Solutions

Challenge
Endpoint security efficacy against a vast myriad of ATT&CK technique implementations and attack scenarios such as ransomware, worms and trojans.

Assess
Endpoint Point Protection (EPP) and Endpoint Detection and Response (EDR) efficacy.

Optimize
Signature and behavioral based endpoint security efficacy.
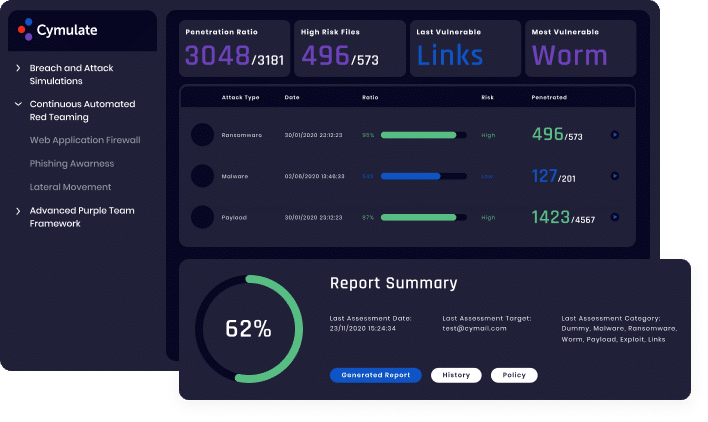
Benefits
Validate the effectiveness of your endpoint security against
threat evolutions.
- Track EDR effectiveness over time and prevent security drift
- Find, prioritize, and fix security gaps against an exhaustive and continuously updated library of attacks
- Benchmark your endpoint security performance against industry peers
- Safe to run in production
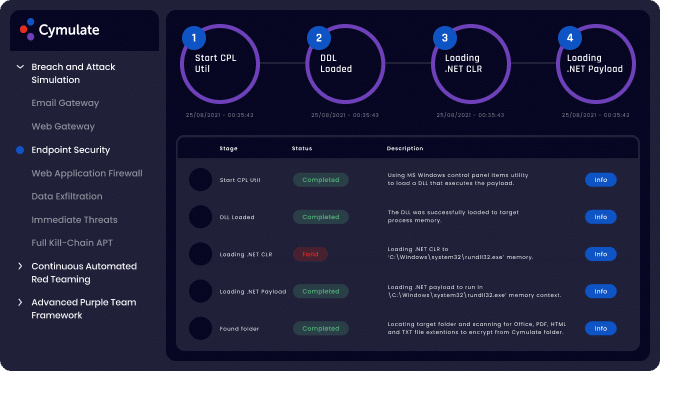
Endpoint Security Vector
The Endpoint Security vector challenges your endpoint security controls and checks whether they are properly tuned to defend against signature and behavior-based attacks. Endpoint security is critical to an organizations capability to prevent and detect malicious behaviors and threats. Organizations protect their endpoints with layers of defense such as antivirus, anti-spyware and behavioral detection solutions. They even deploy highly sophisticated deception systems to lead attackers away from the real endpoints and lure them to honeypots and traps.
Cymulate’s Endpoint Security vector allows organizations to deploy and run simulations of full attack scenario’s e.g. ransomware or implementation of MITRE ATT&CK TTPs on a dedicated endpoint in a controlled and safe manner, comprehensive testing that covers all aspects of endpoint security.
Learn More
More Attack Vectors and Modules

Immediate threats
Validate your defenses against the latest cyber-attacks found in the wild, updated daily.

Full Kill Chain APT
Validate your defenses against APT attack scenarios e.g., Fin8, APT38, Lazarus and custom scenarios.

Web App Firewall
Validate your defenses against web application attacks, including OWASP top ten.

Web Gateway
Validate your defenses against malicious inbound and outbound web browsing and command and control.

Email Gateway
Validate your defenses against thousands of malicious email constructs, attachments, and links.

Lateral Movement
From an initial foothold propagate within the network to find critical assets.

Data Exfiltration
Validate that sensitive and critical data cannot be exfiltrated from the organization.