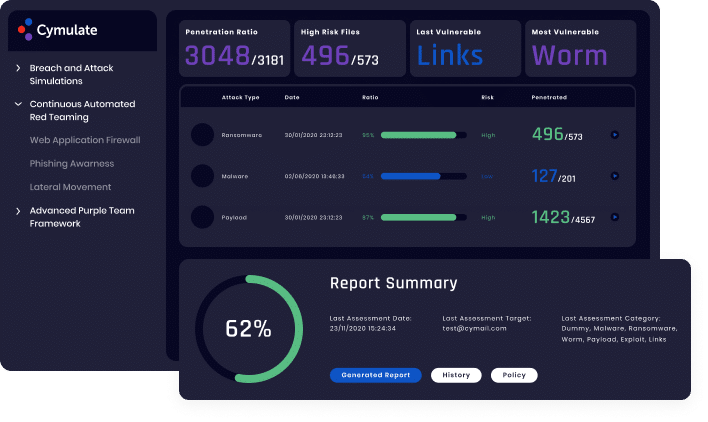
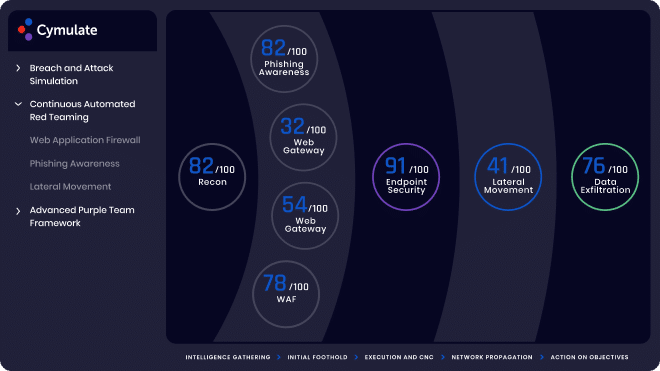
The Challenge: Protecting Against Emerging Threats
With new threats emerging daily, companies should continuously evaluate how well their cyber defenses stack up against them. Knowing with a reasonable degree of certainty that compensating controls provide effective protection if a vulnerability is exploited is critical to maintaining a security posture. However, research about new indicators of compromise (IOCs) and Tactics, Techniques, and Procedures (TTPs) takes up a lot of time and resources, as well as the work that goes into constructing simulated threats and launching them safely in a company’s environment.
The Solution
Cymulate automates threat intelligence-led testing with its Immediate Threats Intelligence module. Updated daily with new threat assessments, Cymulate safely deploys these simulations in a company’s production environment to validate its defenses and if it is effectively protected against the latest threats found in the wild. Cymulate also provides actionable remediation guidance to close security gaps created by the new threat. Organizations can prioritize patching and remediation by knowing which vulnerabilities can be exploited by the new threat and which machines are affected in their environment.
Benefits

Immediate Insights

Mitigation Prioritization

Increase Efficiency
Learn More
Simply Know
Control and assure the security posture
of your organization with the most
comprehensive Extended Security Posture Management platform.
More Solutions
Learn how Cymulate makes it easy to keep all angles of your company safe and secure.

Security Control Validation
Comprehensive SIEM/SOC and IR assessment with many scenarios permutations

SIEM Validation
Optimized SIEM Performance
with enhance detection and
reduced false positives

Mergers and Acquisitions
Comprehensive M&A security posture analysis of planned acquisitions

Cloud Security Validation
Continuous cloud security control validation and mitigation optimization

Attack Surface Management
Continuous Security Validation with 360°
exposure visibility, comprehensive
threat vector identification
and resilience scoring

Attack Based Vulnerability Prioritization
Data backed optimized mitigation prioritization

SOC and SOAR Validation
End-to-end threat detection and IR playbook optimization through comprehensive automated continuous security validation