The Challenge: Difficulty Validating Network Segmentation
An organization may segment its different networks to control the flow of traffic, but a misconfiguration or security drift can still leave it vulnerable to an unauthorized user moving laterally within the networks. This can result in exfiltrating highly confidential information or the activation of ransomware.
The Solution
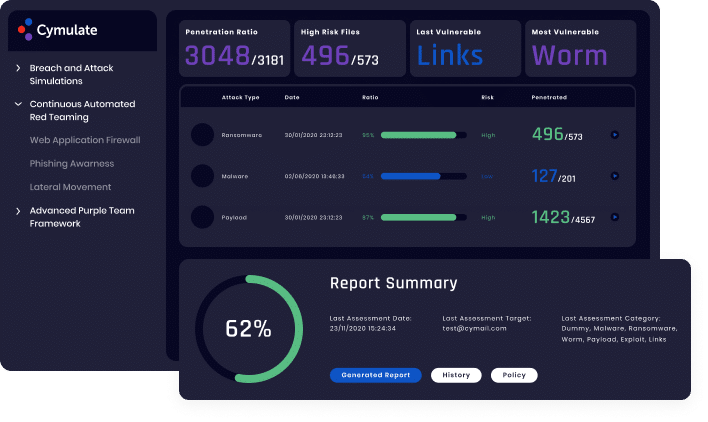
In the case of network segmentation, Cymulate enables continuous validation of the efficacy of security policies for separate units within the same company.
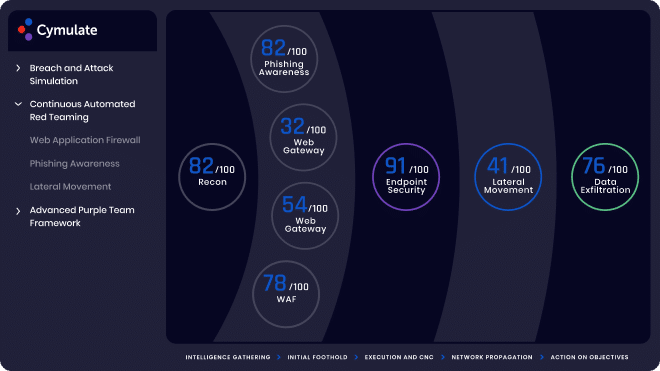
For companies with a complex infrastructure, Cymulate helps ensure that there is no opportunity for lateral movement between networks. The platform continuously discovers discrepancies and provides remediation guidance so that organizations can reduce risk by closing gaps and preventing security drift.
Benefits

Segmentation Policy Validation

Lateral Movement Insights

Prevent Security Drift
Related Resources
Simply Know
Control and assure the security posture
of your organization with the most
comprehensive Extended Security Posture Management platform.
More Solutions
Learn how Cymulate makes it easy to keep all angles of your company safe and secure.

SIEM Validation
Optimized SIEM Performance
with enhance detection and
reduced false positives

Mergers and Acquisitions
Comprehensive M&A security posture analysis of planned acquisitions

Operationalizing Threat Intelligence
Continuously updated emerging threats resilience evaluation

Cloud Security Validation
Continuous cloud security control validation and mitigation optimization

Attack Surface Management
Continuous Security Validation with 360°
exposure visibility, comprehensive
threat vector identification
and resilience scoring

Attack Based Vulnerability Prioritization
Data backed optimized mitigation prioritization

SOC and SOAR Validation
End-to-end threat detection and IR playbook optimization through comprehensive automated continuous security validation