectiveness of their cybersecurity strategy and optimize current investments. Disparate tools and passive approaches to risk management lack concrete actionable data for leadership to understand the status of their security posture:
- Can anyone breach the organization and what harm can they cause?
- Is the security team continuously optimizing security controls so that no new threats can get through?
- Is the security team nimble enough to support new business initiatives?
The Solution
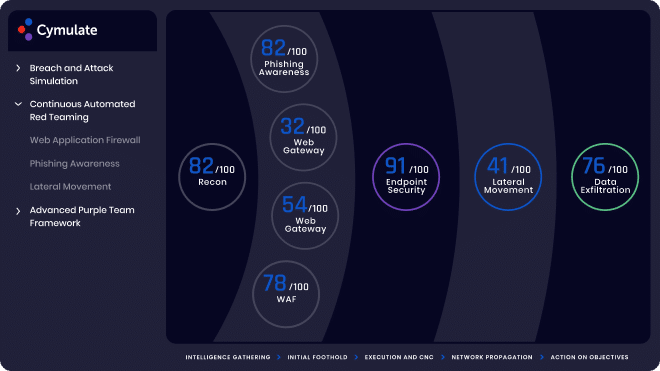
Cymulate Exposure Management and Security Validation helps security leaders take a proactive approach to their security strategy by continuously challenging, assessing, and optimizing security controls across the full cyber kill chain. Automation of the security assurance process and streamlining the influx of information from simulated attacks enables leaders to establish an enterprise-wide security baseline and continuously maximize their security posture, assure improved effectiveness, and prevent security drift.
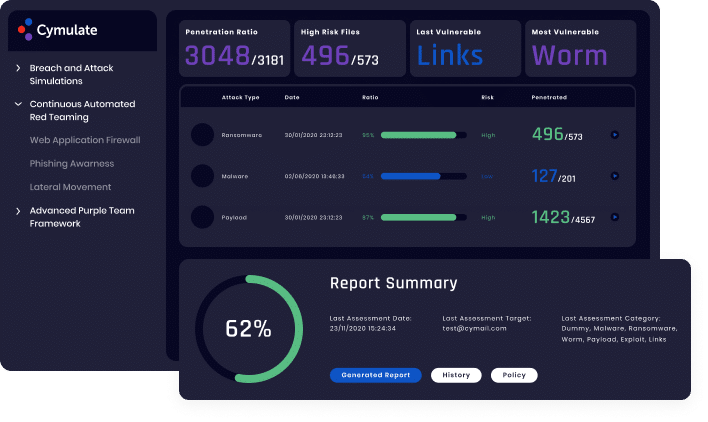
Customizable dynamic dashboards provide an at-a-glance understanding of an organization’s security posture. Visualizing security controls efficacy in a local context focuses mitigation efforts, prioritizes workloads, and prevents security drift. The data that Cymulate provides leaders allows them to immediately understand the effectiveness of their security strategy and the best way to optimize their investments for improved security posture.
Benefits

End-to-End Baselining and Trending

Customizable Reports and Dashboards

Prevent Environmental Security Drift
Related Resources
Simply Know
Control and assure the security posture
of your organization with the most
comprehensive Extended Security Posture Management platform.
More Solutions
Learn how Cymulate makes it easy to keep all angles of your company safe and secure.

SIEM Validation
Optimized SIEM Performance
with enhance detection and
reduced false positives

Mergers and Acquisitions
Comprehensive M&A security posture analysis of planned acquisitions

Operationalizing Threat Intelligence
Continuously updated emerging threats resilience evaluation

Cloud Security Validation
Continuous cloud security control validation and mitigation optimization

Attack Surface Management
Continuous Security Validation with 360°
exposure visibility, comprehensive
threat vector identification
and resilience scoring

Attack Based Vulnerability Prioritization
Data backed optimized mitigation prioritization